The Israeli white hat hacker who developed the tool clearly states that the tool he provides is not meant to be used for any illegal activity! But, generally, such a warning is not enough to stop attackers from misusing software that has been developed for security purposes such as penetration testing, as G DATA has already reported about. Therefore, G DATA experts explain what is behind this new threat and what users have to be aware of:
The attack requires preparation
The binary used to steal the Windows account credentials can only be used locally on a machine and is perfectly suitable to work in domain network environments, the ones companies and enterprises usually have. End users and their home computers might also lose their Windows credentials, of course. Attackers can set the machine’s host name as requested contact, instead of the Windows domain.
Executing the binary locally requires the attackers to have access to the attacked PC, for example through a legitimate or secretly installed remote administration tool (RAT). Therefore, such an attack is referred to as post-exploitation tool.
The binary phishing for credentials
G DATA products detect the threat discussed as Win32.Trojan-Stealer.KeyLogger.A
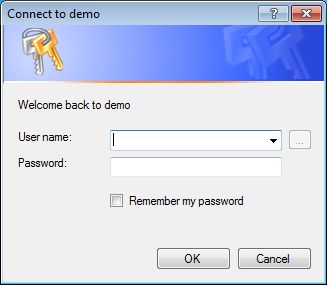
Once the attacker executes the binary, it displays a log-in window which asks the user to enter his/her user credentials for the chosen domain. The current binary only delivers English log-in Windows – not matter what system language you have set!
All inserted credentials from all log-in attempts are stored in a .txt file in the infected user’s temp folder. The log-in window appears again and again, as long as the user credentials are incorrect – the binary uses each set of given credentials to authenticate itself on the domain controller and therefore knows which credentials are correct and which are not.
As soon as the correct log-in information has been provided, the binary has validated the authentication on the domain control server and also has the password information stored as plain text in the .txt document mentioned.
How to identify the threat?
There are only limited possibilities for the human user to spot this threat. In many companies, it is not unusual to enter Windows user credentials to reach certain network resources and depending on the administrator’s settings, such request might appear more or less often during the normal working day.
- If you spot any irregularity regarding the number or cycle of user credential requests, inform your local admin about the irregularities and have your system checked thoroughly.
- In case you are using a non-English system, regard a log-in Window with English text as suspicious and do net enter the requested information! Inform your local admin about the irregularities and have your system checked thoroughly.
- Using an up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must! A spam filter that protects you from unwanted spam emails obviously also makes sense.
