Companies looking to save costs by foregoing IT security measures should adjust their calculations. As current examples show, it is becoming increasingly expensive to delay actions or reject investment proposals.
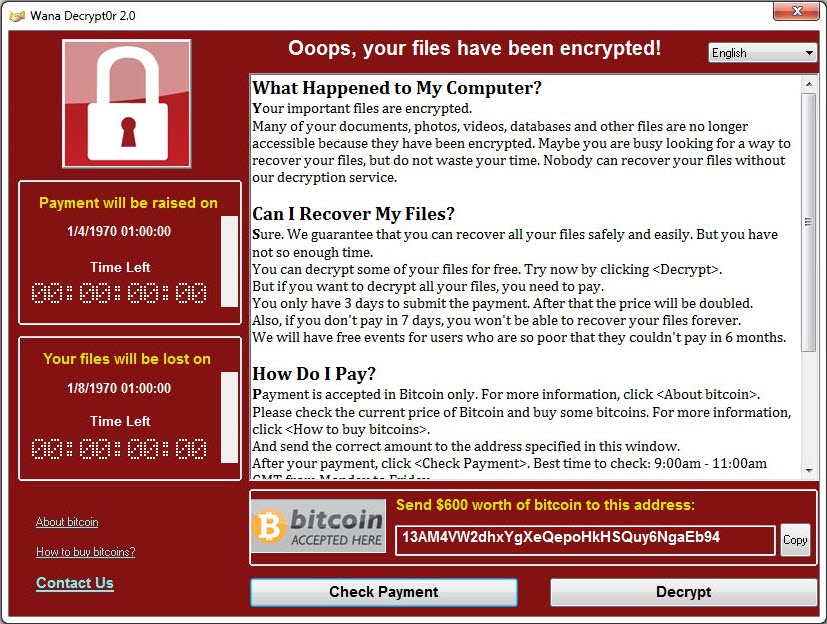
According to the company, Taiwanese company TSMC recently experienced an outbreak of the infamous WannaCry ransomware. Taiwan Semiconductor Manufacturaing Company manufactures processors and systems-on-a-chip (SoCs) for desktop computers and smartphones for many major manufacturers. The company also manufactures Apple-designed A12 chips for the coming iPhone generations. After installing a new computer in the production network, WannaCry was able to spread across the internal network - probably because not all available patches had been applied to the computer prior to connecting it to the network. TSMC would not have applied basic IT security best practices in this case. As a result of the incident, production at several sites ground to a screeching halt over the weekend. The company itself estimates the cost of the incident to be around 3 percent of annual turnover - about 170 million USD. The company is optimistic to still reach its financial goals for 2018, but the remaining quarters will have to make up for the current loss.
Another breach, another cause
The Dailymotion video platform has also suffered costs due to inadequate IT security. Although the scope is much smaller than with TSMC, it could still turn out to be a ground-breaking event. After a conviction by the French data protection authority CNIL, the company must pay a fine of 50,000 Euro after the loss of customer data. According to the data protection authority, Dailymotion is partly to blame for this, because the administrator password for a system of the provider was found in the code repository Github. The attackers did not need to find vulnerabilities in the system or phish user data to gain access - they could simply log in with full access rights. The penalty is low compared to the costs of a comprehensive hacker attack - but after the entry into force of the General Data Protection Regulation (GDPR), further penalties of this type can be expected to be handed down to companies, if they do not take better care of their customer data. Depending on the severity of a case, the maximum penalty is up to 4 percent of a company's global turnover.
But it is not only the penalties themselves that are relevant in the assessment - for companies, the confidence of users in their products and data protection practices is particularly important for future business development. "In the course of the adjustment of their processes to the GDPR many enterprises already recognized the necessity of lasting investments in IT-security," says Michael Zimmer of G DATA Advanced Analytics. "IT security incidents usually lead to reputational damage and these are regularly feared more than the high maximum penalties."
Security incidents must be reported to the authorities
According to the GDPR, companies in Europe must report certain security-related incidents to the relevant data protection authority. In addition, affected users must be informed. This should make the security practices of companies much more transparent. Based on this, customers could make a more informed choice about which company they want to entrust with their personal data. With regular reports, the Australian Data Protection Authority OAIC shows how the public could be better informed in this area. The figures show that there are not only very large data leaks with more than 50,000 or even 1 million breached records get reported, but also numerous minor incidents. For example, if an accident happens to the baker around the corner and the customer file is viewed by unauthorized persons.
According to the report, the most frequently leaked information is contact details - i.e. e-mail or postal addresses. These account for 89 percent of reported incidents. Second place with 42 percent are financial data. Health-related information was affected in 25 percent of all reported cases.
Data leakage due to BCC-failure
Hacker attacks are not always the cause of data breaches. In about 36 percent of the cases, human error is said to be to blame. Examples of this are also listed in the report: personal information was sent by e-mail to the wrong addressees, in other cases the popular CC-Fail occurred - an e-mail to many people was sent to an open distribution list and not to recipients masked by BCC (blind carbon copy). It also often happens that devices containing personal data or paper documents containing personal information are disposed of insecurely or inappropriately. In the worst case, the data then ends up in a publicly accessible (waste) container.
In other cases, however, attacks are responsible for the outflow of personal information. Most commonly used are reused login data or otherwise compromised logins. At HaveIbeenPwned.com users can easily check if access data was already affected by a data leak. The Hasso Plattner Institute offers a similar service which is called Identitiy Leakage Checker. In 29 percent of reported cases, access data was accessed via phishing, i.e. via reconstructed website logins or phishing campaigns sent via spam e-mails. In addition, access data can be cracked by brute force attack using very easy to guess passwords.
Cybersecurity costs can be calculated
Much has been reported about corresponding data leaks in recent years. In fact, these not only cause reputational damage to companies, which is difficult to assess financially, but also cause clearly quantifiable costs. The Ponemon Institute calculates the cost of data breaches once a year on behalf of IBM [report as PDF]. On average, companies pay around 3.86 million US dollars per incident. The average cost per record accessed illegally is 148 USD. This data constitutes approximate values, but they can serve as a basis for companies to calculate their own risk analyses. One of the biggest data leaks in recent history was experienced by US financial services provider Equifax. The estimated cost is approximately 439 million Dollars. Equifax is only insured for 125 million - the difference must be paid by the company itself. The Equifax hack was caused by an unpatched Apache-Struts application server.
Companies can protect themselves against the risks described with professional IT management and the right security solution. Business customers of G DATA can book a patch management solution, in order to keep operating systems and software up-to-date easily to protect against exploits. Endpoint protection must also not be neglected when users interact with a system. G DATA products can minimize threats from Ransomware, tech support scams and other viruses or Trojans.