The email
It should be noted that there are two different aspects to this email, depending on whether the potential victim views it as text-only or as an HTML version. The screenshots show the difference:
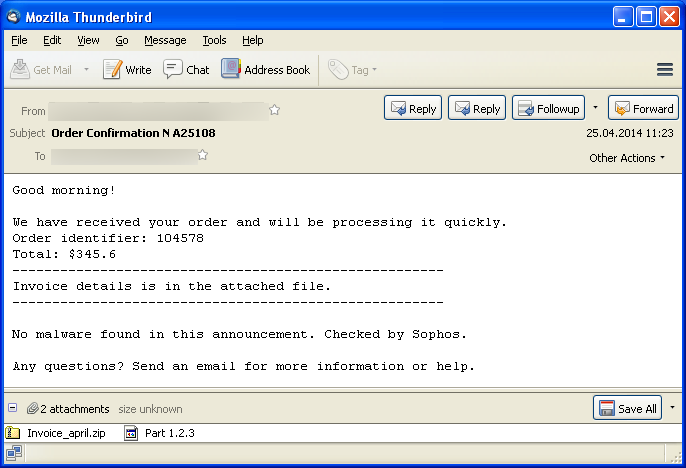

The text-only version of the email suggests that the email has been checked by Sophos:
"No malware found in this announcement. Checked by Sophos."
The HTML version, on the other hand, is supposed to be safe following a check by G Data:
"No virus found in this notification. Checked by G Data."
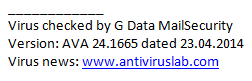
The original message that recipients see when an email has been successfully scanned by a G Data security solution (and the option to show information has been enabled) looks like this:
However, both versions of the fraudulent email are attempting to get the recipients to do the same thing – open the attached file in which the supposed invoice is located. Neither the email text nor the subject line or sender of the email give any indication of what the recipient is actually being invoiced for. This is one way of making the potential victim quite curious, although the situation should make alarm bells ring – no business should (and, we hope, would) be sending invoices to its customers in such an unprofessional way.
The infected attachment
Many users have the file extension display switched off in their system, as this is the default setting for Windows systems. This means that the actual file ending (.scr) for the file within the zip file is hidden from them. .scr files are executable files, and in the current case, double clicking them starts the malware running, not, for example, opening the zip archive, as the name without the file ending (and the icon used) would suggest. G Data security solutions recognise the initial malware file (Invoice_april.zip.scr) as Trojan.GenericKD.1654498.
After running this screensaver file, encrypted code is decrypted in the memory, and this then overwrites the encrypted code. This produces a minimalist downloader, which contacts a predetermined list of URLs again and again, to download a new malware file (an .exe file) from there. As soon as a download from an address is complete, the downloader runs this .exe file on the PC and then shuts itself down.
The .exe file contains code that is decrypted in the same way as the downloader was. However, in this case the decrypted code results in a Trojan horse from the ZeuS family, which in this case involves a variant with Necurs rootkit functionality. The ZeuS malware is identified by G Data security products as Trojan.GenericKD.1655050.
In its SecurityBlog a few days ago, G Data reported on a case involving very similar malware, which was also being distributed by email: Password protection does not automatically mean secured.
Advice
- Email from unknown senders or services and companies you have no affiliation with should be treated with caution! If an email looks strange or foreign: ignore it, delete it, but under no circumstances open attachments or click on URLs.
- Spam emails should never be responded to either. All a response does is indicating to the fraudsters that the address they wrote to is actually valid.
- If you find out that one of your contacts is sending unusual emails or instant messages, contact them – ideally using a different communication channel than the one via which the suspicious message came.
- Using an up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must! A spam filter that protects you from unwanted spam emails obviously also makes sense.
- Make Windows show you the right file extensions. Instructions for the different versions as well as a ‘Fix it’ package are available on the Microsoft website "How to show or hide file name extensions in Windows Explorer".
