Scam 1: Casino content appearing in websites about other subjects
The attackers add HTML code to a site, enabling terms that are connected to casinos and online gambling to appear in the text of the site. For example, the experts found a manipulated website for a hotel in which clickable words such as "slot machine", "blackjack" or even entire sentences on gambling appear within descriptions of room furnishings. Clicking on one of the links then opens a connection to the online casino website being advertised.
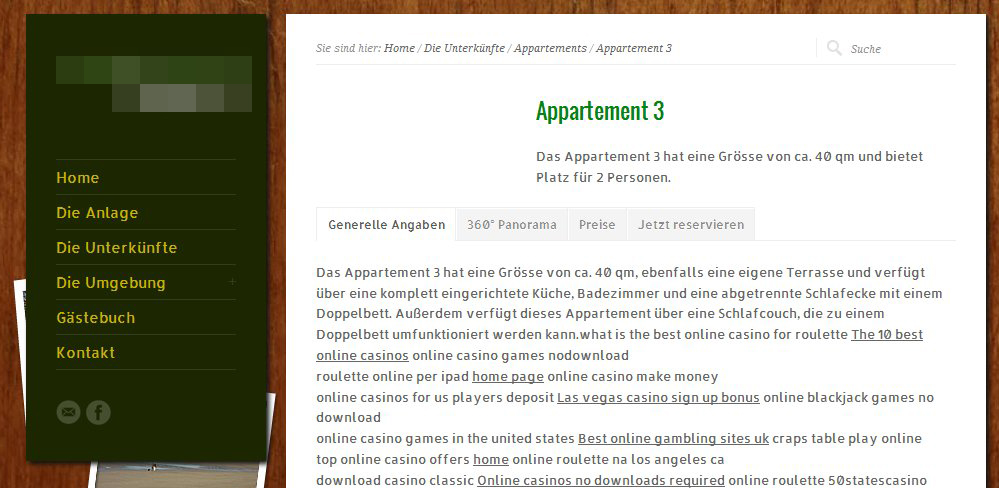
The attackers have a double benefit here: they can hope that the links that they have visibly put there will be clicked on; and they have also affiliated the website they are advertising as a reference site for a website that will ideally be seen by numerous visitors. Search engine crawlers will assess these connections positively as they pass through, as the added text and links look to them as if they belong on the website.
Scam 2: Casino content outside of the visible area of a website
Scam 1 described above indeed brings a double benefit to the attackers, but where this involves a hi-jacked site, their activities can of course be discovered more quickly by a visitor or even the site administrator because of the visible code. One option for potentially preventing discovery is to hide the casino content outside of the visible area of the website. This operation is called "cloaking" – hiding content from human website visitors.
However, the search engine crawlers will of course find this additional code during their search, and the references to the website being advertised in the context of the manipulation are assessed positively.
Scam 3: Casino content hidden by JavaScript in sites
A third scam is to hide the added code using JavaScript elements, a process that can also be thought of as cloaking. Two different approaches are shown in the following screenshot:
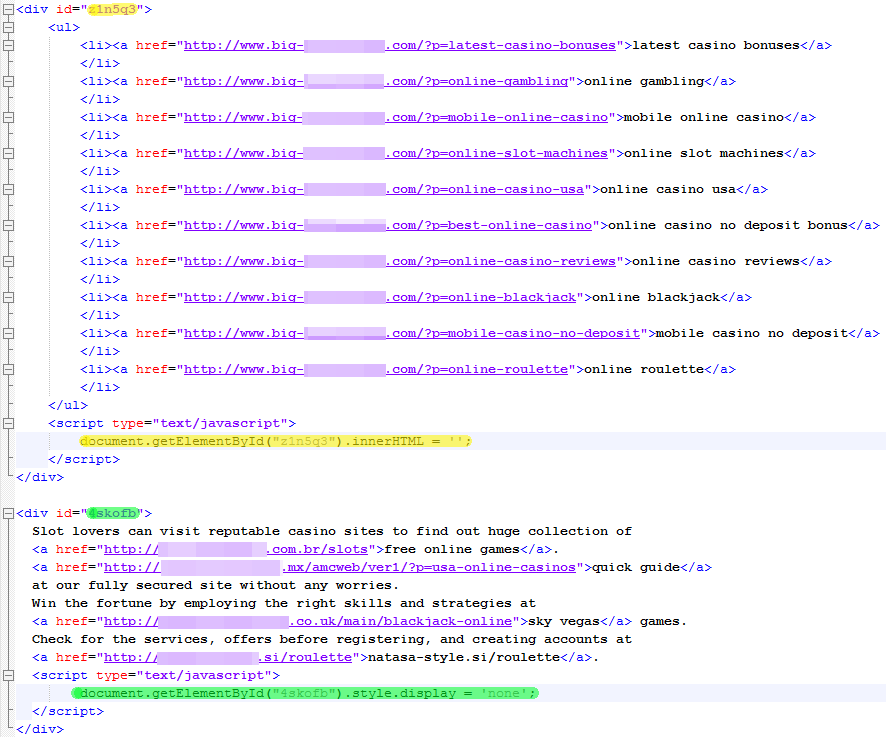
The command document.getElementById("z1n5q3").innerHTML =' ' within the yellow highlighted area ensures that the code is not visible on the website if it is visited with JavaScript activated. The stored code is then deleted by JavaScript. However, if the site is visited without JavaScript functionality enabled, the terms and links ("latest casino bonuses" etc.) are displayed on the site as a list. As search engine crawlers generally do not run JavaScript, they record this information in their site assessment.
In the area highlighted in green,
document.getElementById(„4skofb“).style.display='none' is also used to ensure that visitors to the site with JavaScript functionality enabled do not see the code/text. However, this is not deleted, just hidden. Visitors that do not display active JavaScript content – search engine crawlers – still see the links.
Additional cloaking processes
If the site optimisers are determined to hide the manipulation of websites from human visitors, there are additional cloaking techniques they can use. For example:
- The added text is written in a colour that makes it impossible for the visitor to detect using the naked eye. For example, in Scam 1 the text could have been white instead of grey.
- Not all website visitors are presented with the same website content. The providers decide, on the server side sometimes, whether the content required for optimisation is basically presented to all or just to targeted users.
- This might depend on the visitor's user agent, for example. In this case, the critical element is no longer just the status of the client, as described in Scam 3, but also the server used even before the data is sent to the client.
- Or it might depend on the referrer, for example. If a visitor comes to the website from a certain previous site, he will be supplied with related content. If he comes to the site in question from a different site, he does not see this.
A speck of dust in the microcosmos of site optimisation
The examples given above are a small excerpt of things that a website visitor might come across while surfing. However, the business operating around these functions is highly complex and cannot be described superficially or in brief.
For example, entire SEO networks are set up from new, hi-jacked websites or even recently expired domain ownerships and networked together to promote a specific subject such as online casinos. Links are strategically placed within the network and on the sites being promoted to increase the visibility of sites. The quantity of websites involved here can reach into the thousands and the websites can play various roles within the network.
Another difference to note is whether a campaign involves legitimate search engine optimisation, or a fraudulent version known as black hat SEO. Optimisation is called black hat SEO if it infringes search engine providers' guidelines. The popular provider Google names cloaking and doorway pages as techniques to be avoided in its quality guidelines.
Obviously the hacking of websites is also regarded as an infringement. Naturally, search engine providers' website crawlers are optimised to detect tricks and manipulation better; nevertheless, the scams mentioned continue to be in circulation.
---
G DATA CyberDefense AG - Lesen Sie mehr auf:
Geld ist Trumpf und Besucher sind Geld
