Installation of the Rootkit
Before the rootkit's loader functionality is executed, it first must be installed as a system service. According to VirusTotal, the rootkit loader is dropped and installed by a malicious executable disguising itself as “Microsoft Foundation Applications” [F2]. The dropper places the rootkit loader into “C:\Windows\System32\drivers\ws3ifsl.sys” [P1] and registers it as a system service in user mode [P2]. The name “ws3ifsl” is probably chosen to disguise itself as Winsock2 IFS Layer (ws2ifsl.sys) which is a legitimate Windows utility for socket communication.
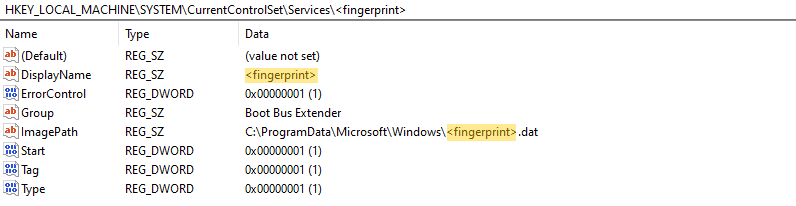
Once the driver is executed, it first moves itself from “C:\Windows\System32\drivers\ws3ifsl.sys” [P1] to “C:\ProgramData\Microsoft\Windows\EventStore.dat” [P3]. Afterwards, it deletes the old service “ws3ifsl” and registers a new system service called “EventStore” pointing to the new location [P3] (see Figure 1). However, this time the service is configured to be loaded as kernel driver with “Type” equals “1”. This is most likely done to prevent users from detecting the service in the Windows Task Manager or Services overview.
Emulation with speakeasy
Since traditional automated sandbox systems are usually not capable of triggering the functions of a kernel driver, we employ Mandiant’s speakeasy emulator instead. The tool allows us to capture memory accesses to extract the plain strings protected by VMProtect and create memory dumps. We increase the default emulation timeout from 60 seconds to 10 minutes:
speakeasy -t <payload> -q 600 -d <results>.zip -o <report>.txt
After speakeasy emulated all 15 API calls to the kernel interface “ntoskrnl.exe“, we find several interesting strings. Among them are four URLs which point to an HTTP address containing the uncommon port 38005 [U1-4]. At the time of publication of this blog post the domains are not registered anymore. The URLs [U1-2] previously hosted the file [F3] and the URLs [U3-4] served the file [F4]. The files [F3-4] contain a base64-encoded blob which turn out to be deaddrops with random-looking bytes in the front and an HTTP URL at the end. As shown in Figure 2 the deaddrops only differ in the URL paths [U5-6] which host the encrypted second stage payload that belongs to the FK_Undead malware family.
Parsing the Deaddrop
The driver uses different deaddrops and FK_Undead payloads depending on the Windows version. It determines the Windows version by calling the system routine “RtlGetVersion” or alternatively the deprecated function “PsGetVersion”. If the Windows version number is equals to 10.0 it will download the deaddrop “auth.bin” [F3] from URL [U1] otherwise “auth7.bin” [F4] from URL [U3] to “C:\ProgramData\Microsoft\Windows\Templates.log” [P4]. If the download fails, it tries to fetch the deaddrop from URL [U2] or [U4]. Once the download finishes, it decodes the base64 blob and decrypts the first 16 bytes with AES-128. While the AES key (”0XMTXKEDTNLDKADSLIOKJASDF”) is 25 bytes long, only the first 16 bytes are used in the AES key expansion step.
The content and structure of the decrypted deaddrop file is visualized in Figure 3. It consists of a begin and end marker, two delimiters as bytes “0D 0A”, an eight bytes long seed and the URL to the FK_Undead payload. After parsing the deaddrop‘s file, the rootkit loader downloads the payload “txlsddlx64.dat” [F5] or “txlsddlx64_7.dat” [F6] and stores it in the Windows program data folder with a filename derived from a fingerprint based on the machine GUID and the fixed-size seed.
Finally, the previously downloaded deaddrop file “Template.log” [P4] is moved one directory above to “C:\ProgramData\Microsoft\Templates.tmp” [P5]. If the malicious driver is loaded again, it first checks if “Templates.tmp” [P5] already exists before trying to download it again.
Decrypting the FK_Undead payload
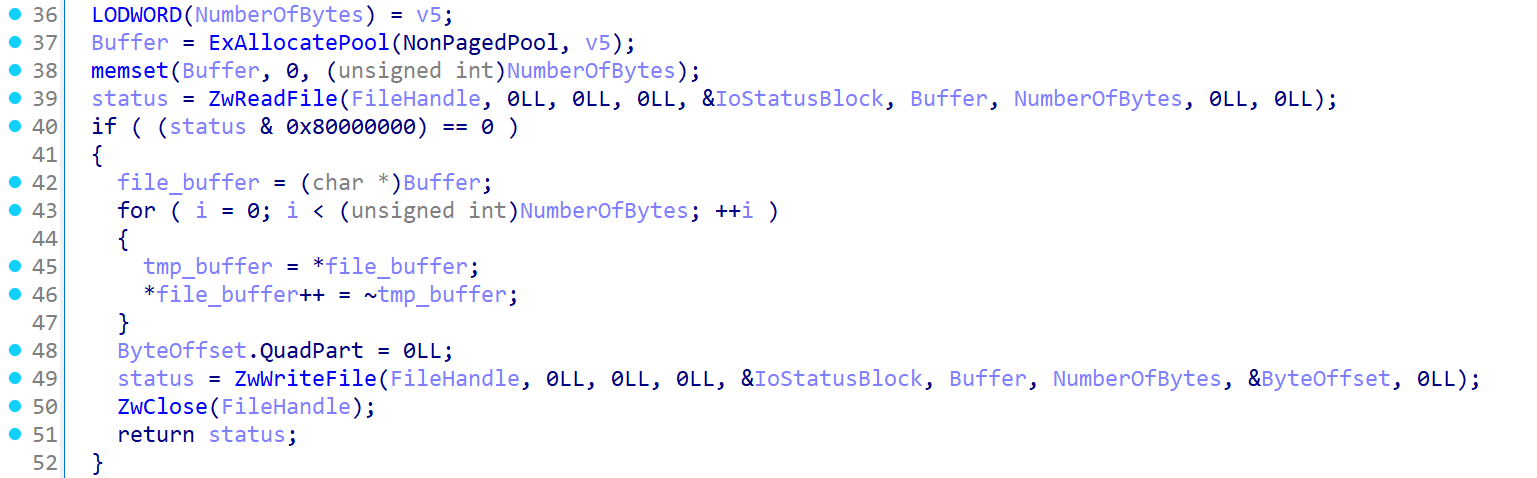
After the payload is downloaded successfully, the rootkit loader decrypts it by inverting every bit (see Figure 4).
The payload is once again a signed driver protected with VMProtect [F7-8]. We identified the sample as a variant of the FK_Undead malware family. As already described in previous blog posts, it routes user traffic via attacker-controlled servers using PAC (Proxy auto-config).
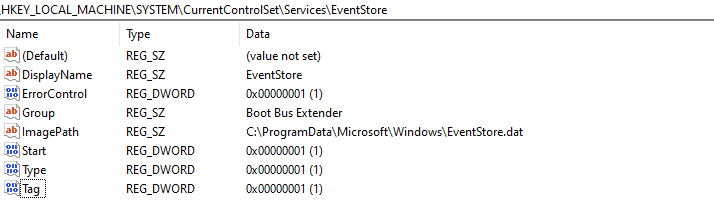
Subsequently, the rootkit loader registers the FK_Undead driver as a new system service using the same function as for the EventStore service but with the generated fingerprint as DisplayName and filename in the ImagePath (see Figure 5).
Evasion Capabilities of the Rootkit
The rootkit loader takes several measures to disguise itself from being detected. First, it checks if files related to PC Hunter (pchunter64as.sys) or Windows Kernel Explorer (WIN64AST.SYS) exist on the system. If this is the case, it will just abort.
Additionally, it scans if drivers from VMWare (vmci.sys, vmmouse.sys, vmrawdsk.sys) or VirtualBox (VBoxGuest.sys, VBoxMouse.sys, VBoxSF.sys, VBoxWddm.sys) are present. However, the rootkit loader does not apply any mitigation if any of the files are found. Moreover, we found an unused function sub_180016DD0 which checks if an Internet connection is available by downloading a file from an attacker-controlled server [U7-8] and saving it to “C:\ProgramData\Microsoft\Crypto\RSA\connect.dat” [P11] (see Figure 6). Unfortunately, we were not able to get the files because the domain is not registered anymore.
The unused function and the missing mitigations for VMWare and VirtualBox indicate that the rootkit loader is still being developed or that the code has been copied and adapted.
Finally, the rootkit loader registers several notify routines using PsSetLoadImageNotifyRoutine and PsSetCreateProcessNotifyRoutine which are triggered if the following executables or drivers are loaded:
- regedit.exe
- 360Safe.exe
- 360sd.exe
- SuperKiller.exe
- register.exe
- HRSword.exe
- WIN64AST.SYS
- pchunter64as.sys
- PCHunter64ar.sys
If such a process is discovered, it waits until none of the SYSTEM.LOG [P6] files are opened by another process anymore. Once this is fulfilled, it calls sub_180015680 to delete the service entries from the registry that the rootkit loader created before for itself and for the downloaded payload [P7-10] (see Figure 7). Thus, it hides from discovery by security solutions or incident responders.
Files
[F1] Rootkit Loader (ws3ifsl.sys / EventStore.dat)
adf0bed4734b416c0c958e096593e93726ba9eb2b39c88645e02033755e16a1b
[F2] Rootkit Dropper
046442a7e16166225a0c070bf8d311caddc48cbe61a4b82d462d8dd4501cfd00
[F3] Deaddrop 1 (auth.bin)
33a305cf2ff910c833e3c8efd77e9f55fc1344215f75a4c8feda6fd5d8e98628
[F4] Deaddrop 2 (auth7.bin)
6af4343fd0ce9b27a2862f75d409d4021efc3160c40a5bda174b2ad30086722d
[F5] Encrypted FK_Undead Payload 1 (txlsddlx64.dat)
10d8591dd18e061febabe0384dc64e5516b7e7e54be87ca0ac35e11f698b0cc2
[F6] Encrypted FK_Undead Payload 2 (txlsddlx64_7.dat)
ca8061f5ee59cba8f8f4e036eddc5f470e0936ebec470a0ebd4e84ab0475ece2
[F7] Decrypted FK_Undead Payload 1 (txlsddlx64.dat)
708f4f45f7515d2b94de5772ee883cfd579dbff216e8a8db3181d2cf0e2a2770
[F8] Decrypted FK_Undead Payload 2 (txlsddlx64_7.dat)
1f5dcc5b0916a77087f160130d5eadb26fe8ee9d47177d19944773d562c03e8e
URLs
[U1] hxxp://tjxgood[.]com:38005/auth.bin
[U2] hxxp://tjxupdates[.]com:38005/auth.bin
[U3] hxxp://tjxgood[.]com:38005/auth7.bin
[U4] hxxp://tjxupdates[.]com:38005/auth7.bin
[U5] hxxp://101[.]37[.]76[.]254:31005/txlsddlx64.dat
[U6] hxxp://101[.]37[.]76[.]254:31005/txlsddlx64_7.dat
[U7] hxxp://microsoftdns2.com:27688/html/png/V[yyyyMMddHHmmssfff].dat
[U8] hxxp://microsoftdns2.com:27688/html/jpg/U[yyyyMMddHHmmssfff].dat
Paths
[P1] C:\Windows\System32\drivers\ws3ifsl.sys
[P2] HKLM\System\CurrentControlSet\services\ws3ifsl
[P3] C:\ProgramData\Microsoft\Windows\EventStore.dat
[P4] C:\ProgramData\Microsoft\Windows\Templates.log
[P5] C:\ProgramData\Microsoft\Templates.tmp
[P6] C:\Windows\System32\config\SYSTEM.LOG[1-5]
[P7] HKLM\SYSTEM\CurrentControlSet\Services\[EventStore/<fingerprint>]
[P8] HKLM\SYSTEM\ControlSet001\Services\[EventStore/<fingerprint>]
[P9] HKLM\SYSTEM\ControlSet002\Services\[EventStore/<fingerprint>]
[P10] HKLM\SYSTEM\ControlSet003\Services\[EventStore/<fingerprint>]
[P11] C:\ProgramData\Microsoft\Crypto\RSA\connect.dat
Certificate Thumbprint
[T1] e2d6c9b698932d209c9fab3f96c48d476a44669a
![A hexadecimal data view displaying both raw hex values and their decoded text representation. The decoded text reveals an HTTP link: hxxp://101.37.76.254:31005/txlsddlx64.dat, followed by the marker [END]. The hex data corresponds to this link and some additional metadata.](/fileadmin/web/general/images/blog/2024/12/GDATA_BLOG_FK_Undead_illu2_DeaddropHex.png)
![The diagram shows an encoded payload structure with AES-128 encryption for the first 16 bytes, including markers [BEGIN] and [END]. It contains a URL for a second-stage payload (hxxp://101.37.76.254:31005/txlsddlx64.dat) separated by delimiters. Fixed-size markers and a seed define the payload's boundaries.](/fileadmin/web/general/images/blog/2024/12/GDATA_BLOG_FK_Undead_illu3_DeaddropStructure.png)