Tried and tested infection vector
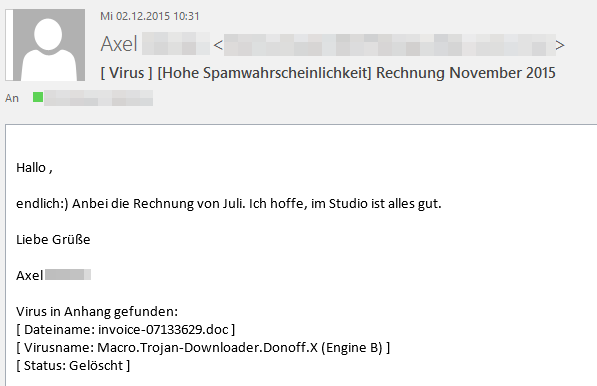
While Dridex's main monetarization vector remains unchanged, the criminals behind the recent campaigns not only changed the implementation of the first stage, they also upped their phishing game: We have received a phishing email sample very recently which at first glance looked like a targeted attack against a user / organization.
At a second glace, however, the email is pretty generic, but in any case very well written. It turned out to be an example for a current campaign looking to spread malware, in this case, Dridex, via spam emails. As in earlier cases, Dridex is being delivered via a malicious word document attached to phishing emails. Those campaigns used a password protected attachment to evade detection and automated processing of the sample. This time, it is just a plain DOC file.
Downloading & running the payload
What is interesting about the word document attachment is that it does not contain any VBA macro code. Instead, it has a malicious VBS script (posing as another document) embedded in the document. The phishing technique uses social engineering to trick the user into opening the fake document to view its content. Once user falls for the trap and opens the VBS file, the malware will then start executing a PowerShell script. This VBS script uses codes that leverage the use of PowerShell commands. These commands are responsible for downloading and running the payload. PowerShell scripting became popular when the ‘Poweliks’ malware was discovered.
The Dridex payload will start the program spoolsv.exe and injects itself into this process. It will then connects to its first stage command and control server to request additional data and further instructions. Those instructions also tell Dridex on which banking website it should catch the credentials and other data. Subsequently, it injects itself into the process of popular browsers and waits for the user to visit the banking site Dridex was primed to monitor. G DATA’s BankGuard technology is able to detect and prevent further damage of Trojan-Spy Dridex. Bankguard technology focuses on banking spy malware and capable of identifying malicious transaction for most of banking Trojan.
Conclusion
While ransomware has taken center stage in terms of public attention to current threats, many other types of malwares are still flying 'under the radar', pretty much roaming freely, infecting and spreading without being noticed. Even though some news reports claim that members of the Dridex gang were arrested, their succession is secured. Others will pick up where the arrested individuals left off and continue the work; the arrested were part of the lower tier of the entire operation. While the overall number of infections with Locky is gradually falling, we are seeing Dridex slowly rising from what was perceived (for a while, anyway) as being his grave.
IoC list & information for fellow researchers
Email attachments:
fb9b5b2dd1c29724536ee1fc24372c4f24dfc5659a191600f668c29b46bb0bb2
e164bffc3b03e137e936c7b5848764605d72570ee9fbfa55f9d5e8ef33eb562b
5f35c98eb9256dbae88a97ddffa9df21619fe130fcac5c9707fbb7925cd87291
Embedded VBS script:
b77a8fa6084e33a5d842dc02fd804a3edee92234affa5e244f25004e340f21e9
425231f38d5348cafee7666dff5e47d2ae5a076ae10aac95b0cfc639eb9580fe
e6f2cd2f7d93551274930bd8be1f47546d5e5e9dd183f46d986f1aed27eee3a4
Known landing pages for payload download:
hotel[.]gruyereshotels[.]ch/jobs/pharmacy/list.php
swiss[.]chevaliers-gruyeres[.]ch/jobs/pharmacy/list.php
chalet[.]hoteldegruyeres[.]ch/jobs/pharmacy/list.php
Dridex Payload:
ecb9405883c2c865ea7cbddf5035cfe461e35b96069d6683b0744340eca239fe
C2 server (stage 1):
85[.]25[.]203[.]43:53443