Why force your way into a house when you can trick the owner into letting you in? This concept has always been used by malware authors to gain access into their victims' computers. They understand that the most sophisticated security system does not completely guarantee protection for the user. This is especially true if the job of that person includes opening and reviewing multiple documents (such as resumes or invoices) from their email inbox. With that in mind, let us look into one of the products that malware authors prefer to abuse when it comes to deploying malware: Microsoft Word.
More than a Word Processor
Microsoft Word is one of the most recognizable products as far as Word Processors go, with a user base of well over 100 million commercial users as well as more than 27 million consumers for home and personal devices.
Even back in the 1990s, it was able to overcome its competitors like WordStar and WordPerfect by introducing features that would enhance the user experience when it comes to browsing and editing documents. By 1994, had cornered 90 percent of the word processor market, making Microsoft Word a permanent fixture on most computers.
The introduction of Macros, also known as Visual Basic for Applications (VBA), gave users the power and the flexibility to create custom solutions. VBA therefore is capable of launching other applications on the host computer (see code listing below) or simply created dialog boxes.
This has far-reaching implications: Malware authors can create a document file capable of downloading and executing a file when it is opened and macros are enabled by the user.
Another option is to leverage Macros to run PowerShell, (code listing below) which is a scripting language built on Microsoft .NET. It is a popular choice among system administrators because it is the most powerful way for them to administer Windows computers. But with PowerShell having access to the .NET Framework, Windows Management Instrumentation (WMI), Active Directory Service Interface (ADSI) as well as the Win32 Application Programming Interface (API), penetration testers saw its potential leading to the creation of pentesting tools such as Nishang as well as Post Exploitation tools such as Empire.
<#
PowerShell command for running calc.exe.
Specifying "1" as the second argument opens the application in normal size and puts it on top.
#>
Dim RetVal
RetVal = Shell("C:\WINDOWS\CALC.EXE", 1)
# This PS script will open a dialog box
Dim RetVal
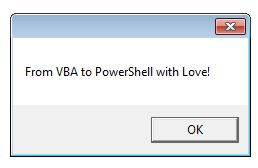
RetVal = Shell("powershell -NonInteractive -NoLogo -NoProfile -WindowStyle Hidden -ExecutionPolicy unrestricted -Command $message = 'From VBA to PowerShell with Love!';[reflection.assembly]::loadwithpartialname('system.windows.forms'); [system.Windows.Forms.MessageBox]::show($message)", vbNormalFocus)Using vulnerabilities
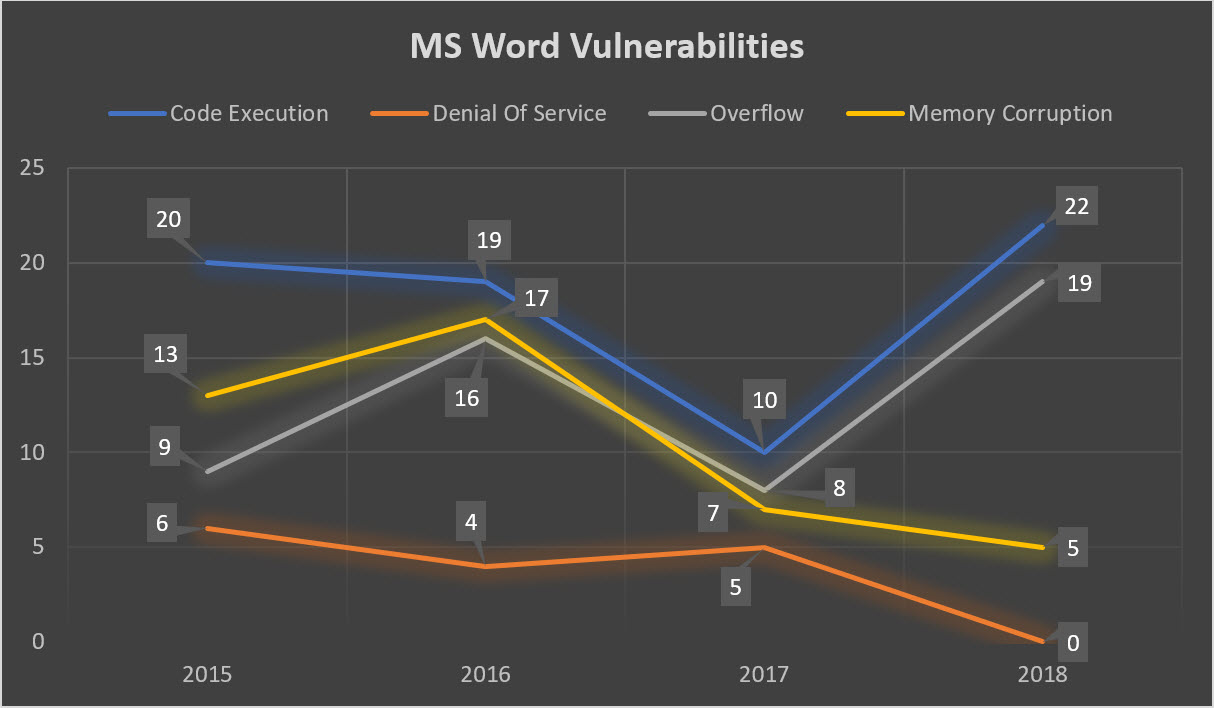
If the malware author feels that scripting will not cut it, they can easily step it up. This can be achieved either by using vulnerabilities that have been researched by themselves or by using the 46 publicly disclosed vulnerabilities for Microsoft Word with 22 cases of Code Execution for 2018 compared to the 10 cases recorded in 2017. Note that these figures did not consider undisclosed vulnerabilities which have yet to receive a Common Vulnerabilities and Exposure (CVE) designation.
However, malware authors do not need to use exploits all the time. Nesting a document inside another document (See Figure 4) or saving a document in a different file format supported by Microsoft Word (e.g. Single File Web Page (.mht) ) will help make a malicious macro less obvious (See Figure 5).
An active user base, the presence of native features that can be subverted, an active interest in the area of software vulnerabilities, as well as the ease of obfuscating a malicious macro script: what's not to love about MS Word by malware authors? This combination makes it possible to deploy a payload with a high change of it being opened by a user. But how does that assumption hold up in the real world?
So what is new, exactly?
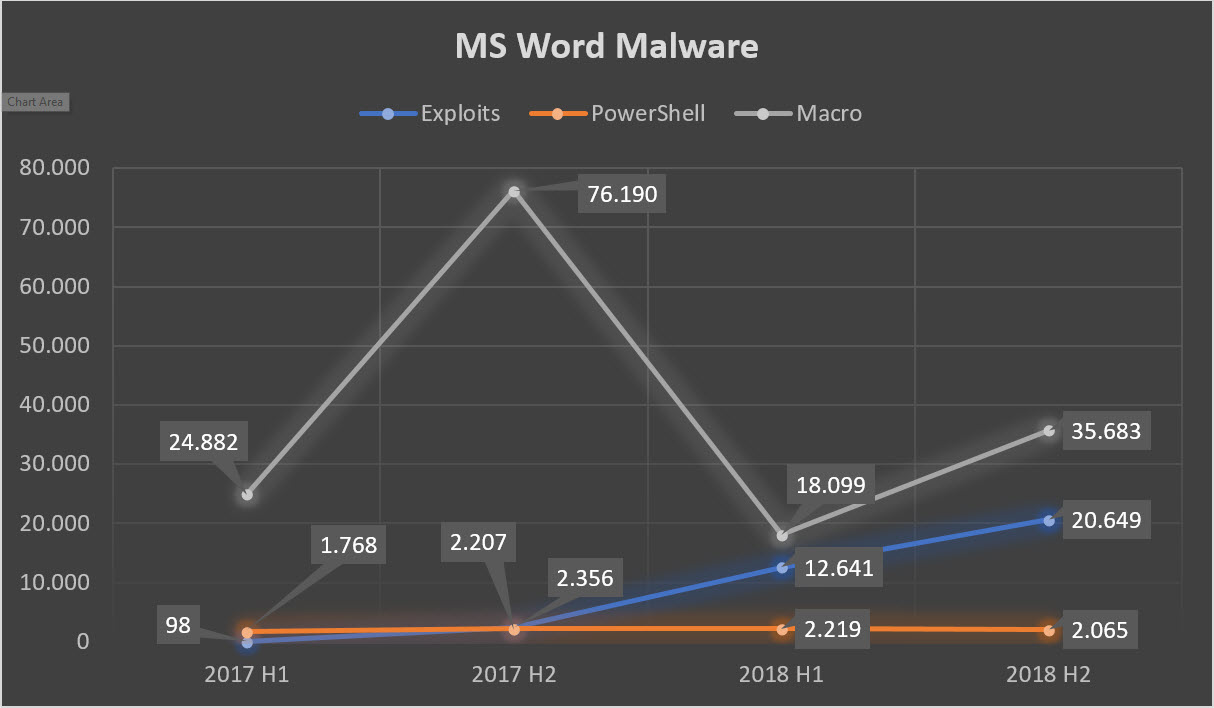
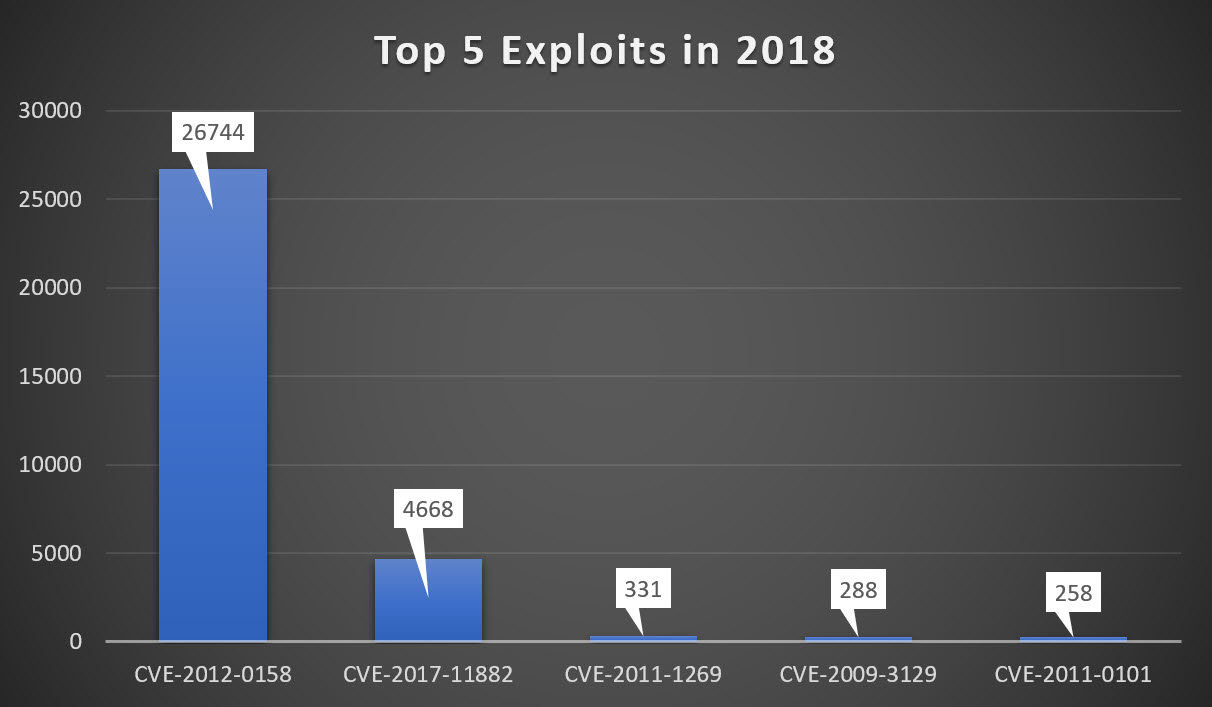
Malicious macros still lead the pack of common techniques used in Office documents despite having experienced a steep drop between the last half of 2017 and first half of 2018. Given that macros are disabled by default (as of Microsoft Excel 2007) and that tricking victims into re-enabling them is difficult, malicious actors are moving away from traditional macro-based attacks towards other, more potent techniques. This can be seen in the steady increase of Exploit and PowerShell based attacks with a 99 percent increase of Exploits from 98 in the start of 2017 to 20,649 by the end of 2018 (See Figure 6).
We will only discuss the top two exploits presented here, which are CVE-2012-0158 and CVE-2017-11882, since the first is a 6-year-old vulnerability while the other is a quite recent vulnerability.
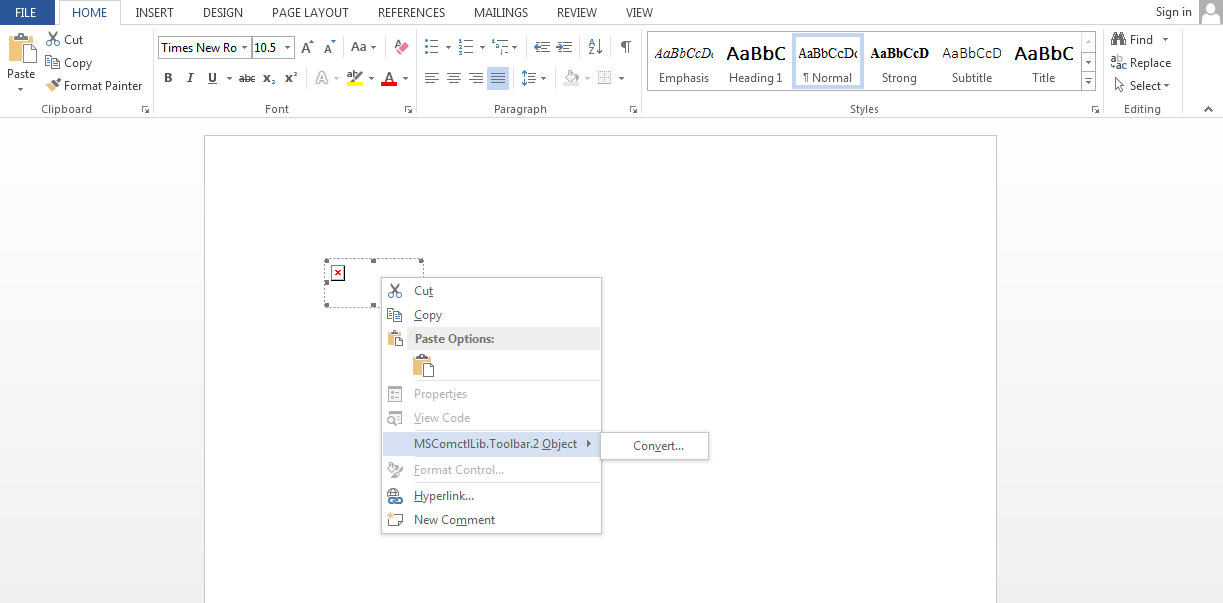
CVE-2012-0158 was previously seen in October 2014 distributing Remote Access Tool (RAT) and our findings has been discussed in detail in our Blog entry entitled “Operation "TooHash": how targeted attacks work”. It was relatively straightforward back then, but malware authors have changed their approach by embedding the malicious codes in toolbars Objects.
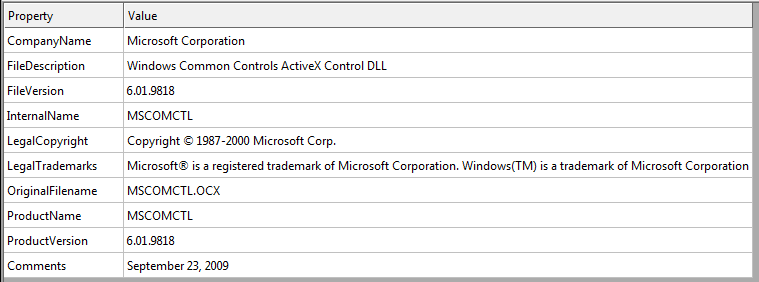
CVE-2012-0158 relies on a vulnerable version of MSCOMCTL.OCX (See Figure 8) which is responsible for ActiveX controls. It is a key application that is used by several Microsoft Applications such as Microsoft Internet Explorer and Microsoft Office, wherein it allows an application to use a functionality of another application.
It is classified as a Buffer Overflow attack, which is triggered when a certain part of the memory gets overwritten with malicious code and executed afterwards. This allows malware authors to execute custom commands in the victim’s computer with the vulnerable version installed in a stealthy manner.
Malicious Formulas
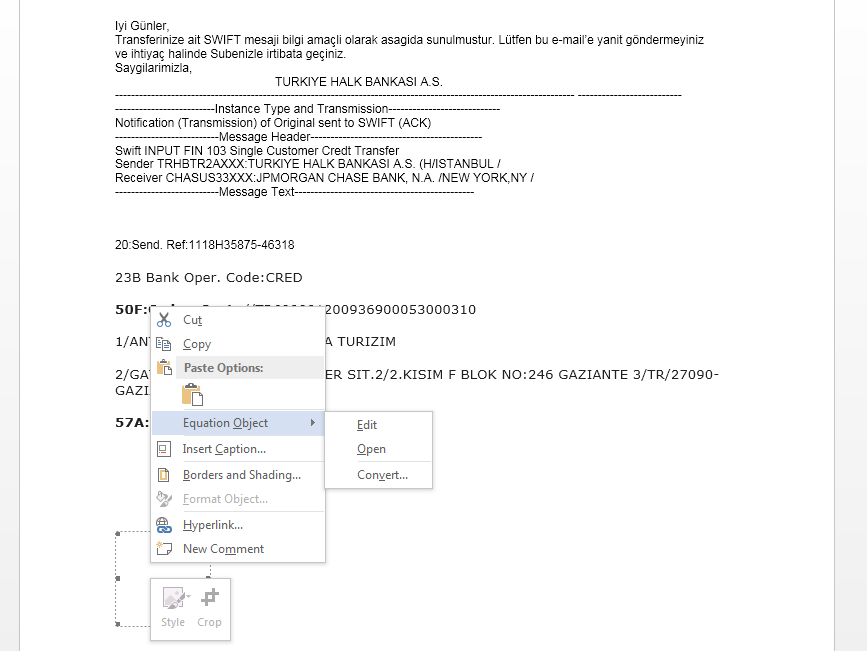
CVE-2017-11882 comes in second and it relies on the Microsoft Equation 3.0 which allows user to create equations using known mathematical notation. By inserting a Microsoft Equation 3.0 object into the document (See Figures 10 and 11), users can create an equation such as (x+a)^n=∑_(k=0)^n▒〖(n¦k) x^k a^(n-k) 〗 which would be difficult using the normal character set of Microsoft Word.
The rest of the scheme is rather predictable: Malware authors start by sending an email with a convincing argument that tricks users into opening a malicious attachment. In this case, they claim it to be from H&B Wire Fabrications ltd saying that a user has a remittance document. The document tries hard to look like an invoice, but the embedded equation object (See Figure 13) stands out due to it having no value.
Upon exploitation, the malicious document then calls Windows Command Line which then calls msiexec.exe to download and silently install a malicious backdoor into the victims’ computer.
Backdoors are one of the most frequently used payloads due to their extensive range of potential uses. Once it is in place, backdoors can be used to do a myriad of things like downloading additional malware, exfiltrating files of interest, accessing network resources and many more.
Users who constantly update their computers do not have to worry too much, since both vulnerabilities have been addressed by Microsoft with MS12-027 being the patch for CVE-2012-0158 while CVE-2017-11882 was fixed on November of 2017. However, the volume of samples suggests that malware authors are aware that most victims do not update their systems and that using vulnerabilities for key windows components are the way to go.
Take for example Microsoft Equation 3.0: This can be removed without having adverse effects to the user’s computer while removing MSCOMCTL.OCX will be problematic since other windows applications like Microsoft Internet Explorer are using it. Even Microsoft removed Microsoft Equation 3.0 in favor of the Built-in Equation and Symbols editor with the launch of the January 2018 Public Update, which in turn made attacks using CVE-2017-11882 useless.
There is a lot to love about Microsoft Word due to its rich features such as, but not limited to, Macros, Embedding Objects, and Multiple File Formats. On top of this, the program is widely used and almost universally adapted into everyway workflows by home users as well as in businesses. Bear in mind, though, that malware authors also love Microsoft Word for the same reasons. With Microsoft Word, a skilled malware author can use various tricks like these to infect users, making it one of the many options that they can use to deploy malware.
Mitigation strategies
The fact that Microsoft Word is susceptible to all manner of attacks does not mean that we should throw out Microsoft Word. Users can protect themselves effectively by following these simple steps:
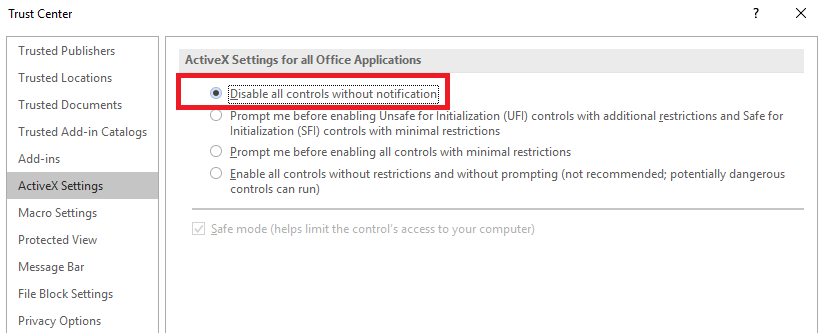
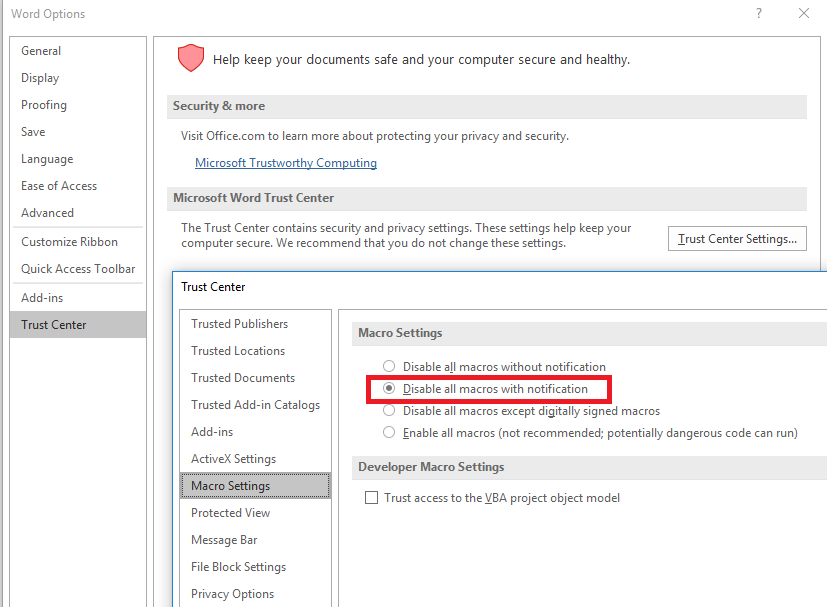
- Macros, ActiveX, Fonts, Formula Editors and Codecs should not be activated if they are not needed. These features can be deactivated with Trust Center which can be found by navigating via Options -> Trust Center. Disabling Features through Trust Center can be done across Microsoft Office Products such as Excel and PowerPoint.
- If using ActiveX or Macros is a requirement, make sure that the notification option is enabled. That way you will be notified if the document needs additional permissions to execute.
- You need to have an end point security solution in place since it is your computers’ last line of defense.
- Furthermore, a backup of important files in case your computer is going to be compromised is strongly recommended. This can be in the form of a local backup or an off-site backup.
- Always keep your software up-to-date since most vulnerabilities used by malware authors have existing patches available. This is one of the key points that we have learned from ransomware victims in 2017.
- Do not open attachments or click on links from unknown sources. Banking Trojans such as Emotet to Ransomware such as WannaCry spread through these methods.
- And lastly: stay informed and be vigilant. Remember that users are the weakest link in any system and malware authors know this. The best policies and the best protection technologies are useless if the user just ignores and or disables them.
IOC’s and Corresponding G Data Detections
Embedded CVE-2012-0158 311c2f1a732a56bfab0d66b344228fcbd928118f2ae219a8c57dfc5511334ab6
[Exploit.CVE-2012-0158.Gen]
Root Email File
c9382456adeb2245c3fc21107878a5eb4bfd65d427cf42d72f06dd479bcdfe6a
[Exploit.CVE-2017-11882.Gen]