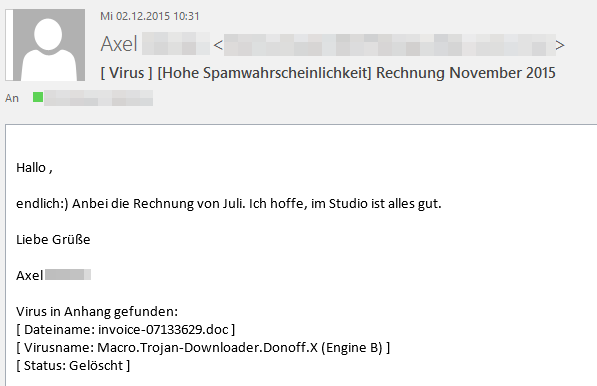
In the first public reports by Telekom in relation to this wave of spam, the malware program in question was assumed to be a Bitcoin miner. This assumption has been corrected with the statement that it is a Trojan horse "the effects of which are as yet unknown".
However, the procedure used in this case reminded the experts at G DATA SecurityLabs of a similar case from January 2014: Cridex banking Trojan on the rise. Even back then, renowned telecommunications companies and banks were used as bait and the procedure was very similar. The malware used is also extremely similar to that used in the previous case. While banking Trojan Cridex was spread back then, the current malware has now been identified as its successor and named Swatbanker.
Compared to other banking Trojans, Swatbanker gained notoriety within a very short space of time. Here's an overview of the attacks that BankGuard detected in the month of May:
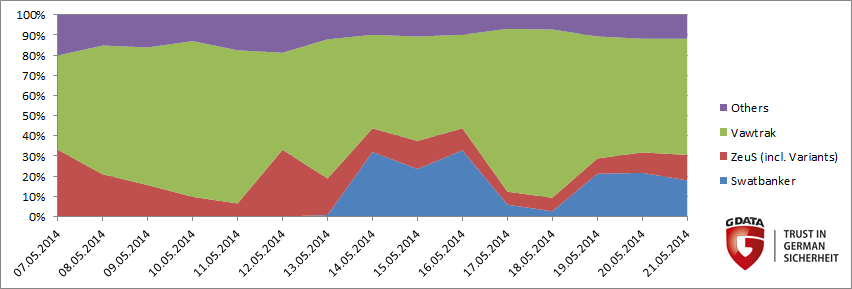
Malware: Swatbanker, a Cridex successor
Significant similarities in the protocol
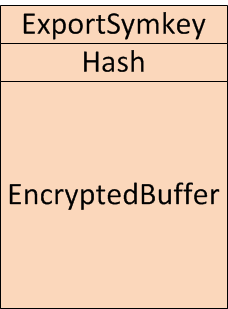
The binary files differ so greatly that it must be assumed that the actual malware was programmed from scratch. However, there are some obvious similarities in the protocol. Both variants use the same scheme for sending stolen data to a server controlled by the attackers, the so-called drop zone:
All this data is sent using the HTTP protocol. First, plain text data is used to form a checksum using the hash function SHA1 (Hash). The stolen plain text data is then symmetrically encoded using a key, which the software always generates anew and randomly (EncryptedBuffer). RC4 is used as the encryption procedure. The RC4 key is then encoded asymmetrically using a public key from a X.509 certificate which is also supplied (ExportSymkey). Since only the attackers have the corresponding private key, nobody else can decode the data, even if it falls into someone else's hands during its digital transfer.
The similarity of the two strains of malware manifests itself not only in the protocol but also in the internal data structure for preparing the encrypted sending of data:
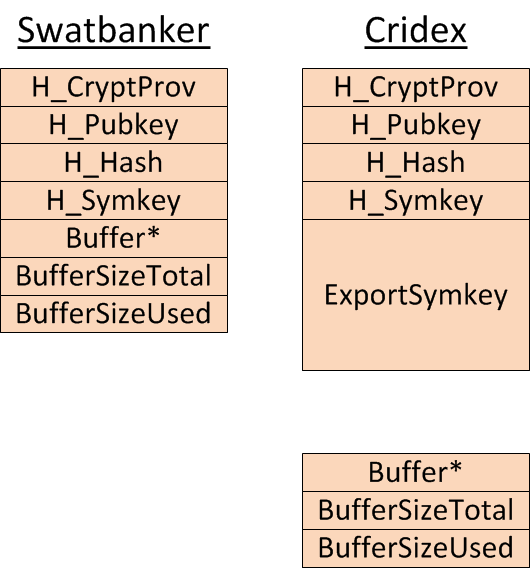
Both variants first have to initiate Windows programming interfaces in order to be able to execute the encryption process described above. The Windows programming interfaces return handles, which represent the initialised state and are saved in the same order by both variants (H_CryptProv, H_Pubkey, H_Hash, H_Symkey).
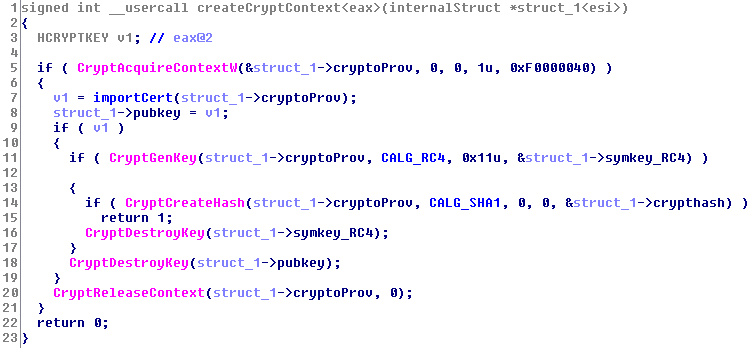
One difference between the two variants is that Cridex already calculates the above-mentioned ExportSymkey during the initialisation while Swatbanker does not do so until immediately prior to sending the data. Another difference is that the pointer to the unencrypted data (Buffer*) is stored in a separate data structure in Cridex, while Swatbanker summarises the pointer and the handles in one data structure. While many internal functions are very similar, the "createcryptcontext" function is actually completely identical in both programs:
Webinjects with a new version number
Another indicator that the two are related arises from the comparison of the webinjects. Webinjects are JavaScript code that the malware injects into the attacked websites. Even at a first glance it is obvious that the webinjects were merely revised and assigned a new version number:
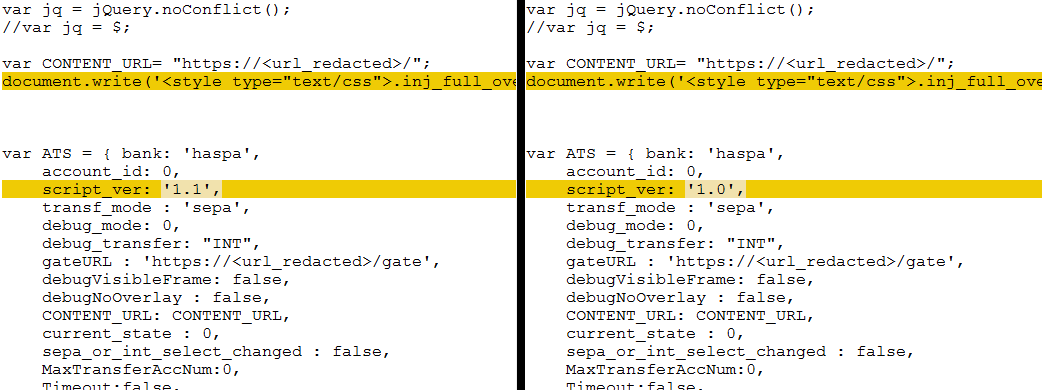
Code excerpt from the new and old variants of a webinject.
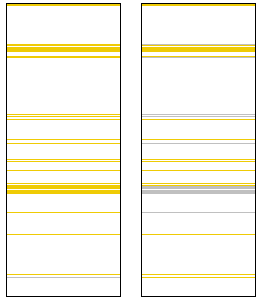
Comparison of the code from the new and old variants of a webinject. Orange bars represent differences.
For fellow researchers:
c5f739b880454bbf4d7570b5e685b7481ff9aa80bb5d3c15fd8eaac5d6d4f289
New URL schemes and waves every day
The attackers now change the URL schemes they use every day, starting new waves of spam with new variants of the malware files to lure ever more recipients into the malware trap and to try to fool AV solutions. Once servers have been hacked, several attack scenarios used by these waves are stored there at once.
The first wave of the current spam mails was detected mid-May and started with supposed invoices from Telekom and Vodafone. Since then, about 20 different URL schemes for distributing the malware have been registered for the four affected companies. By exchanging the URLs as well as the stored variants of the Swatbanker malware files, the attackers naturally want to ensure that AV solutions and potential victims do not stand a chance against these attacks. However, the G DATA protection solutions are equipped to fend off attacks with advanced and extensive protective technologies such as G DATA BankGuard.
Alphabetically-arranged examples of current email subjects, including typos and spelling mistakes made by the attackers include:
- Ihre Rechnung vom [Datum] steht als PDF bereit, [7 Ziffern]_0000000000_[1 Buchstabe]_[8 Ziffern]_[1 Buchstabe]_[2 Ziffern]_[4 Ziffern].
- Ihre neue Rechnung als PDF, [7 Ziffern]_0000000000_[1 Buchstabe]_[8 Ziffern]_B_[2 Ziffern]_[4 Ziffern].
- Information zu: Überweisung/Umbuchung, [12 Ziffern] Information zu: Überweisung/Umbuchung #[10 Ziffern].
- Information zu: Überweisung/Umbuchung, ID:[10 Ziffern]
- Kundenservice Rechnungonline Telekom - Ihre Rechnung [10 Ziffern] vom [Datum].
- RechnungOnline Monat April 2014, Buchungskonto: [10 Ziffern]
- RechnungOnline Monat Mai 2014, Buchungskonto: [10 Ziffern]
- SEPA UMSTELLUNG/ SICHERHEIT IM ONLINE-BANKING
- SPARKASSE SEPA UMSTELLUNG/ SICHERHEIT IM ONLINE-BANKING
- Transaktionscode: [4 Ziffern][1 Buchstabe][2 Ziffern][2 Buchstaben][2 Ziffern][1 Buchstabe][3 Ziffern].
The experts at G DATA SecurityLabs will keep an eye on this case and possibly publish any updates in relation to current events in the G DATA SecurityBlog.
Tips on handling emails:
- An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails also makes sense.
- Email from unknown senders should be treated with caution. If an email looks very strange, here's what to do: ignore it, delete it, but under no circumstances open attachments or click on URLs.
- Opening file attachments, especially from unknown senders, harbours risks. Attachments should first be scanned with an antivirus program and, if necessary, deleted without being opened.
- Links in emails should never be clicked on without thinking. Check the URL. Many email programs permit the actual target of the link to be seen by hovering the mouse over the visible link without actually clicking on it – the so-called mouse-over function.
- Spam email should never be responded to either. All a response does is indicate to the fraudsters that the address they wrote to is actually valid.
- Never disclose any personal information and/or bank data – either via email or on dubious websites.
- Never transfer money to an unknown person.
- Never thoughtlessly publish your own primary email address online, e.g. in forums and guest books, as it can be accessed by fraudsters there. It is useful to enter a secondary address for these purposes.