Case 1: Phishing campaign
We identified a spam campaign concerning phishing attempts. This campaign currently mainly targets Italian users and in particularly the customers of the bank called Gruppo bancario Iccrea. The purpose of this campaign is to steal credit card information.
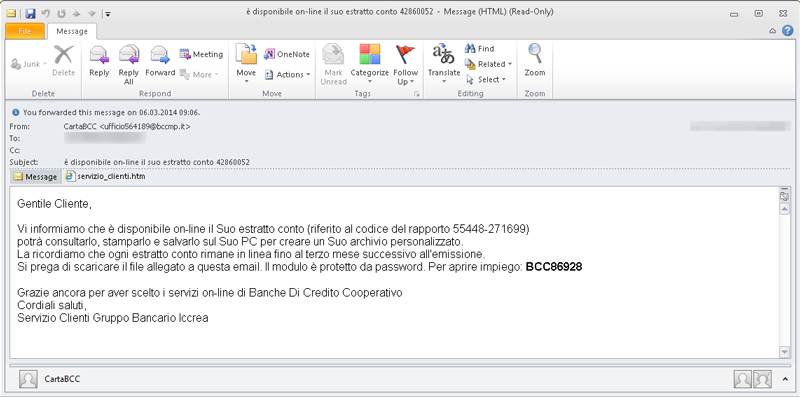
The email has an attachment: a .HTML document which, when opened, asks for a password – the one given in the email text. Note that the window asking for the password is in English language, not in Italian any more.
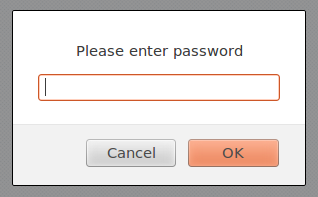
The password is used to decode the payload containing the HTML code of the phishing campaign:
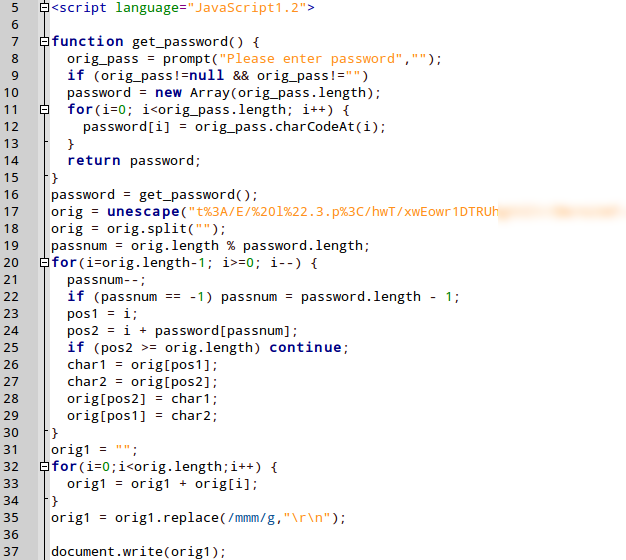
If the entered password is correct, the HTML code contained in the variable called “orig” is decoded and the phishing website is displayed:
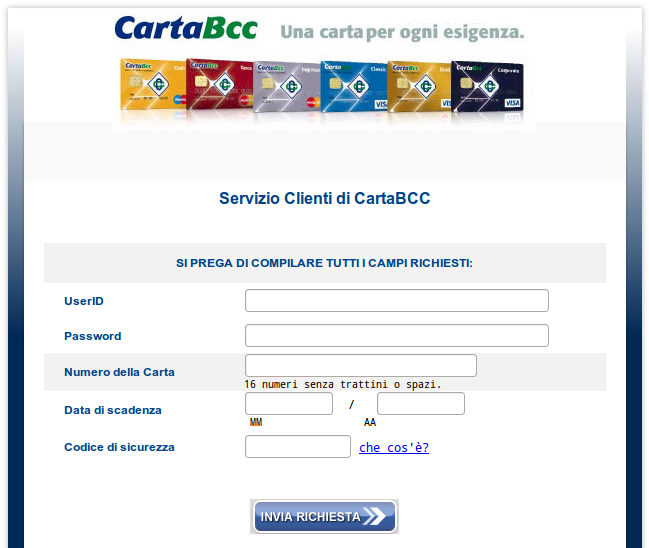
The author of this campaign uses the fact that a password is commonly linked to the lexical field of security: for some people, if something is protected by a password, it is secure. The attackers use this perception to deceive the email readers.
Case 2: Malware campaign
An article on myonlinesecurity.co.uk reported about a similar campaign, involving malware attachments. The attackers use social engineering techniques to lure possible victims into downloading and installing malware.
In addition to this social engineering aspect, the attackers use technical tricks as well. The attachment, a .RAR archive file, is protected by the password mentioned in the email. Password-protected archives cannot be scanned by security suites and therefore can bypass the email security gateways unchecked, though packed with malware. Scanning the content would require automatic unpacking, thus breaking the password protection. This is something no normal email client should do.
Manually unpacking the .RAR archive reveals the malicious content: a file named NIKON-2013564-JPEG.scr, which is detected as Trojan.GenericKD.1604689 by G Data products.
The file extension .SCR informs Windows about this file being an executable. The second extension hint, JPEG, preceding the real extension, makes the user believe he is handling a picture.
By default, Windows does not show the real file extension, so a user would originally not see .scr and the second extension JPEG can be used to cheat. Another level of disguise is the file icon. The file’s icon shows a PDF document.
How the malware works
The attached executable extracts a second binary, called viewer_update.exe, and executes it. This .EXE connects to the Internet and downloads further files:
- hxxp://[DELETED]/images/gombos/13003UKc.ton
- hxxp://[DELETED]/wp-content/uploads/2014/03/13003UKc.ton
These websites seem to be compromised legitimate websites. The file downloaded, 13003UKc.ton, is an encrypted driver which we detect as Generic.Trojan.Agent.BK. After its download, the encrypted driver is decrypted by viewer_update.exe and drops ZeuS malware with Necurs rootkit capabilities onto the victim’s PC. G Data detects this particular sample as Rootkit.Necurs.QC.
Conclusion
Packing malware into password-protected archives and therefore bypassing malware scanners monitoring the email programs is nothing entirely new. It became popular with the Bagle family back in 2003. The purpose by that time was to hinder automatic analysis of the files. But, actually,it didn't take too long to adopt the relevant systems back in 2003. It is rather surprising that attackers start following this strategy again, because it is time consuming for them to realize – compared to other spam methods used. And it doesn't disturb analyses at all. The only effect is that the malicious files are detected a bit later.
As email programs and their standard security measures have their problems with this kind of attack, it is even more important to rely on a comprehensive AV product and first of all, understand the nature of the attack to avoid being trapped!
Some advice you should consider:
- Email from unknown senders or services and companies you have no affiliation with should be treated with caution! If an email looks strange or foreign: ignore it, delete it, but under no circumstances open attachments or click on URLs.
- Spam emails should never be responded to either. All a response does is indicating to the fraudsters that the address they wrote to is actually valid.
- If you find out that one of your contacts is sending unusual emails or instant messages, contact them – ideally using a different communication channel than the one via which the suspicious message came.
- An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must! A spam filter that protects you from unwanted spam emails obviously also makes sense.
- Make Windows show you the right file extensions. Instructions for the different versions as well as a ‘Fix it’ package are available on the Microsoft website "How to show or hide file name extensions in Windows Explorer".
