By the Numbers
Since .ODIN came to our attention, G DATA has been monitoring its activity in the wild. Based on the statistical data that we have gathered, .ODIN was very rampant in European region especially in countries like Germany and Netherlands mostly targeting business-to-business (B2B) companies.
Within G DATA’s customer base, the proliferation of .ODIN detections happened a few weeks after its reported release in the wild. The rate of novel infection attempts was decreased after the release of the next two Locky variants.
The Two Copycats
Locky was on a rampage again by releasing two more consecutive variants last October. An unpleasant .SH*T variant was deployed around third week of last month followed by .THOR variant few days after. There were no notable feature differences found among the last three variants except for the obviously new file extension.
The way the recent Locky variants work has not changed, yet. Its distribution method still relies mostly through Nuclear Exploit Kit which uses compromised websites; and the technique on infecting their victims and dropping of payloads remain the same. However, there are recent indications regarding a high possibility of Locky adapting to a different distribution and execution technology.
Recently, a new Dridex campaign was seen utilizing an established and effective method of using PowerShell command by exploiting the known LNK vulnerability. Locky is now expected to move away momentarily from using malicious script attachments in its spam campaign to evade detection. According to Microsoft’s recent technical blog, “the Locky ransomware writers, possibly upon seeing that some emails are being proactively blocked”, could have prompted the change in tactic. Few cases were seen tied to .ODIN but none so far for the latest Locky variants.
New Locky variants are executed the same way as .ODIN. They both use legitimate Windows program RUNDLL32.EXE using the following command line:
Rundll32.exe %TEMP%\[dll_name].dll,<pre-defined text argument>
Notice the shift of using a more flexible argument string that is usually pre-defined within Locky’s script component. It should be noted that the infection routine will not pursue without specifying the required command argument.
Both Locky variants follows the .ODIN’s naming format for the encrypted files:
[generated_unique_id]-[file_hash_identifier].[Locky_ext_name]
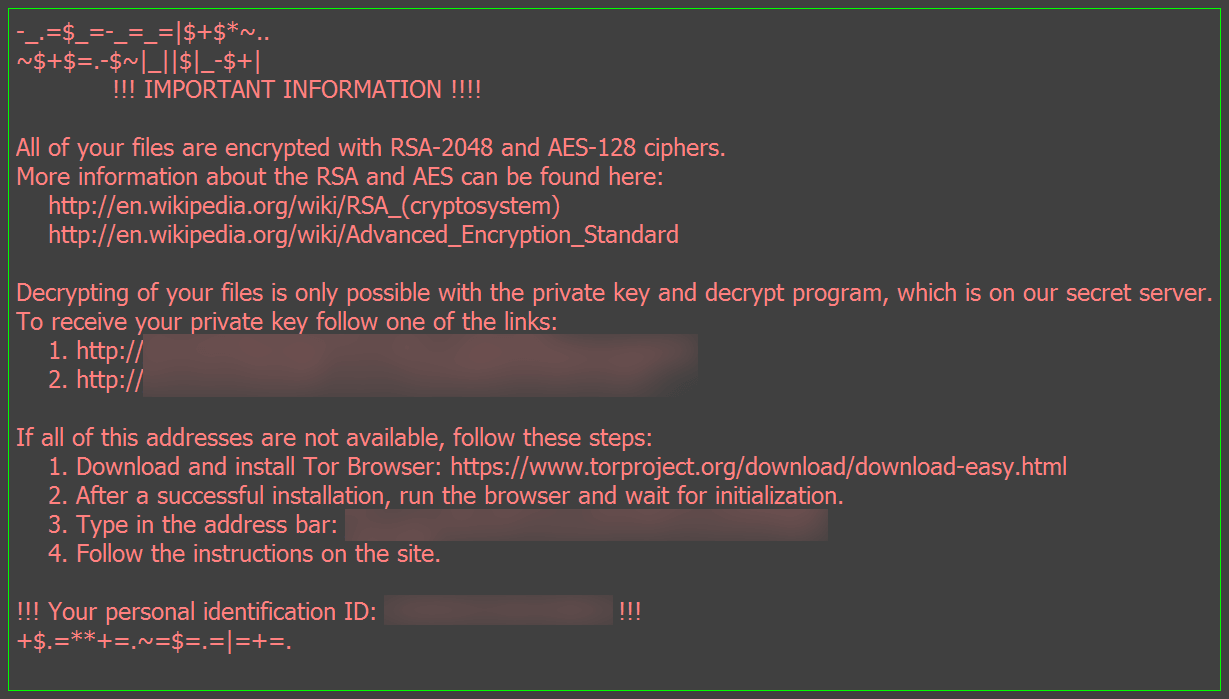
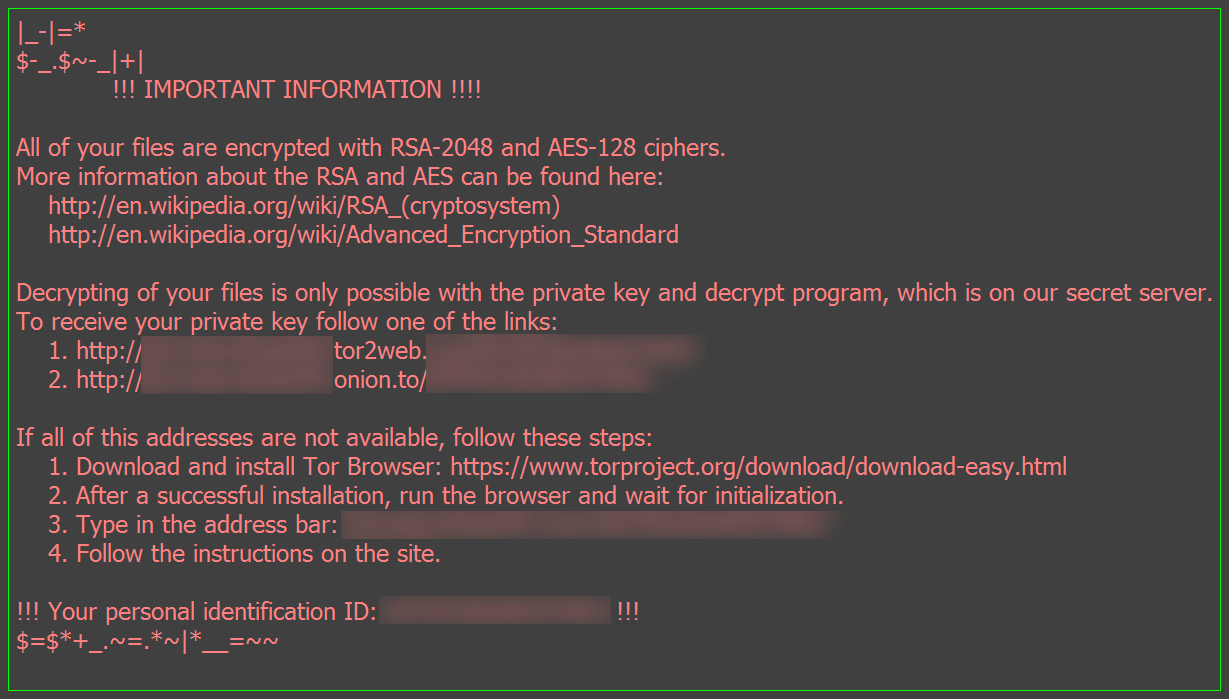
It also drops ransom notes on every affected location to inform the user about the infection.
- [AFFECTED_LOCATION]\_{NUMBER}_HOWDO_text.html
- %DESKTOP%\_HOWDO_text.html
- %DESKTOP%\_HOWDO_text.bmp
After its encryption routine, it executes the following command line to delete the system’s Shadow Volume Copies so it will be impossible for the affected user to recover their encrypted personal files:
VSSADMIN.EXE Delete Shadows /Quiet /All
To complete the infection, both variants communicate to its CnC servers by accessing the following server file:
/linuxsucks.php
It was seen connecting on the following IP addresses
| SH*T | .THOR | ||
| 109.234.35.215 | 51.255.107.20 | ||
| 91.200.14.124 | 194.1.239.152 | ||
| 185.102.136.77 | 194.28.87.26 |
Information about these IP addresses reveals concentration of its server locations:
IP Address: 109.234.35.215
ASN: AS35415 WEBZILLA, NL (registered Aug 03, 2005)
IP Location: Russian Federation Moscow Mchost.ru
IP Address: 91.200.14.124
IP Location: Ukraine Lenina Pp Sks-lugan
ASN: Ukraine AS35804 ALNET-AS, UA (registered Oct 31, 2005)
IP Address: 185.102.136.77
IP Location: Russian Federation Anzhero-sudzhensk Mediaserviceplus Ltd.
ASN: Russian Federation AS43146 AGAVA3, RU (registered Jun 14, 2007)
IP Address: 51.255.107.20
IP Location: France Roubaix Webhost Llc Dmitrii Podelko
ASN: France AS16276 OVH, FR (registered Feb 15, 2001)
IP Address: 194.1.239.152
IP Location: Russian Federation Dmitrov Internet Hosting Ltd
ASN: Russian Federation AS42632 MNOGOBYTE-AS Moscow, Russia, RU (registered Mar 23, 2007)
IP Address: 194.28.87.26
IP Location: Ukraine Kiev Hostpro Ltd.
ASN: Ukraine AS196645 HOSTPRO-AS, UA (registered Jul 29, 2009)
Conclusion
.ODIN continuously hitting the European region since it was released. Statistics show countries like Germany and Netherlands had been the most affected. Few weeks after its released, Locky strikes again with two of its copycats: .SH*T and .THOR. They now join the ranks of other Locky variants that cause damages to millions of users around the world. Though there seem no stark differences from .ODIN, Locky is starting to adopt another malware technology to strengthen its defenses against AV detections.
There is still no available solution to reverse the encryption without paying the ransom. However, it is still highly recommended to recover the files from backup or if lucky, from Shadow Volume Copies if it is still existing in the system.
SHA256 Hashsums
Script Downloader
96e9da900001a628847e722e2b8043a61420010bcc4e0c52b461770059910c84
0866481ac3b6d5e2ebe15969fd0514af41c73de644fb23d60612420aa6bf8a30
.THOR
610e1f5a9386b13cbaac217f05f8089270136ccab00922856fb992eb08a9d12f
b03082c7d72917195ed16061a968547b680f63d0a4463041b14c01c1ee0263ed
.SH*T
695e42426d244733310d4782a5b9f2111e7b48504a89d1ea35ff5180c5f30a05
UPDATE: .AESIR is the new Locky extension (11/22/2016)
New extensions .AESIR attacks
| .1cd | .3dm | .3ds | .3fr | .3g2 | .3gp | .3pr | .7z | .ab4 | .ai | |
| .al | .bz2 | .ce1 | .ce2 | .cr2 | .crt | .cs | .db | .db3 | .dc2 | |
| .fh | .gz | .js | .kc2 | .kdbx | .m3u | .m4a | .m4p | .m4u | .m4v | |
| .md | .mp3 | .mp4 | .muhd | .n64 | .nd | .nk2 | .ns2 | .ns3 | .ns4 | |
| .nx2 | .p12 | .p7b | .p7c | .pl | .ps | .py | .r3d | .rb | .re4 | |
| .rm | .rw2 | .sd0 | .sh | .sr2 | .st4 | .st5 | .st6 | .st7 | .st8 | |
| .vb | .wb2 | .wk1 | .x11 | .x3f | 0.001 | 0.002 | 0.003 | 0.004 | 0.005 | |
| 0.006 | 0.007 | 0.008 | 0.009 | 0.01 | 0.011 | 0.123 | 0.602 |

Encrypted files were renamed with a similar format:
[generated_unique_id]-[ file_hash_identifier].aesir
It drops ransom notes on every affected location to inform the user about the infection:
- [AFFECTED_LOCATION]\-{NUMBER}-INSTRUCTION.html
- %DESKTOP%\-INSTRUCTION.html
- %DESKTOP%\-INSTRUCTION.bmp
SHA256 Hashsums
Locky Script Downloaders:
b101a4cbf461f1e6aca2fc553b4d624e5594fd03850f9a878a8e3eb18e057cc4
23779cacf832a0f266e77dff903d836d9c19a60a720aa932d09627436d5e0b7f
629242f1572848ccb4c0c1e37d7a6cb845959ca2985b365dc2e001579cdc61b9
.AESIR DLL binaries:
ff4a021e6175e5f2c0a666270081d74991c69e651c249a6fdf82a004dd9215e5
b8b79de0c2be90bbf4806016f7bf255f34402f5c9458f6b6c6f2e024798615f1
Complete list of extensions attacked by .AESIR
| .1cd | .3dm | .3ds | .3fr | .3g2 | .3gp | .3pr | .7z | .7zip | .aac | .ab4 | .accdb | .accde | .accdr | .accdt |
| .ach | .acr | .act | .adb | .adp | .ads | .aes | .agdl | .ai | .aiff | .ait | .al | .aoi | .apj | .apk |
| .ARC | .arw | .asc | .asf | .asm | .asp | .aspx | .asset | .asx | .avi | .awg | .back | .backup | .backupdb | .bak |
| .bank | .bat | .bay | .bdb | .bgt | .bik | .bin | .bkp | .blend | .bmp | .bpw | .brd | .bsa | .bz2 | .cdf |
| .cdr | .cdr3 | .cdr4 | .cdr5 | .cdr6 | .cdrw | .cdx | .ce1 | .ce2 | .cer | .cfg | .cgm | .cib | .class | .cls |
| .cmd | .cmt | .config | .contact | .cpi | .cpp | .cr2 | .craw | .crt | .crw | .cs | .csh | .csl | .csr | .css |
| .CSV | .csv | .d3dbsp | .dac | .das | .dat | .db | .db_journal | .db3 | .dbf | .dbx | .dc2 | .dch | .dcr | .dcs |
| .ddd | .ddoc | .ddrw | .dds | .der | .des | .design | .dgc | .dif | .dip | .dit | .djv | .djvu | .dng | .doc |
| .DOC | .docb | .docm | .docx | .DOT | .dot | .dotm | .dotx | .drf | .drw | .dtd | .dwg | .dxb | .dxf | .dxg |
| .edb | .eml | .eps | .erbsql | .erf | .exf | .fdb | .ffd | .fff | .fh | .fhd | .fla | .flac | .flf | .flv |
| .flvv | .forge | .fpx | .frm | .fxg | .gif | .gpg | .gray | .grey | .groups | .gry | .gz | .hbk | .hdd | .hpp |
| .html | .hwp | .ibank | .ibd | .ibz | .idx | .iif | .iiq | .incpas | .indd | .iwi | .jar | .java | .jnt | .jpe |
| .jpeg | .jpg | .js | .kc2 | .kdbx | .kdc | .key | .kpdx | .kwm | .laccdb | .lay | .lay6 | .lbf | .ldf | .lit |
| .litemod | .litesql | .log | .ltx | .lua | .m2ts | .m3u | .m4a | .m4p | .m4u | .m4v | .mapimail | .max | .mbx | .md |
| .mdb | .mdc | .mdf | .mef | .mfw | .mid | .mkv | .mlb | .mml | .mmw | .mny | .moneywell | .mos | .mov | .mp3 |
| .mp4 | .mpeg | .mpg | .mrw | .ms11 | .msg | .muhd | .MYD | .myd | .MYI | .n64 | .nd | .ndd | .ndf | .nef |
| .NEF | .nk2 | .nop | .nrw | .ns2 | .ns3 | .ns4 | .nsd | .nsf | .nsg | .nsh | .nvram | .nwb | .nx2 | .nxl |
| .nyf | .oab | .obj | .odb | .odc | .odf | .odg | .odm | .odp | .ods | .odt | .ogg | .oil | .onetoc2 | .orf |
| .ost | .otg | .oth | .otp | .ots | .ott | .p12 | .p7b | .p7c | .pab | .pages | .PAQ | .pas | .pat | .pcd |
| .pct | .pdb | .pdd | .pef | .pem | .pfx | .php | .pif | .pl | .plc | .plus_ | .png | .pot | .potm | |
| .potx | .ppam | .pps | .ppsm | .ppsx | .PPT | .ppt | .pptm | .pptx | .prf | .ps | .psafe3 | .psd | .pspimage | .pst |
| .ptx | .pwm | .py | .qba | .qbb | .qbm | .qbr | .qbw | .qbx | .qby | .qcow | .qcow2 | .qed | .r3d | .raf |
| .rar | .rat | .raw | .rb | .rdb | .re4 | .rm | .RTF | .rtf | .rvt | .rw2 | .rwl | .rwz | .s3db | .safe |
| .sas7bdat | .sav | .save | .say | .sch | .sd0 | .sda | .sdf | .sh | .sldm | .sldx | .slk | .sql | .SQLite | .SQLITE3 |
| .sqlite3 | .SQLITEDB | .sqlitedb | .sr2 | .srf | .srt | .srw | .st4 | .st5 | .st6 | .st7 | .st8 | .stc | .std | .sti |
| .stm | .stw | .stx | .svg | .swf | .sxc | .sxd | .sxg | .sxi | .sxm | .sxw | .tar | .tbk | .tex | .tga |
| .tgz | .thm | .tif | .tiff | .tlg | .txt | .uop | .uot | .upk | .vb | .vbox | .vbs | .vdi | .vhd | .vhdx |
| .vmdk | .vmsd | .vmx | .vmxf | .vob | .wab | .wad | .wallet | .wav | .wb2 | .wk1 | .wks | .wma | .wmv | .wpd |
| .wps | .x11 | .x3f | .xis | .xla | .xlam | .xlc | .xlk | .xlm | .xlr | .XLS | .xls | .xlsb | .xlsm | .xlsx |
| .xlt | .xltm | .xltx | .xlw | .xml | .ycbcra | .yuv | .zip | 0.001 | 0.002 | 0.003 | 0.004 | 0.005 | 0.006 | 0.007 |
| 0.008 | 0.009 | 0.01 | 0.011 | 0.123 | 0.602 |
UPDATE: Yet another new Locky extension: .zzzzz (11/24/2016)
24-Nov (JST), #Locky spam email, "Attention Required". Encrypted files extension ".zzzzz". No C2 responsed. JS file https://t.co/hFZbecCa3Zpic.twitter.com/eGJQnykjxE
— TMMalAnalyst (@tmmalanalyst) 24. November 2016