Which ransomware families are currently most active?

STOP ransomware is currently very active - far more so than any other malware family. According to our findings, almost 70 percent of ransomware infection cases can be attributed to STOP ransomware. Dharma, Phobos, Sodinokibi, and GlobeImposter 2 also continue to be very common, but the difference with STOP ransomware is enormous - they are worlds apart. No end to the wave of attacks is currently in sight. Every day we discover 1 to 3 new variants.
Where does the malware get its name from?
This ransomware has been called STOP/DJVU from the first known variants, which used the file extensions .stop and .djvu. If a ransomware does not include its name in the ransom message, the file extension is very often used as the name, because afflicted users usually search for the extension on the Internet.
What makes STOP ransomware particularly dangerous?
The developers of this malware distribute STOP ransomware as “Ransomware-as-a-Service” (RaaS). This is currently very popular. RaaS means that criminals can configure the malware how they want. Typically, they can specify their own file extensions, the files to encrypt, the amount of the ransom request, and a specific contact email address. STOP ransomware uses new extensions for the encrypted files with each variant. Examples are: .stop, .toec, .leto, .neka, .coot, .nols, and .kuub. The configuration options make identification of the ransomware family more difficult, because there is a risk of confusion with other ransomware that might be using the same file extensions.
Does STOP Ransomware specifically attack companies or private individuals?
In almost all cases private individuals are affected by STOP Ransomware because the main distribution channels are illegal software downloads, cracks for Windows or Microsoft Office products and adware bundles. It is malware for the mass market. This distinguishes it from Ryuk, for example, which usually specifically encrypts corporate networks. Ultimately, the target groups depend on who is deploying the STOP ransomware.
What happens with a ransomware attack?
This depends very much on the attack chain. For example, attackers can get access to systems with insecurely configured RDP by trying out frequently used passwords and usernames. This allows them to penetrate the system and then run ransomware on it.
Criminals use exploit kits, which they can also buy as a service, to define the distribution channels - and thus also the course of the attack - in advance.These can be exploit kits that send infected Word documents via email.STOP ransomware encrypts Office documents, image and video files, as well as PDF files. The malware spares executable files. The attackers are not concerned with encrypting system-related files, but with rendering important personal files unusable - until the users pay a ransom. In addition, STOP ransomware modifies the HOSTS file to block access to bleepingcomputer.com. This is a site where victims of ransomware infections will find knowledgeable help. The site offers things such as decrypters.
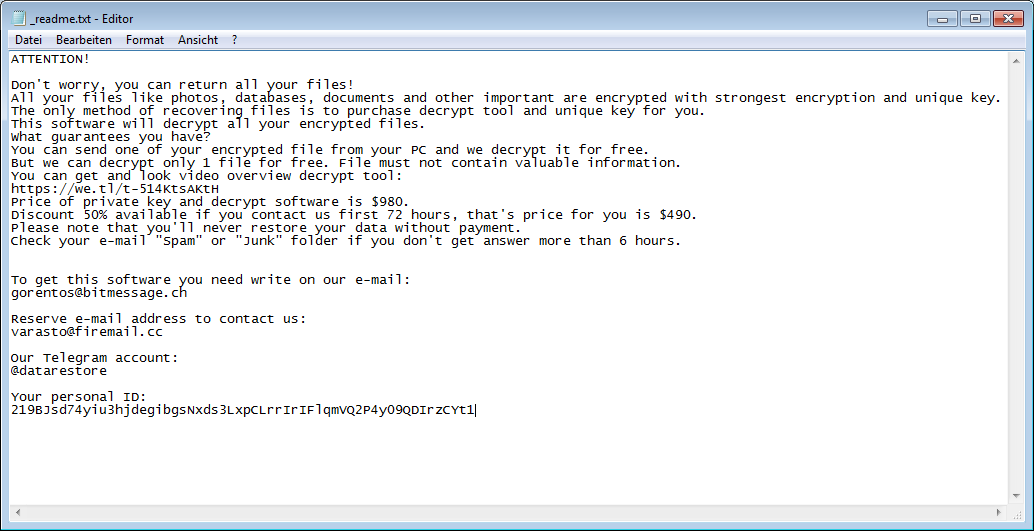
Can infected systems be decoded free of charge?

Decryption is currently only possible in certain cases. Emsisoft offers a decrypter. STOP ransomware contacts a command and control server when it is executed. But if this server is not reachable because the Internet connection is flaky, STOP ransomware uses an offline key. As soon as the key has been extracted from the respective STOP variant by malware analysts, affected systems can be decrypted with Emsisoft's decrypter. The user ID indicates whether decryption is possible without paying anything. If it ends with "t1", the ransomware has used an offline key and the data might be decrypted free of charge by Emsisoft's decrypter.
How can users avoid an attack by STOP ransomware?
Experience shows that our DeepRay technology detects STOP ransomware very well. Corporate and private customers should definitely activate this technology in their software. It will mean that our customers are very well protected.
Otherwise, of course, the well-known security policies apply: Install current security patches on the system. With antivirus software, the signatures should always be up-to-date andregular backups are also important. Of course, they don't prevent an attack, but you don't have to pay a ransom if the data is encrypted. It is important that backups are always stored in an area that is not permanently connected to the network. Otherwise STOP ransomware will encrypt this data as well. And, with STOP ransomware in particular, keep away from software cracks and illegal software downloads.