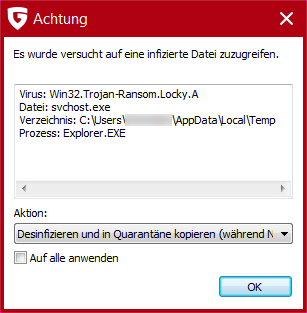
PRIVATE INDIVIDUALS BEING TARGETED
In choosing what to lure people in with, the attackers have focused on the end of the year. They are sending emails in German with supposed messages about possible tax refunds or invoices that are meant to have been discussed back in the middle of the year. All the emails have a very personal tone as they are not emails from fake companies but from supposed acquaintances. The salutations and greetings are intended to suggest a connection between the sender and the recipient. Private individuals are clearly the main targets of the attack, and we can expect further emails of this sort.
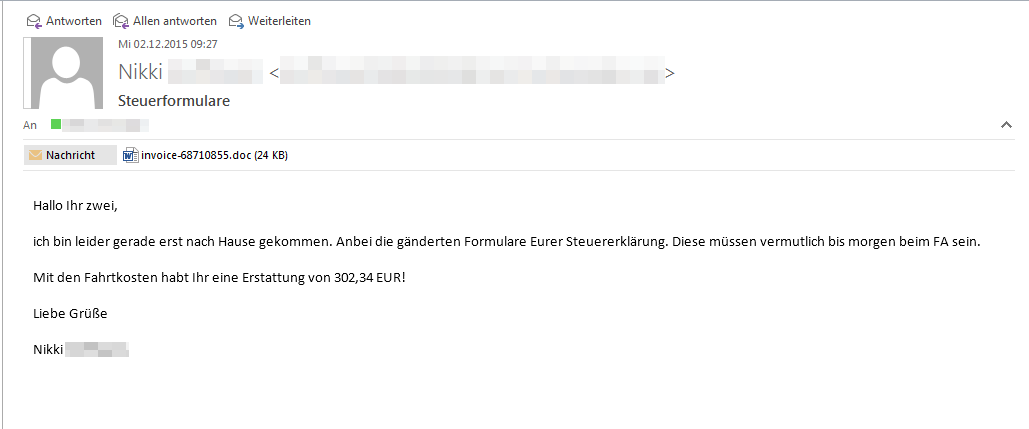
Text in the "Tax Form" email
"Hi Both
Unfortunately I've only just got back. Attached is your amended tax return form. This needs to reach the tax office by tomorrow.
You are due a refund of €302.34 in travel expenses!
Best wishes
<Name of Sender>"
G DATA recognises the primed Word document as W97M.Downloader.AHU (Engine A) and Macro.Trojan-Downloader.Donoff.X (Engine B). The downloaded executable file is identified by the scan engines as Trojan.GenericKD.2905834 (Engine A) or Win32.Trojan-Spy.Dridex.AI (Engine B). Aditionally, G DATA BankGuard technology reliably fends off this malware.
Text in the "Invoice November 2015" email
"Hello
Finally :) Here is the invoice from July. I hope all is well in your studio.
Best wishes
<Name of Sender>"
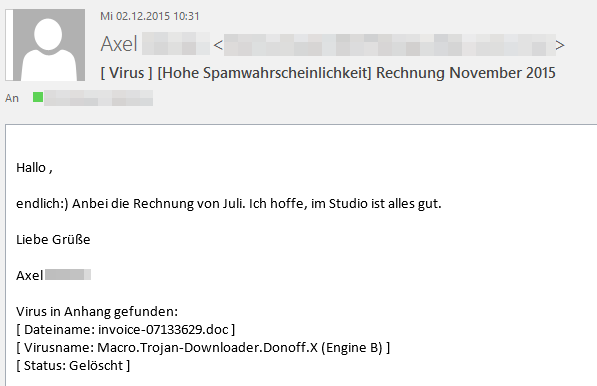
G DATA recognises the primed Word document as W97M.Downloader.AHU (Engine A) and Macro.Trojan-Downloader.Donoff.X (Engine B). The downloaded executable file is identified by the scan engines as Trojan.GenericKD.2905834 (Engine A) or Win32.Trojan-Spy.Dridex.AI (Engine B). Additionally, G DATA BankGuard technology reliably fends off this malware.
BUSINESSES ALSO BEING TARGETED
At the same time, these (or other) attackers are sending out English versions of these emails, imitating the output from network printers. For example: the attacker suggests that the attached document is a printer scan and that it needs to be opened with Microsoft Word. The model name used relates to a multifunction device from the popular brand Sharp. The attackers falsify the name of the sender of the email, so it looks as if the email is coming from the recipient's own/a company –which is clearly not the case!
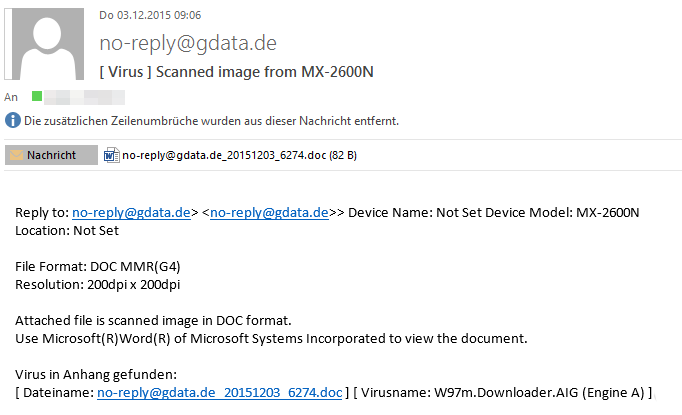
Text of the "Scanned image from MX-2600N" email
"Reply to: <Sender Address>
Device Name: Not Set
Device Model: MX-2600N
Location: Not Set
File Format: DOC MMR(G4)
Resolution: 200dpi x 200dpi
Attached file is scanned image in DOC format.
Use Microsoft(R)Word(R) of Microsoft Systems Incorporated to view the document."
G DATA security solutions recognise the primed document as W97M.Downloader.AIG (Engine A) and Macro.Trojan-Downloader.Dridex.AL (Engine B). The subsequently downloaded file used to infect the PC, Trojan.GenericKD.2852932 (Engine A), is fended off. Additionally, G DATA BankGuard technology reliably fends off this malware.
THE MALWARE ATTACK
The attackers send primed Microsoft Office documents with an embedded macro. As soon as the user opens the document and enables the macro to be executed, a connection is established with a server. An executable file is then downloaded onto the victim's PC from there and run – and so the banking Trojan from the Dridex family gets onto the system.
DRIDEX? BUT PEOPLE WERE ARRESTED FOR THAT!
At the end of August the administrator behind the Dridex malware was arrested on Cyprus. 30-year-old Andrey Ghinkul was said to be one of the leaders behind attacks on the Penneco Oil Company in Pennsylvania in 2012. At the time, they were able to extract over 3.3 million US dollars from the company in multiple stages, reports pcworld.com. The malware is thought to have got hold of some 30.5 million US dollars in the United Kingdom, and the FBI estimates that direct damages of 10 million US dollars in the USA can be attributed to Dridex.
The malware's activities faltered after the arrest, as a coordinated takedown of the servers involved was carried out. But the botnet could not be brought to a halt – as the current wave clearly shows.
HOW TO STAY ON THE SAFE SIDE
"We urge all internet users to take action and update your operating system. Ensure you have up to date security software and think twice before clicking on links or attachments in unsolicited emails," says Executive Assistant Director of the FBI Robert Anderson, making important points as he does so.
An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails is also useful.
We urgently recommend that users never open attachments that they receive from unknown senders. We recommend you to be alert to invoices and the like. You should ask yourself the following questions before opening attachments:
- Have I actually ordered anything? Am I really supposed to have received such an invoice?
- Is the email written in a language that makes sense for me and my situation?
- A German website will most likely send you emails and invoices exclusively in German, not English.
- In relation to the supposed document scans: Do you or does your company own such a device? Would this device be capable of saving documents as .doc files, or rather as images or .pdf files?
- If you are sure that the document is not intended for you, resist the urge to open the document to find out information about somebody else! That is just what the manipulators are counting on. It is also not unusual for attachments to be sent that supposedly contain payroll details.
- Does the email contain personal information such as my correct name, address, customer number, user name or other data? Never thoughtlessly publish your own primary email address online, e.g. in forums and guest books, as it can be accessed by fraudsters there. It is useful to enter a secondary address for these purposes.
- Remember that attackers very frequently use topical subjects to lure potential victims into traps – as is the case here with end-of-year taxes. In the coming spring, in the run-up to the 2016 Football UEFA European Championship, a watchful eye needs to be kept on messages relating to football.
If you have any doubts, do not open the attachment! We urgently recommend that you never enable macros in documents from an unknown source.