The screen, which is officially known as a stop error, already changed during the switch from Windows 7 to Windows 8. The blue and white text wasteland was reduced to just a few lines of information, flanked by a sad, grim-looking ASCII emoticon. The most relevant information – an error code – was now displayed more prominently so that users and support services had a basis for looking into the cause of the problem:
Since the appearance of preview build 14316, the Windows 10 Insider Community has been reporting that the “BSOD” has changed again. The update, due to be rolled out to all Windows 10 users this summer, provides a QR code on the error page as an apparently new feature. According to the latest information, the QR code takes the user to the URL, which is displayed next to it. The dedicated error code can then be searched for on this landing page:

Benefits and drawbacks of this feature at a glance:
| Benefits | Drawbacks |
| You do not need to tediously search for or type in the URL for the error search page on a second device. | The error code still has to be manually entered into the preview display. The QR code does not take you directly to the specific error page. |
| You can switch off the automatic computer restart and so save the information. | If the automatic restart is switched off in case of a crash, the display time for the code and the error for reading, scanning and typing is short. |
| The dedicated display of the error code with no text wasteland makes it easier to identify. | Overall analysis of the error can only happen once the system has collated the error information. |
What is the danger now?
Of course, there is no acute risk to the PC from the original “blue screen of death”, however there is to the blood pressure of the user concerned, and then maybe to the PC... ;-)
But joking aside, the following situation is entirely imaginable. Cyber criminals copy the “BSOD”, replace the QR code displayed with their own and then display the manipulated screen to unsuspecting users – on a website or even by way of a simulated computer crash.
If those affected then visit the associated website with their mobile device by scanning the code, they could end up on web pages manipulated with malware. Since Android devices can now become victims of drive-by infections as well, this attack vector has gained new momentum. If we then put ourselves in the position of a company where mobile devices are integrated into the corporate network as active work resources, there are numerous threat scenarios.
A phishing attack might also await the users of the manipulated QR code. The attackers might for example simulate a genuine-looking Microsoft service page and ask for customer data, payment data, logins for Microsoft services or maybe even serial numbers for Windows licences.
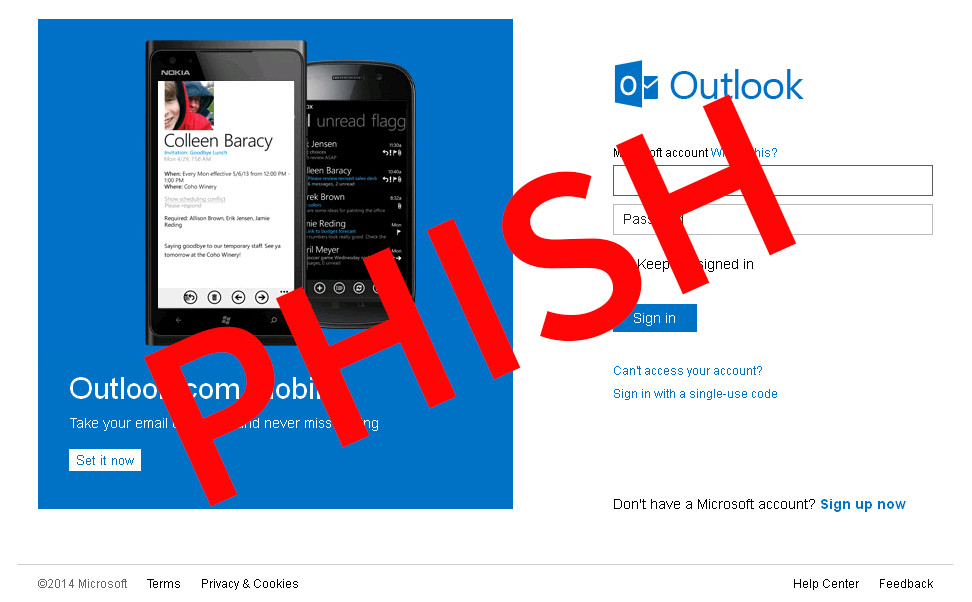
QR codes as a source of risk are nothing new of course. There have been repeated reports for several years of attackers misusing the machine-readable format to harm users of smartphones and tablets. They exploit the fact that, in the majority of cases, the user cannot assess the encoded information until the command behind it has been executed. QR codes can be compared with short URLs, which also do not make their actual purpose obvious.
We recommend...
- Treat QR code with a healthy distrust, as with short links. Ensure that you know the destination of the code before opening it, and ideally investigate it with a powerful scanner to avoid falling into the cyber trap.
- If necessary, switch off the automatic computer restart in the event of a system crash, so you have an opportunity of taking note of the error message.
The anticipated Windows 10 summer update has already made the security headlines. Our Security Evangelist Eddy Willems has addressed it in his article on the question "Ubuntu on Windows 10: Good or Bad?".


