Threats in the cloud
The usage of cloud services for storing or processing data or running platforms is rising. Cloud resources are also abused by malware for criminal purposes. The usage of cloud services for malicious or fraudulent purposes will rise. As the usage of cloud processing increases the more attractive it is for cyber criminals to attack cloud infrastructures. Attacks against cloud services and storage are complex, but not impossible. We expect to see this at some time in the next year.
Phishing and spam with personalized data
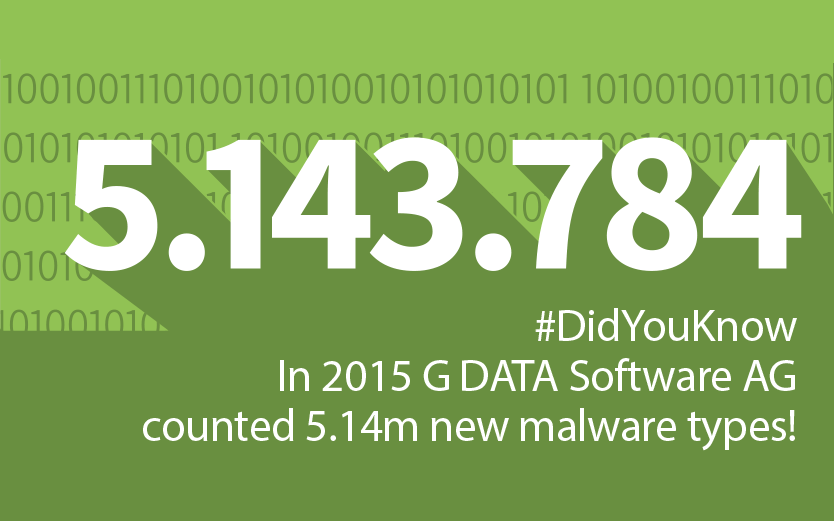
For decades spyware has been stealing personal data from infected PCs. Hundreds of data breaches with almost 2 billion records were stolen [https://haveibeenpwned.com/PwnedWebsites]. Data breaches will continue in 2017 with a continued attention to passwords and credit card data. But addresses, and contact data are interesting, too. There were first cases of spam and phishing mails in 2016 with correct personal information like name, customer ID, address etc. This increases the likelihood of visiting the promoted website or opening the attached file. We will see more of this in 2017 and should be prepared to stop considering correct customer information as a characteristics of trustworthiness.
Adware
Many web sites and download portals, and the majority of popular apps on smartphones are financed by advertisements. There is a huge amount of malware which also takes advantage of the abuse of ads. Unauthorizedly installed browser toolbars, click fraud, replacement of ad banners, and tools for user tracking have a steady position in the cybercrime economy - this is also reflected in G DATA's monthly MII statistics. Without causing a bigger stir, adware has made it to the most prevalent type of malware. We don't see reasons why this should change in 2017.
Smartphones
Smartphones plays a vital role in the lifes of their users and they contain precious personal data. The number of smartphones exceeded the number of PCs long ago. They hold plenty of access data and are used for payment and online banking. In brief, a smartphone is an interesting device for cyber-criminals. Especially if they succeed in exploiting vulnerabilities of the operating system in order to establish drive-by-infections. Then we might see that the well-established business of exploit kits for PCs will move towards smartphones. Regardless of this, the number of malware for Android will continue to rise in 2017.
Targeted attacks against organizations
The myth that targeted attacks are only concerning huge enterprises and are solely carried out by state-driven services is busted. Meanwhile small and medium businesses are exposed to targeted attacks - especially if they have high innovation potential or are dealing with interesting data (e.g. credit cards). Besides groups with national or political interests, profit-driven criminals increase their share. Stealing data, and asking ransom in connection to DDOS attacks or file encryption are seen more frequently. Identifying and defeating targeted attacks will be one of the biggest challenges for security experts in 2017. We hopefully don't see any cyber sabotage attacks with political or extremist background.
Ransomware
The business model ransomware is now established and profitable. Ransomware is available for the standard operating systems (incl. MacOS, Linux, and Android). Several frameworks for ransomware are traded in the cyber crime underground or offered "as-a-service". Whereas at the end of 2015 most of the attacks concerned private users, during 2016 more and more organizations were focused. Attacks that were directed towards typical enterprise infrastructure like web servers and file servers became more frequent. In 2017 ransomware will be a prominent topic. The currently active gangs will enhance their encryption and will at the same time try new blackmailing scenarios. Possible target systems could be TV sets, cars or IoT systems. Industrial control systems (e.g. SCADA) provide a wide range of opportunities that will make victims pay a ransom. What we have seen by now was just the beginning.
Protecting the risk of things
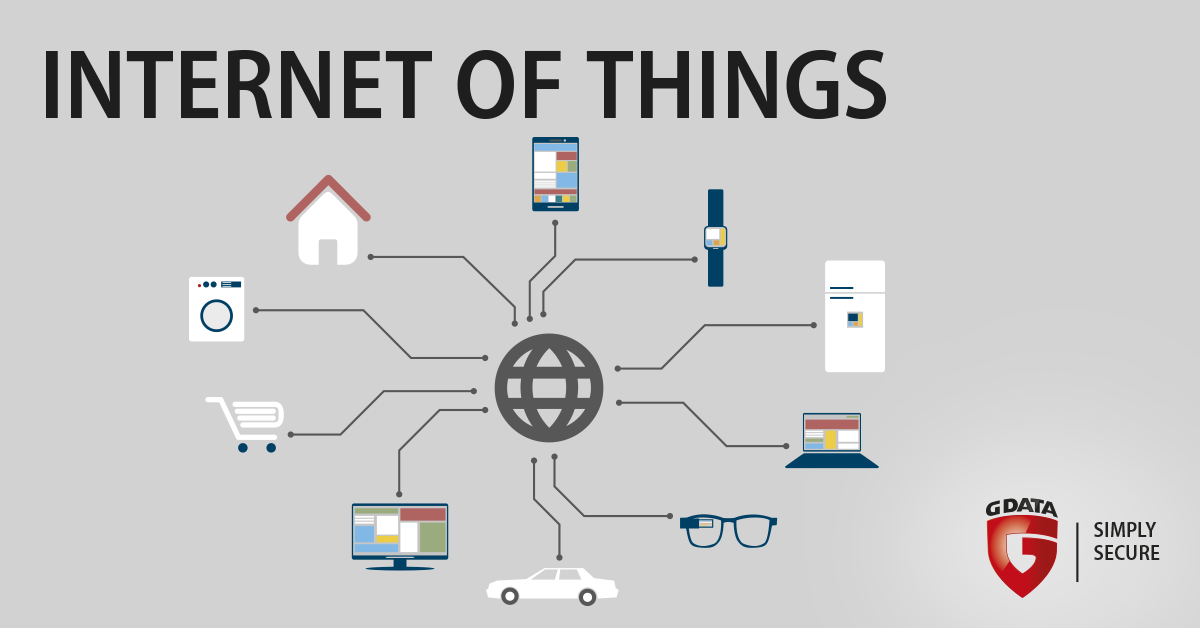
In all areas of our lifes devices with embedded processors get connected. At home this might be fitness trackers, smart TVs, home appliances and home automation. Industrial IoT (IIoT) is dealing with a huge variety of solutions in e.g. logistics, medicine, production, and energy. The public sector too, is testing concepts with intelligent traffic systems in smart cities and uses smart devices in order to optimize administrative processes. Once connected, the devices communicate to each other or with a server (either local or more often somewhere in the Internet). Unfortunately security issues and mitigating potential attacks is often neglected, resulting in a huge number of easily attackable devices (e.g. webcams). We expect that cyber criminals will be very active in this field. 2017 will be the year of faulty and therefore exploited hardware.
Emerging technologies
Augmented reality, virtual agents, intelligent machines and autonomous vehicles are just a few of the new technologies that will find their way into the market in the near future. Cars are already moving computers with way more than 200 processing units. They are exchanging huge amounts of data with servers in the Internet, monitor the situation in traffic, warn each other in case of congestion and are supposed to negotiate the speed with the city's traffic control system. As these systems do not have a wide user base it is very unlikely that cyber criminals will create attack scenarios. Nonetheless, this filed is observed by security researchers in universities and startups. Even if there is no criminal background, we will read about the security gaps that are revealed.
No matter what, no matter how. With our products and services we are prepared to protect the PCs, smartphones and networks of our customers. We wish you a merry Christmas and a good start in the new year.