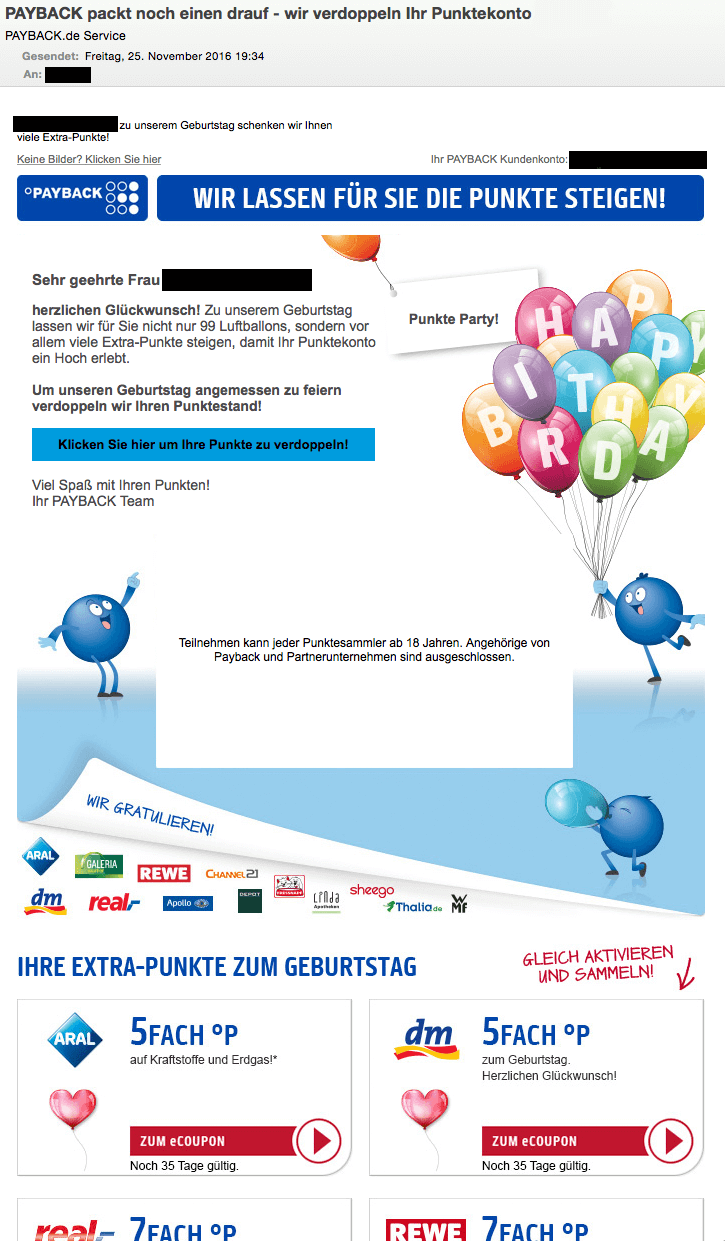
This is what the phishing emails look like
On their website, Payback admits that the emails from the current spam campaign "are well-made, unfortunately". We fully agree with this statement. A look at the sender name could easily fool the reader, because it looks legitimate. It reads "Payback.de Service". On the other hand, legitimate messages from Payback only use "Payback Service" as the sender name. You can find more details on this in the section "Fraud Attempt Indicators". Furthermore, the recipient is addressed correctly. The name is in line with actual data, as is the email address under "Your Payback Account". Save for a few exceptions, the email looks identical to genuine messages from Payback. There are very few indicators for things that are not quite alright and they are difficult to spot:
Fraud Attempt Indicators
- The actual sender domain is not associated with the alleged sender. This is also true for this case.
- Interestingly, two of the analyzed emails showed unusual top level domains: .fr and .club.
- The 15th anniversary of Payback which is referenced in the emails was actually in 2015. The "birthday promotion" is expired as Payback is now 16 years old.
- The email text refers to doubling your points, whereas a legitimate email would rather choose a different wording such as "Secure your opportunity to receive double points".
- The font around the Call To Action button is off and differs from the rest of the email.
- The URLs behind the buttons have nothing to do with the respective loyalty program
- Payback themselves have shown in a spam email which they have archived that sometimes 'seasonal promotions' are completely misplaced by attackers, such as a 'Summer Promotion' which is sent in November.
The phishing websites
The two emails direct the reader to two different websites. We admit that the domains are well chosen for the purpose as it is easy to glance over them without suspecting anything:
- paybrack.pw
- paybaecks.pw
At the time of the analysis, both domains were hosted on the same server at BlazingFast LLC, a hosting service in the Ukraine. Both websites are exact lookalikes of the genuine Payback website.
The only differences are on the submission form for login data. Any data entered in there will not be sent to Payback but instead to a server controlled by the attacker: www. loginpage .online
This domain is hosted in the USA. Any domain registration details are hidden. The dedicated server is also associated with BlazingFast LLC. A quick search with popular search engines shows that the company does not have an entirely clean record. One can suspect that the attackers are carrying out their phishing activities on hacked webservers. The first domain we mentioned actually hosts the website of a Brazilian vendor for aircon units. The web presence has also been been abused before and is also known for its connection with other phishing attacks (e.g. against customers of a Brazilian bank).
What are the dangers from this type of phishing?
Initially, one might be tempted to shrug it off because, after all, those are just virtual points, so nothing is really lost when something happens to those. This is bad advice, though, because behind this seemingly insignificant account is real information which can even be turned into money.
- The makers of a loyalty or coupon program need personal data. For one, to send out rewards and also in order to keep the business model working. Apart from full names, those data sets also contain date of birth, your home address and even phone numbers or bank details. All this data can be accessed by the phishers and either be used by them or sold on for money.
- Attackers can raid rewards accounts themselves and either acquire any non-cash bonuses, transfer bonus points to other loyalty programs or they can cash out and get 'real' money.
Tips & Tricks to avoid being phished
- If you have not done so already, configure your Payback or other loyalty/couponing program account to accept a user name & password instead of things like your post code and birthday. Those are too easy to find out for an attacker.
- Make a conscious decision whether or not you really need the loyalty program's regular newsletter. If you have opted not to receive any newsletters, the sudden appearance of a supposed newsletter might give away an attempt to trick you into giving up your data.
- Be wary of promotions or offers that seem too good to be true, even if there are lots of raffles, promotions and other special campaigns around Christmas.