"Creating and removing viruses is our vocation"

G DATA analysts discovered a ransomware that poses as "Enigma SpyHunter5". SpyHunter is a "Malware Remediation Utility" by EnigmaSoft. The ransomware adopts the logo of SpyHunter as its icon, the file name is "SpyHunter5.exe" and it uses file properties that hint to SpyHunter as well.
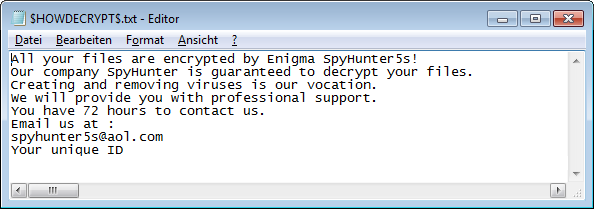
While it is common for malware to appeal to the user by presenting itself like a well-known program, this ransomware goes a step further and pretends it was in fact the SpyHunter application which encrypted the system. The ransom message states "Our company SpyHunter is guaranteed to decrypt your files. Creating and removing viruses is our vocation".
Ransomware is a variant of GarrantyDecrypt
The ransomware is a variant of the GarrantyDecrypt family. We found the first mention of it in October 2018 by Michael Gillespie on Twitter.
Most ransomware families have a list of file extensions to search for personal documents, backups and images that they target for encryption. It is rather unusual that GarrantyDecrypt targets files regardless of their extension. That means it will also encrypt, e.g., executable files. It appends ".spyhunter" to encrypted files and places a ransom note named $HOWDECRYPT$.txt into affected folders.

The ransomware binary is packed using a VB6 stub. The packer's stub obfuscates the path for the library import of MSVBVM60.DLL in such a way that Detect it Easy is not able to identify that it is indeed a Visual Basic 6 executable (see picture on the right side). Windows does not seem to care about additional slashes and backslashes in the path.
The packed file uses self-injection to execute the unpacked payload dynamically. Unlike older GarrantyDecrypt variants (see IOC list) the unpacked sample has obfuscated strings, e.g., for the ransom note name and contents, and folders which are excluded from encryption. The strings are decoded dynamically.
GarrantyDecrypt uses the CryptoAPI and RSA. A list of function imports from the CryptoAPI is below (created by PortexAnalyzer). Exact analysis of the encryption process is pending.
Like most ransomware families it deletes shadow volume copies to prevent recovery of files.
[Cryptography Functions] <Data Encryption/Decryption>
rva: 0x1024, va: 0x401000, hint: 0, name: CryptEncrypt -> Encrypts a section of plaintext by using the specified encryption key.
[Cryptography Functions] <Key Generation/Exchange>
rva: 0x1014, va: 0x401000, hint: 0, name: CryptDestroyKey -> Destroys a key.
rva: 0x101c, va: 0x401000, hint: 0, name: CryptExportKey -> Transfers a key from the CSP into a key BLOB in the application's memory space.
rva: 0x1020, va: 0x401000, hint: 0, name: CryptGenRandom -> Generates random data.
rva: 0x1028, va: 0x401000, hint: 0, name: CryptGenKey -> Creates a random key.
rva: 0x102c, va: 0x401000, hint: 0, name: CryptImportKey -> Transfers a key from a key BLOB to a CSP.
[Cryptography Functions] <Service Provider>
rva: 0x1000, va: 0x401000, hint: 0, name: CryptReleaseContext -> Releases the handle acquired by the CryptAcquireContext function.
rva: 0x1018, va: 0x401000, hint: 0, name: CryptAcquireContextA -> Acquires a handle to the current user's key container within a particular CSP.
Some files can be recovered
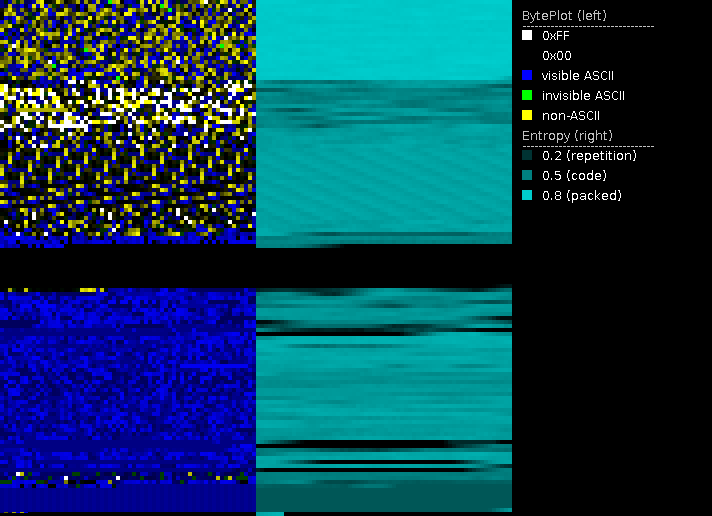
After creating a visualization of the encrypted files using PortexAnalyzer, we can see that only the header, more specifically the first 0x2800 bytes, is encrypted (see picture below). Ransomware may do this to speed up the encryption process. From a malware author's perspective, this shortcut also has its downsides: modifying file headers in bulk (e.g. thousands per second) can tip off installed security software.
There is also some data appended to the file. Services like id-ransomware are able to identify the GarrantyDecrypt family based on data in encrypted files.
File recovery programs are able to determine the original file format of such files and can create valid headers for them. In a proof-of-concept test we were able to recover some of the encrypted files. The success rate highly depends on the file format.
Systems with Russian, Ukrainian and some others languages are safe
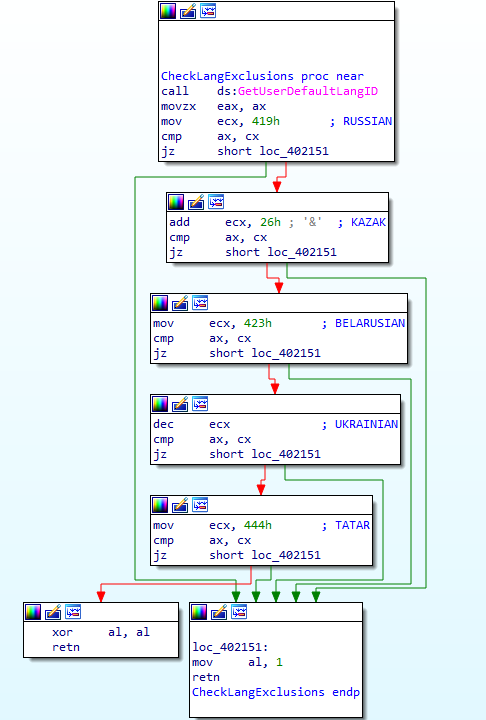
GarrantyDecrypt checks the default language of the system. If it is Russian, Ukrainian, Kazak, Belarusian or Tatar it will not encrypt any files and terminate instead.
IOCs
| GarrantyDecrypt sample that we analysed in this article | |
|---|---|
| SHA256 | 730046dd331ffe44a007477287deaa4f600026acca1cb4fcbdbbcfc607aa0d9b |
| Detection name | Win32.Trojan-Ransom.GarrantyDecrypt.A |
| File extension | .spyhunter |
| Contact email | spyhunter5s@aol.com |
| File name | SpyHunter5.exe |
| Older variant of GarrantyDecrypt for comparison | |
| SHA256 | 5a8f6d1ea5dc2a1b8b65bdc33a62f6662b240d9b7219551f132fc6f5d6b92160 |
| Detection name | Generic.Ransom.GarrantDecrypt.5BF25D46 |

