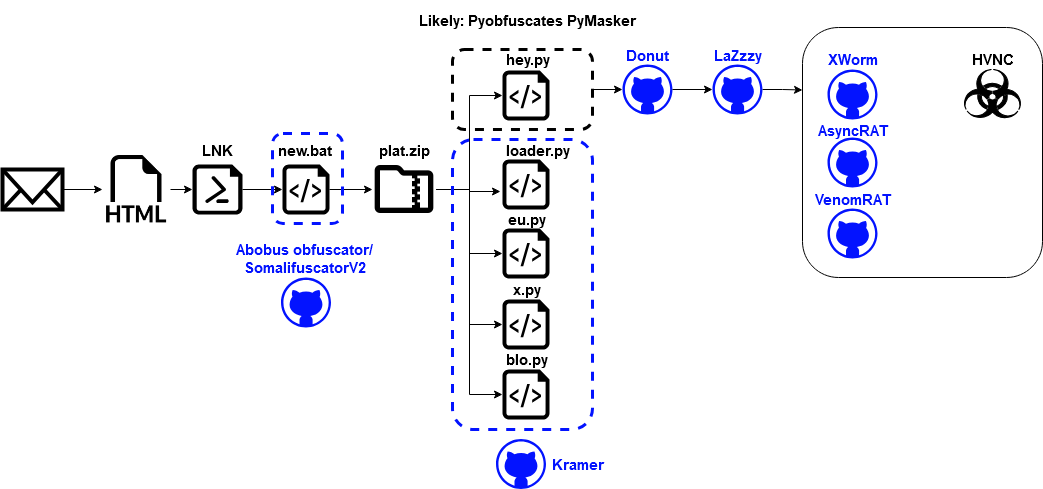
A few days ago, Fortinet published an excellent analysis titled “PureHVNC Deployed via Python Multi-stage Loader” outlining an attack chain consisting of 9-10 stages. Along most of these steps, a different open source software was used for obfuscation or as malware component.
This campaign also, unsuccessfully, tried to infect G DATA customer systems. After receiving a “false positive” report from a customer whose LNK files were quarantined, I discovered an exact replica of the impressive infection chain outlined by Fortinet.
However, that chain was never a serious threat to begin with and does not seem to stem from a well-thought-out process on how it was applied by the threat actor(s). Here is why.
No detections on VirusTotal does not mean it is undetected
To get to the bottom of this, we must understand how antivirus products operate. The beginning of the infection chain, the LNK, batch file and Python scripts had a low detection rate on VirusTotal when the threat was discovered. Nevertheless, we quarantined those parts of the infection chain because the behavior itself was clearly malicious.
VirusTotal uses dedicated command line scanners from each antivirus vendor. These do not have the full features of the product, especially dynamic features and those that require the backend/cloud which are not covered by the command line scanner. E.g. in the case of G DATA Antivirus/XDR flagship protection components like BEAST and DeepRay are not part of the VirusTotal command line scanner.
This can lead to the wrong impression that antivirus products are perpetually lagging behind threat detection and only play catch-up with pattern scanning, when in fact they employ a wide variety of protection mechanisms that also work for newly developed malware. What public discourse often does not take into consideration when claiming that “antivirus is dead” is that very often these mechanisms tend to be dynamic or use context information and do not have to rely on a signature patterns. But when they find new malware, all the other protection mechanisms follow suit and integrate automatic patterns, among others, or use the malware in training sets for machine learning.
Adding more evasion layers worsens malware evasion
This might sound counterintuitive at first, after all the threat actor is adding more components to protect the malware payload. Does this make reverse engineering harder? Definitely! The analysis of a chain with 10 layers or more can be draining, because each step includes more tricks to leech time and resources out of human analysts. But does it help with evasion?
An infection chain needs to successfully execute from the start to the end of the chain to deploy the payload. Every step along the way, the protection products have a chance to intervene and therefore disrupt the chain. That means just one of the components or artifacts in that chain need to be detected for successful prevention of the infection.
So, adding more layers to the chain just provides more opportunity to prevent it. To put it into a metaphor: The chances to score a goal are greater the more attempts you have.
Open source malware: Hard to reverse but easy to detect
In the case of the malware discovered by Fortinet, the threat actors used the following open source obfuscators: Kramer, SomalifuscatorV2, Abobus obfuscator (used in some cases[1] instead of SomalifuscatorV2). These obfuscators are not malware, they can also be used by legitimate software for protection against reverse engineering.
Futhermore, the threat actors used the malware/shellcode loaders LaZzzy and Donut, which are considered malicious due to their focus on malware evasion, e.g., Donut patches the Antimalware Scan Interface and LaZzzy has an option to sign files with spoofed certificates.
Even some of the malware payloads themselves are open source, e.g., XWorm RAT.
Open source malware loaders like Donut are indeed tools that can be considered sophisticated. Donut is hard to reverse engineer from scratch. I attempted this until I figured out that there is a decoder for Donut, which is also open source. However, Donut has been known for years and as such the code that it generates is well-detected by antivirus vendors. The same is true for LaZzzy.
Adding any well-detected open source malware loaders unaltered to an already convoluted infection chain seems like a haphazard attempt to evade antivirus scanners. In Germany we call this “Verschlimmbesserung” – a noun that roughly translates to making something “worse-better”, or “making things worse in an attempt to improve them”
All poking fun at German compound words aside, by combining all those tools the threat actor(s) basically are throwing stuff at the wall hoping that something will eventually stick. But this is not how any of this works.
What is sophistication anyways?
Sophistication of a threat can refer to several things. In the case of the malware outlined by Fortinet, reversing the whole chain is challenging as the malware employs all tricks of the trade. So if we define sophistication as difficulty in reverse engineering and skillfullness of the--in this case open source--developers, the PureHVNC chain certainly falls into that category.
But sophistication of a threat can also refer to skillfulness in the malware deployment, successful evasion, and high risk of causing damage or harm. I can see neither of these in the PureHVNC campaign.
References
[1] new.bat with Abobus obfuscator, loads plat.zip (see [2]) 78847e8b593b0599d24669a1b0140bb84cb8a055a5caf8b990e8fddee67346f5
[2] plat.zip 4bb6ca3a4f3bd5f2357c983d7f767ee203112765e86ba38b017bb202b74e9853