The new attack
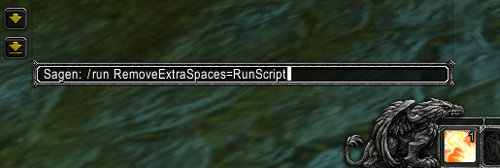
Imagine the following situation: an in-game character that appears to be a member of a popular guild approaches your in-game character and promises to share some cool items, such as rare mounts (animals that you can ride on and which improve your traveling speed), weapons, etc. Most probably, the attacker does not have neither those items nor a valid code for them. Subsequently, the victim does not receive any valid code and no item at all. The trap: the attacker manages to persuade players to enter one single command line into the chat window:
/run RemoveExtraSpaces=RunScript
The WoW interface (e.g. action bar, chat and other graphical elements… everything that is 2D) and also the add-ons (e.g. improvements to the interface) are written in Lua script language. Both sides of the equation, RemoveExtraSpaces and also RunScript are legitimate functions and part of the WoW Lua API. But, feeding your chat window with this single line of code changes the behavior of the WoW interface.
What does this command actually do?
- /run is a command to interpret the following text as a Lua script
- RemoveExtraSpaces is a built-in function which removes unnecessary spaces from text
- RunScript is a function that executes text as Lua code (similar to the /run command)
Why is this a threat?
The function RemoveExtraSpaces is called on every new chat message a player receives. The command mentioned above replaces the RemoveExtraSpaces function with the RunScript function, which is called hooking in software development. Once the original function is overwritten, every new chat message is interpreted as Lua code and immediately executed. The scenario is as follows.
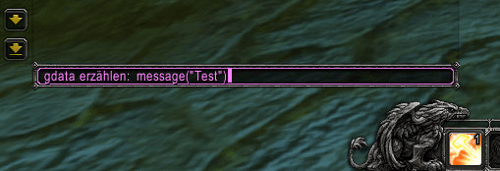
The unaware player enters the given command line into his own chat window, because the foreign in-game character sounded very convincing when he said something like “enter this code and magical things will happen”. Instead of earning some magic items, the player turned himself into the victim:
What we have shown above, is a rather harmless example for this misuse, a Proof of Concept (PoC). But actually, it means that an attacker can now remotely control the victim’s interface. This is very similar to behavior usual Trojan horses show on computers – they pose as something useful and then unfold their malicious behavior. In the real world case, instead of creating a message box with the text “Test”, the attackers run a different script which we’ll explain in the following section.
Temporary persistence and hidden commands
After the victim opened the backdoor to his interface, the attacker sends the following chat message:

In case the command line has been executed, the message seen above won’t be visible to the victim but would be executed immediately. The fact that the chat function does not work anymore, could look suspicious to the victim and maybe even make him restart the game. We suspect that the attacker acts rather quickly to “solve this problem” by sending the command shown above, which establishes a new communication channel, and then most probably re-enables the chat function for the victim.
To understand the intention of this code one needs to know that WoW add-ons have the possibility to communicate via a hidden channel (locally and remotely). This channel is established via the use of “CHAT_MSG_ADDON” events.

The script creates a frame (line 2; z) to which one can set different properties. The script registers for the event CHAT_MSG_ADDON with a specific prefix (line 6 and 25). Only the one who knows the chosen prefix is now able to secretly control the hijacked interface of the victim. This is comparable to a password for a backdoor.
Every time the hijacked interface receives a CHAT_MSG_ADDON event with the given secret prefix, the code will be executed silently instead of being visible to the victim.
Conclusion: As long as the attacker does not want you to see the actions he does to your account, he won’t show you what is going on!
Even though we are talking about add-ons that can communicate via a hidden channel, an attacked player does not need to have any add-ons installed for the attack to work.This is a new development regarding WoW in-game attacks.
What is the harm that can be done?
As the attacker has full access to the victim’s interface, he can check where the victim’s in-game character is currently located on the virtual map to approach him in-game. An attacker usually would not have the chance to know such detailed information about other players.
In WoW, players have the possibility to trade items among each other. For this, the two characters need to be in physical proximity and can then exchange items. If the attacker knows the victim’s character’s location and is within range of the victim’s in-game character, he can now remotely open a trade window, add items and/or gold on the victim’s side and hit the “Accept Trade” button. He can virtually rob the victim.
Our scenario described a social engineering attack paired with a technical attack. Manipulated clients might be misused to send convincing chat messages to other players, e.g. guild members, friends, etc., to manipulate even more in-game characters with this simple but effective script. As we all know, messages from friends and colleagues are considered trustworthy.
How can I protect myself?
As simple as it sounds: Do not enter the script code into your chat window! Question each and every request to type in any message into your chat window.
In the given example, we talked about an attacking in-game character who belonged to a popular guild. Well, he posed as a member of such a popular guild, but he actually was not. He chose a well-known guild and copied their name, substituting the small “L”s in their name for capital “I”s. You might already be familiar with such typo squatting techniques from phishing attacks.
Furthermore, be careful when downloading add-ons from third parties: use trustworthy and popular websites, keep your add-ons up-to-date. It is conceivable that some might add the line of code in question to their add-ons and therefore use the extras as a kind of vehicle for the attack. A similar problem was seen in 2014 when the so-called “ElvUI Backdoor” was discovered in an add-on.

The glitch itself can only be fixed by Blizzard. They have to make sure that overwriting such a special function becomes impossible. During the creation of this article, Blizzard has released a pre-release for the upcoming add-on “Legion”, yesterday. They reacted to the script attacks and have implemented a warning message after the input of a script, but before it is executed:
Choosing “Yes” disables the message permanently, even a restart does not bring it back – the question did not pop-up again, yet. To re-activate it, one has to manually delete one line of code in the configuration… really only this one line:
Code that needs to be deleted: SET AllowDangerousScripts "1"
File: config-cache.wtf
Path: World of Warcraft\WTF\Account\<ACCOUNTNAME>\