What does it do?
When installed on a system, Beta Bot searches for a list of known security products it is said to target. Upon finding one of those programs installed, the bot starts its attacks as described later in the text. Doing so, it prepares itself to attack the av program by killing processes, disabling registry keys or simply by disabling auto updates. Depending on the type of security product, Beta Bot also tries to circumvent firewalls by injecting certain routines into programs that are usually allowed to pass the firewall, like for example Internet Explorer.
User Access Control (UAC) – it’s all about permissions
On modern Windows operating systems, permissions for users are split into standard (low) and administrator permissions (high/elevated). In contrast to an administrator, a standard user cannot alter critical parts of the system. If a user starts a process, the user’s permissions are inherited to the process. Thus they can also be divided into processes with low and high permissions. By default, only a low set of permissions is granted to each process, because a user has only standard permissions by default. On demand, those permissions can be elevated.
Loosely speaking, all processes can be divided into processes with low and elevated permissions, while the ones with low permissions cannot modify the ones with high permissions, but elevated processes can modify both. Additionally, permissions can also be inherited between processes. Thus, if a process with elevated permissions starts another process, this second process also has elevated permissions.
To prevent malware from harming a system severely, the elevation of permissions from low to high is the most critical step. The decision whether to elevate the permission of a running process is handed over to the user, who is prompted by the system in a UAC dialogue to decide "Yes" or "No" on the request for elevation of permissions. The user also gets some additional info about the program requesting the elevation. Beta Bot targets this interface and tries to exploit the human user with a social engineering trick.
More information about UAC, from Microsoft:
“What is User Account Control?” on Windows 7
“What is User Account Control?” on Windows Vista
Elevation techniques of Beta Bot
For some malware, it is sufficient enough to operate with a low set of permissions, because this still enables the attacker to modify other processes with low permissions and to make itself persistent on a machine. Yet security programs usually run with elevated privileges, since they need to have to access to all resources on the system in order to provide maximum protection. As a consequence of running with elevated permissions, security software is also shielded against manipulations from processes with low permissions. Thus, to attack security software, Beta Bot needs to elevate its permissions. To achieve this goal, two tricks are used to convince the user to provide the process with higher permissions.
The elevated process is not Beta Bot directly, but Microsoft Windows’ cmd.exe , which is triggered by command line arguments to start Beta Bot upon execution. Hence the user is prompted to elevate the permissions of a Windows program, which then inherits its privileges to Beta Bot. Usually, a user is tempted to trust such a prompt, as it seems to come from Microsoft Windows itself and this behavior is exactly what beta Bot wants to exploit.
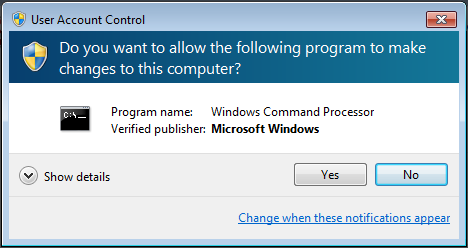
But if we take a closer look at the details, we can spot cmd.exe starting the Beta Bot exe.
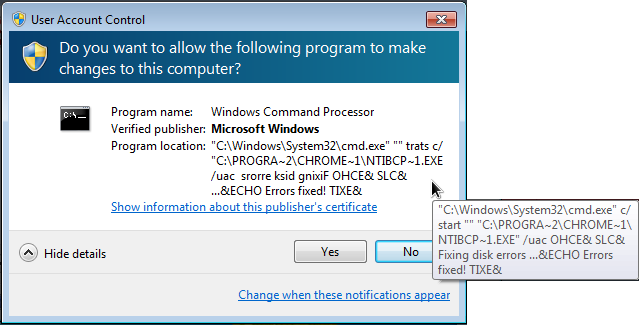
So, the user is tricked into thinking he elevates the permissions of a Windows executable, but actually endangers his system.
Fortunately, many users become suspicious if a UAC dialogue pops up out of nowhere. To address ‘this problem’, Beta Bot presents a justification just before requesting elevated permissions: A fake message about damaged folders in the Documents folder of the current user and a “Critical Disk Error” tries to scare the user into believing important data could get lost. But Beta Bot also provides a solution via two selection options: Both options promise to restore the lost folders. If the user clicks on one of them, the UAC dialogue just described is spawn
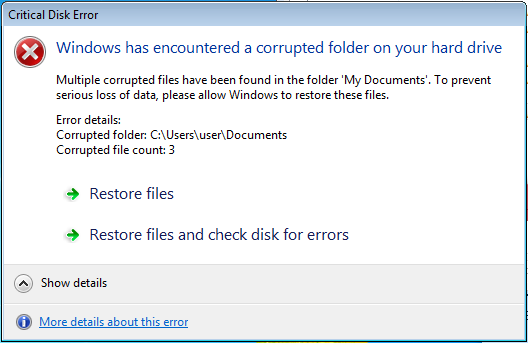
Once the permissions of Beta Bot are elevated, it tries to attack the processes of various security software products, as mentioned in the beginning.
To be able to trick users all around the world, the bot is able create the UAC dialogue and the fake error message in more than 10 languages, e.g. German, English, Spanish, French, Dutch.
Lessons to learn
Malware often uses scare tactics to trick users into providing access to the system. Even in situations that seem critical at first sight, like FakeAV warnings about a massive infection of a system, users should keep calm and verify the given information. In this given Beta Bot case, analyzing the provided details in the system windows can show that cmd.exe actually is about to execute another process.
As described, UAC dialogues are usually used to provide a process with elevated permissions in case the process did not have elevated permissions before. Think about it, would Windows really need to elevate its own process to fix an error on the hard disk? No, it absolutely wouldn‘t.
How to protect against this attack
- Think, before you click! Read the prompts your system shows you and do not click “Yes” or “OK” thoughtlessly. In case of doubt, ask someone for help or try to search the Internet for more information about the prompt in question.
- An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails also makes sense.
- The installed operating system, browser and its components as well as the security solution installed should always be kept up-to-date. Program updates should be installed as soon as possible to close existing security vulnerabilities.
Tip for company networks: International G Data business solutions offer G Data Patch Management as an additional module.
