A big portion of my work as malware analyst at G Data is writing detection signatures for our product. One of those signatures checks for a USB worm component that I have seen in certain variants of .NET based RATs like njRAT and BlackNet RAT. When this worm signature hit on an unidentified sample[1], I got curios. It was a .NET ransomware that seemed oddly familiar to me. I couldn’t put a finger on it yet.
Initial static analysis
The ransomware[1] contains the following image in its .NET resources and a ransom note in the strings listing (see pictures below).
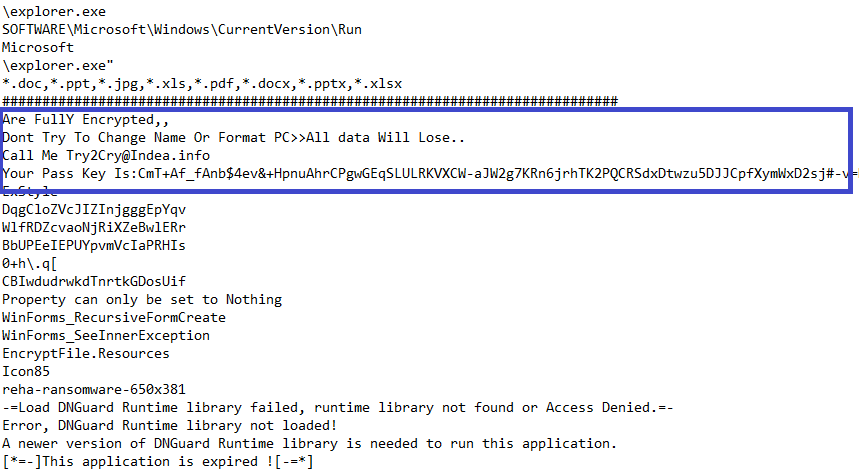
The strings listing indicates
- DNGuard was used to protect the sample
- .Try2Cry extension is appended to encrypted files
- Contact email is Try2Cry@Indea.info
The sample crashed upon running and removing the DNGuard protection seemed very tedious. It also seems to be a trial version of DNGuard. So I used an old trick that I have up my lazy-analyst sleeves and made a Yara hunt rule to obtain similar samples on VirusTotal. As the malware developers often test their samples on Virustotal with and without certain protection features applied, you can usually find unprotected ones.
Indeed, I found 10 more Try2Cry samples, none of which had DNGuard protection. Some of those samples have the worm component, some of them don’t. A few of them have Arabic ransom notes. All of them append .Try2Cry to encrypted files.
Identifying the ransomware family
In private conversation with Michael Gillespie, he identified the sample as being a variant of the “Stupid” ransomware family. By the way: This name was given by the malware authors themselves and is not a mocking from our side.
“Stupid” is an open source ransomware on Github that has numerous variants. This explains the familiarity I felt while seeing the sample.
The following analysis is mainly based on sample [2] and sample [3]. Sample [2] has a slight obfuscation. Sample [3] has no worm component but also no obfuscation, making it a better candidate for code based screenshots. This sample [3] also uses Arabic ransom notes and a different contact email: info@russianvip.io
Encryption
Try2Cry targets files with the following extensions:
*.doc,*.ppt,*.jpg,*.xls,*.pdf,*.docx,*.pptx,*.xls,*xlsx
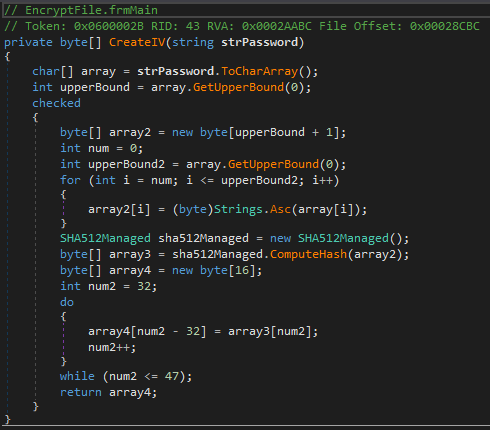
The encryption method uses Rijndael, the predecessor of AES. The encryption password is hardcoded. The encryption key is created by calculating a SHA512 hash of the password and using the first 32 bits of this hash (see left picture below). The IV creation is almost identical to the key, but it uses the next 16 bits (indices 32-47) of the same SHA512 hash (see right picture below).
The developer has put an exception for the machine names DESKTOP-PQ6NSM4 and IK-PC2. The ransomware will not encrypt if a system has any of those names. These are most likely the names of the malware developer’s systems and were put in place as safeguard while testing the malware.
Worm component
The worm component uses a similar technique as Spora, Dinihou or Gamarue.
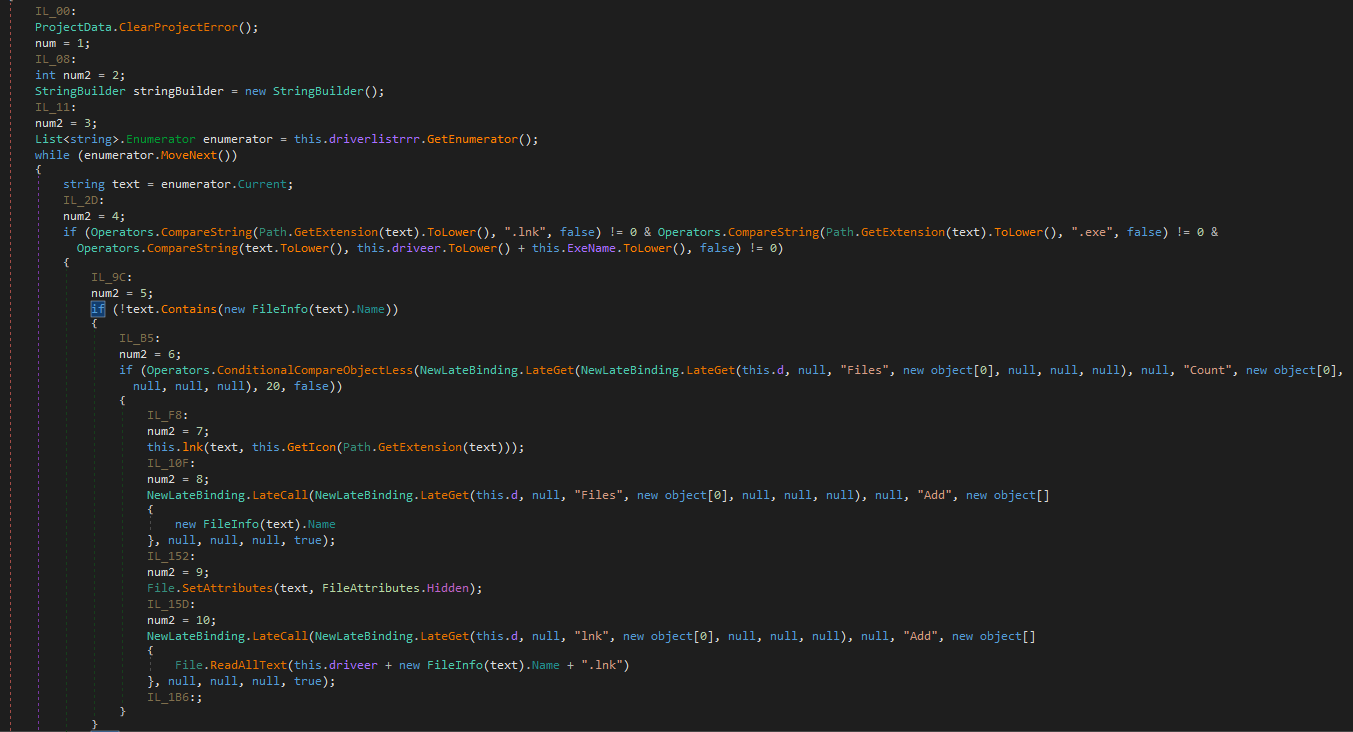
The sample searches for removable devices, then places a hidden copy of itself named Update.exe in the root folder of the device. It applies hidden attributes for every file in the device and replaces the original files with non-hidden Windows Shortcuts using the same icon. E.g. for a file named presentation.pdf, the ransomware places a presentation.pdf.lnk with a PDF icon. This shortcut will run the hidden Update.exe and also the original file presentation.pdf.
Additionally the sample will place visible copies of itself that have and icon folder and Arabic names. They are designed to trick the user into clicking them. This placement of Arabic copies is also present in samples without the LNK worm component. Google translates the Arabic file names to:
- Very special
- Important
- passwords
- a stranger
- The Five Origins
The pictures below show what it looks like with a USB drive that previously had some folders with pictures in it. On the right side I set the option to show hidden folders and known extensions.
Try2Cry tries
Unlike Spora there are tell-tale signs of the USB drive infection, like the arrow in the corner of the shortcut icons and the additional Arabic executables.
Like other variants of the “Stupid” ransomware family, this ransomware is decryptable. It seems that this is just one of many variants of copy & paste ransomware created by criminals who can barely program. This problem would not arise in such a scale if public repositories like Github were more stringent to remove open source malware.
Sample Hashes
[1] f6521e298c849c14cd0a4d0e8947fa2d990e06d978e89a262e62c968cefd9b8f (initial sample, DNGuard protected) [2] 3786ad08d8dacfa84a0c57b48dfa8921435f5579235d17edc00160e7a86ae1c5 (with worm component) [3] 590885b5afc3aa1d34720bb758fb2868bb0870557db2110e61397a5364c7f8b3 (without worm component) [4] 2c5f392767feced770b37fce6b66c1863daab36a716b07f25c5bef0eeafc0b26 [5] 3b65dbd9b05019aae658c21f7fcb18dd29eea1555cc26c3fa12b9aa74ea55b88 [6] 8594533a7544fa477e5711d237ccac7f4a62c2c847465ccea3cfdb414a00a397 [7] cefb7262229b0053daf3208f7adc7d4fb4edaf08944a9b65d7eb1efaa3128296 [8] dd036085f8220d13c60f879ff48ccf6c7d60893217fc988ae64d2ee6a4eb3241 [9] fb621d2c94b980d87a8aa3239ebeda857a2fcb29f5aac08facacdc879f9ce784 [10] fd24367e7a71bce4435fb808f483e0466df60e851fd05eed9c2fd838404e7a9d