The main part: a Chrome extension
It all starts with an EXE-file, disguised as Adobe Flash Player Installer (Flashplayer_Update5302.exe). The file is digitally signed and the file information is loaded with fake Adobe Systems Incorporated information. G DATA products detect this file as Win32.Malware.FBook.E
When executed, the EXE-file drops a Google Chrome browser extension onto the computer, called Flash Player, detected as Script.Trojan.Pinc.A. Usually, those extensions can only be installed from the official Google store, but this one, disguising behind the name “Flash Update” manipulates the Google Chrome browser! The EXE-file changes the browser’s state into developer mode, which enables it to install any extension desired, even from non-Google sources. To change into this mode, the binary edits the file C:\Users\%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\Preferences and adds the following data:
"ui": {
"developer_mode": true
}
The activists’ choice, to use a Chrome extension, is not left to chance. Today, Google Chrome is the most popular browser in the world: according to StatCounter.com, Google Chrome is used by 42,4%.
Neither the EXE-file nor the extension is malicious or harmful in the narrow sense. But the extension’s behavior is potentially unwanted and interferes with the user’s private information (see connection to Facebook, drawn later in the text) and his/her right to install and uninstall content at will. The extension does not only install itself, but it also defends itself from uninstalling and debugging. As soon as the affected user tries to manage the browser’s extension by opening chrome://extensions, this tab is closed again immediately. The user just cannot access it. Furthermore, the extension detects if the “Chrome Developer Tools” are currently running. If they are, the extension does not download the commands described below and does not do anything at all.
The extension receives commands
The extension then contacts 3 different social media accounts: two Twitter accounts and one Google+ account. All of them have been reported to the respective companies. Nevertheless, the stats on the Google+ account show almost 13 million (!) visits until Monday, May 19th! The fact that the activists use two different social networks is particularly interesting: even if one of the networks can’t be reached or switches the account, the second one is always active and that means that the malware can still work properly. G DATA has contacted the Google and Twitter staff and has requested the immediate deletion of the accounts involved.

Looking at the accounts, the most important part is the information that is stored within the profile: The string in-between the two #b# sections is the main part of the next URL the extension is ordered to contact. Check out the scheme that is used to build the complete URL:
http:// + string in-between #b# sections + .com + /chrome.php
Alternatively, the .php-paths iexplorer.php or also protected.php are used as well. As a result, the extension contacts the built URL to receive a JavaScript file.
Another social media platform involved: Facebook
The JavaScript’s code is injected into every visited web page but executed only if the affected user visits Facebook. To inject the JavaScript, the extension uses the function chrome.tabs.executeScript(). As soon as the “infected” user logs in to his/her Facebook account, the downloaded JavaScript becomes active and sends a private message to all of the victim’s Facebook friends:
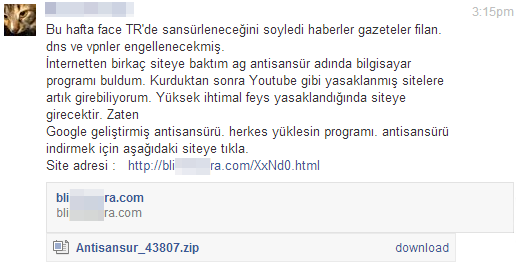
To perform this task, the extension uses Ajax technology and sends queries directly to Facebook, without the need to receive the user’s validation. It simulates the user’s action.
The message is written in Turkish and, according to our translating colleague, it represents a more colloquial language style. Facebook is shortened to “face” or also “feys” and the country Turkey is mentioned by using the official ISO 3166-2 digit abbreviation “TR”. Nevertheless, the text provides interesting information:
------
Newspapers and similar news have reported that Face[book] is going to be censored in Turkey. DNS and VPNs are going to be blocked.
I have checked some websites on the Internet and found a program called “ag antisansür” [network anti-censorship]. After its installation, I was able to access forbidden sites like Youtube. In case feys [Facebook] is going to be blocked, this program can most probably access the site.
“antisansür” was developed by Google. Everyone should install this program. Click the following link to download “antisansür”.
------
The attached ZIP-file contains the EXE-file, or a variant of it, which we have discussed above – this is where the scam has come full circle.
Another anti-censorship advice given
The private Facebook message holds even more: another URL, or, another huge number of URLs. Actually, we have registered more than 15,000 different URLs used in this case. And all of these URLs were hosted on several servers of one single French hoster. The activists gained access to the servers and abused them for their purposes. Each of the involved HTML-files on their server was created on either April 25th or April 26th. The hoster has been informed and has taken care of the situation.
Their only purpose is to redirect the visiting user to one predefined page with a Turkish announcement:
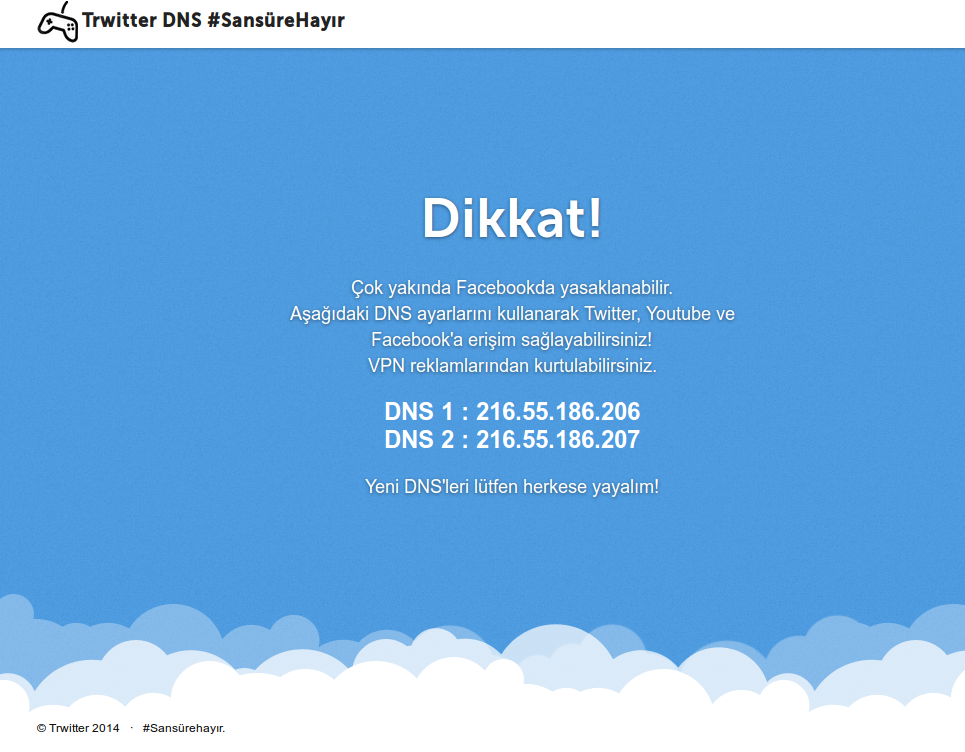
The website’s design and especially the domain name (TRwitter.net) are very similar to the one used by the official Twitter web presence. This is misleading for the visitors who might think that the message is something propagated from the official microblogging service. The message reads as follows:
------
Attention!
Soon, Facebook can be blocked, too.
You can access Twitter, Youtube and Facebook if you use the DNS entries mentioned below.
You can be freed from VPN advertisements.
DNS 1:
DNS 2:
Please share this information about the new DNS with everyone!
------
Information research about the domain shows that it was created on March 24th 2014 with false registrar data (e.g. name = xxx uuuu), 4 days after Erdogan enraged himself about social networks. It is not surprising that the site’s primary traffic arrives from Turkey.
Check out our informative visualization about the activists' scheme -:
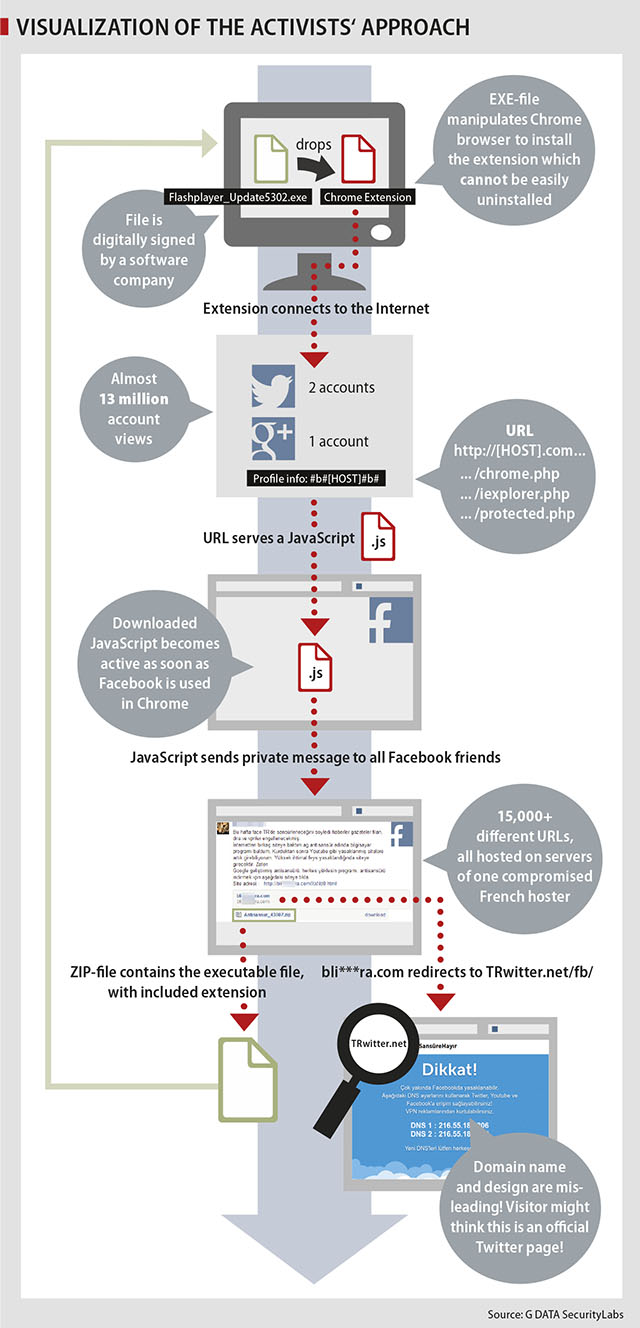
Some useful advice:
- Changing DNS settings to any unknown IP addresses can have far-reaching effects. The owner of the IP can redirect the user’s traffic to any desired target (e.g. fake bank websites or fake social media sites) and can then steal sensitive user data!
- Think twice before you install software from an unknown source, it might harm your computer! If you download software from the Internet, download it from the software vendor’s web page or from download websites with a good reputation only.
- Using an up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must! A spam filter that protects you from unwanted spam emails obviously also makes sense.
